GCFR Online Practice Questions and Answers
The Azure URI for the Develop VM is shown below. What will change in the notation when referencing the VM's OS disk?
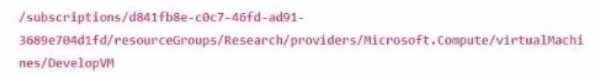
A. Resource Type
B. Provider
C. Resource Group
D. Subscription ID
A threat actor conducts brute force attacks against SSH services to gain Initial access. This attack technique falls under which category of the Google Workspace MITRE ATTandCK matrix?
A. Defense evasion
B. Discovery
C. Credential access
D. Collection
The attack technique "Access Kubelet API" falls under which Mitre ATTandCK tactic?
A. Execution
B. Credential Access
C. Discovery
D. Initial Access
What Pub/Sub component is used to forward GCP logs to their final location?
A. Topic
B. Log Sink
C. Publication
D. Subscription
What can bedetermine about the AVVS Access Key below?
AKIAVNKBKCM4I3VNZIS3
A. The key belongs to a user account
B. The key will only work internally
C. It is a service STS token
D. It is only in use for a single session
Which of the following is the smallest unit of computing hardware in Kubernetes?
A. Cluster
B. Node
C. Container
D. Pod
An organization has optimized their S3 buckets to quickan their data collection across a global infrastructure. Which reflects the bucket URL root?
A. bucketname.s3-accelerate.amazonaws.com
B. bucketname.s3.us-west-2.mazonaws.com
C. s3.us-west-2,amazonaws.com/bucketname
D. bucketname buttcetname.amazonaws.com
Which of the following Windows agents would need to be configured on an Azure VM for an investigator to query Its operating system logs sent to Azure Storage?
A. Azure Monitor
B. Diagnostic Extension
C. Dependency
D. Log Analytics
What method does Google use to alert Gmail account holders that they may be under attack by government sponsored attackers?
A. Message upon successful logon
B. SMS text message
C. Email sent to the user
D. Alert sent to recovery account