GCED Online Practice Questions and Answers
An internal host at IP address 10.10.50.100 is suspected to be communicating with a command and control whenever a user launches browser window. What features and settings of Wireshark should be used to isolate and analyze this network traffic?
A. Filter traffic using ip.src = = 10.10.50.100 and tcp.srcport = = 80, and use Expert Info
B. Filter traffic using ip.src = = 10.10.50.100 and tcp.dstport = = 53, and use Expert Info
C. Filter traffic using ip.src = = 10.10.50.100 and tcp.dstport = = 80, and use Follow TCP stream
D. Filter traffic using ip.src = = 10.10.50.100, and use Follow TCP stream
When attempting to collect data from a suspected system compromise, which of the following should generally be collected first?
A. The network connections and open ports
B. The contents of physical memory
C. The current routing table
D. A list of the running services
Which tasks would a First Responder perform during the Identification phase of Incident Response?
A. Verify the root cause of the incident and apply any missing security patches.
B. Install or reenable host-based firewalls and anti-virus software on suspected systems.
C. Search for sources of data and information that may be valuable in confirming and containing an incident.
D. Disconnect network communications and search for malicious executables or processes.
Which control would BEST help detect a potential insider threat?
A. Mandatory approval process for executive and administrative access requests.
B. Providing the same access to all employees and monitoring sensitive file access.
C. Multiple scheduled log reviews of all employee access levels throughout the year
D. Requiring more than one employee to be trained on each task or job duty.
Although the packet listed below contained malware, it freely passed through a layer 3 switch. Why didn't the switch detect the malware in this packet?
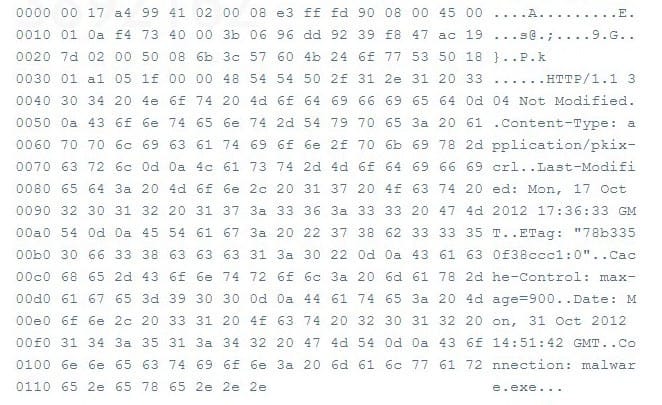
A. The packet was part of a fragmentation attack
B. The data portion of the packet was encrypted
C. The entire packet was corrupted by the malware
D. It didn't look deeply enough into the packet
Which type of attack could be used to obtain IOS router configuration files without a valid user password?
A. ARP cache poisoning
B. CDP sniffing
C. SNMP man in the middle
D. TFTP brute force
Which Windows CLI tool can identify the command-line options being passed to a program at startup?
A. netstat
B. attrib
C. WMIC
D. Tasklist
Which command is the Best choice for creating a forensic backup of a Linux system?
A. Run form a bootable CD: tar cvzf image.tgz /
B. Run from compromised operating system: tar cvzf image.tgz /
C. Run from compromised operating system: dd if=/ dev/hda1 of=/mnt/backup/hda1.img
D. Run from a bootable CD: dd if=/dev/hda1 of=/mnt/backup/hda1.img
Which of the following is the best way to establish and verify the integrity of a file before copying it during an investigation?
A. Write down the file size of the file before and after copying and ensure they match
B. Ensure that the MAC times are identical before and after copying the file
C. Establish the chain of custody with the system description to prove it is the same image
D. Create hash of the file before and after copying the image verifying they are identical
Which of the following is a major problem that attackers often encounter when attempting to develop or use a kernel mode rootkit?
A. Their effectiveness depends on the specific applications used on the target system.
B. They tend to corrupt the kernel of the target system, causing it to crash.
C. They are unstable and are easy to identify after installation
D. They are highly dependent on the target OS.