GCIH Online Practice Questions and Answers
Which of the following types of attack can guess a hashed password?
A. Brute force attack
B. Evasion attack
C. Denial of Service attack
D. Teardrop attack
John works as a Professional Penetration Tester. He has been assigned a project to test the Website security of www.we-are-secure Inc. On the We-are-secure Website login page, he enters ='or''=' as a username and successfully logs on to the user page of the Web site. Now, John asks the we-aresecure Inc. to improve the login page PHP script. Which of the following suggestions can John give to improve the security of the we-are-secure Website login page from the SQL injection attack?
A. Use the escapeshellarg() function
B. Use the session_regenerate_id() function
C. Use the mysql_real_escape_string() function for escaping input
D. Use the escapeshellcmd() function
James works as a Database Administrator for Techsoft Inc. The company has a SQL Server 2005 computer. The computer has a database named Sales. Users complain that the performance of the database has deteriorated. James opens the System Monitor tool and finds that there is an increase in network traffic. What kind of attack might be the cause of the performance deterioration?
A. Denial-of-Service
B. Injection
C. Internal attack
D. Virus
You want to perform passive footprinting against we-are-secure Inc. Web server. Which of the following tools will you use?
A. Nmap
B. Ethereal
C. Ettercap
D. Netcraft
You run the following PHP script:
What is the use of the mysql_real_escape_string() function in the above script. Each correct answer represents a complete solution. (Choose all that apply.)
A. It can be used to mitigate a cross site scripting attack.
B. It can be used as a countermeasure against a SQL injection attack.
C. It escapes all special characters from strings $_POST["name"] and $_POST["password"] except ' and ".
D. It escapes all special characters from strings $_POST["name"] and $_POST["password"].
A search using the term inurl: "ViewerFrame?Mode=" is looking for what?
A. Web accessible devices
B. Searchable SMB shares
C. Default configured HTTP servers
D. Accessible SQL databases
A helpdesk ticket has been escalated to the incident response team. According to the FIRST organization classification guidelines, during which incident response phase should the team document the following information?
Category: Compromised Intellectual Property Criticality: High Sensitivity: Restricted to response team and management
A. Preparation
B. Eradication
C. Lessons Learned
D. Containment
Which of the following accurately describes a "Bot"?
A. Bots normally infect a carrier file and need human interaction to spread from computer to computer
B. Bots are distribution channels that worms and viruses use to spread across the network
C. Bots normally infect a carrier file but need no human interaction to spread from computer to computer
D. Bots are software programs that perform an action on behalf of a human
An attacker wants to intercept their target's network traffic using ARP cache poisoning. How should the attacker setup IP forwarding?
A. On the victim host, directed to the attacker host
B. On whichever network host that is the next hop from the victim, directed to the default gateway
C. On their own host, directed to the default gateway
D. On the default gateway, directed to the attacker host
Analyze the screenshot below. Based on the information, how will you classify this?
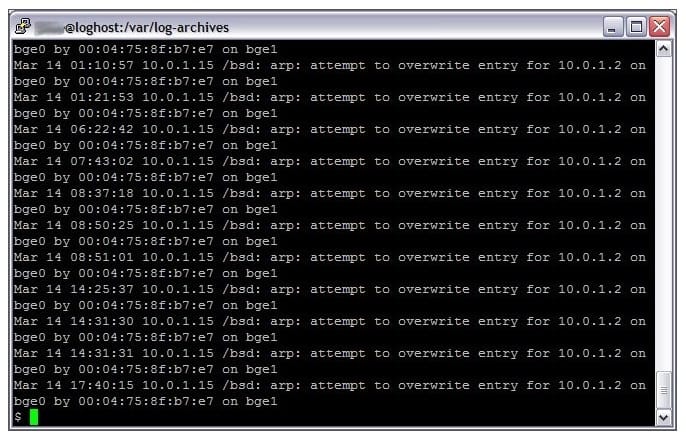
A. An incident. The IP address is being spoofed by another host.
B. An event. The system could have a misconfiguration.
C. An incident. This traffic is always malicious.
D. An event. This traffic is always normal.