ECSAv8 Online Practice Questions and Answers
An external intrusion test and analysis identify security weaknesses and strengths of the client's systems and networks as they appear from outside the client's security perimeter, usually from the Internet. The goal of an external intrusion test and analysis is to demonstrate the existence of known vulnerabilities that could be exploited by an external attacker.
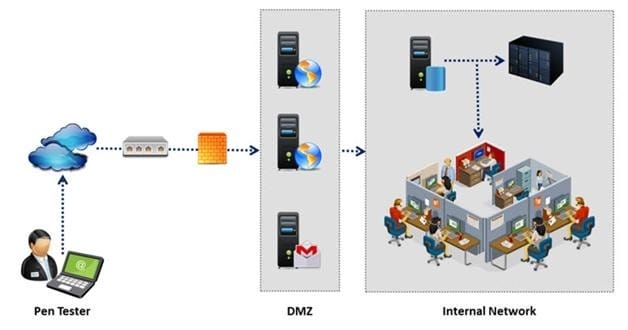
During external penetration testing, which of the following scanning techniques allow you to determine a port's state without making a full connection to the host?
A. XMAS Scan
B. SYN scan
C. FIN Scan
D. NULL Scan
Attackers create secret accounts and gain illegal access to resources using backdoor while bypassing the authentication procedures. Creating a backdoor is a where an attacker obtains remote access to a computer on a network.
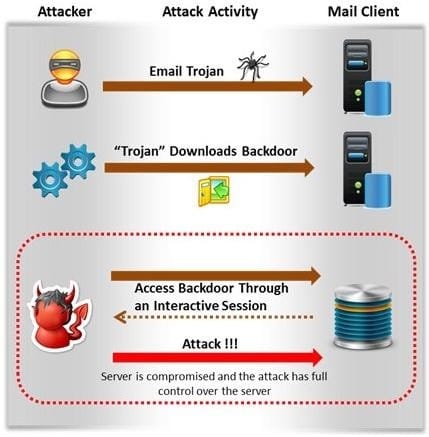
Which of the following techniques do attackers use to create backdoors to covertly gather critical information about a target machine?
A. Internal network mapping to map the internal network of the target machine
B. Port scanning to determine what ports are open or in use on the target machine
C. Sniffing to monitor all the incoming and outgoing network traffic
D. Social engineering and spear phishing attacks to install malicious programs on the target machine
Rule of Engagement (ROE) is the formal permission to conduct a pen-test. It provides top- level guidance for conducting the penetration testing. Various factors are considered while preparing the scope of ROE which clearly explain the limits associated with the security test.
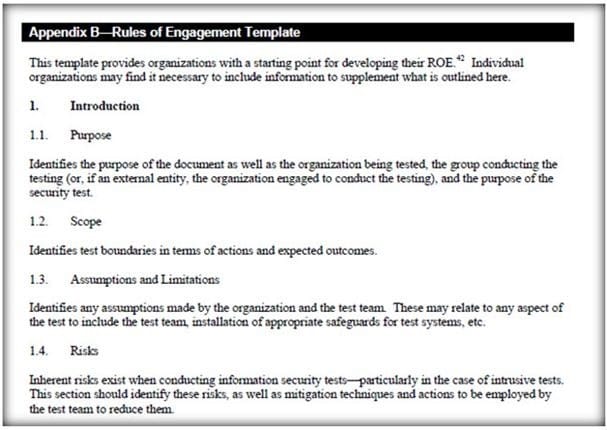
Which of the following factors is NOT considered while preparing the scope of the Rules of Engagment (ROE)?
A. A list of employees in the client organization
B. A list of acceptable testing techniques
C. Specific IP addresses/ranges to be tested
D. Points of contact for the penetration testing team
Which of the following policies helps secure data and protects the privacy of organizational information?
A. Special-Access Policy
B. Document retention Policy
C. Cryptography Policy
D. Personal Security Policy
Why is a legal agreement important to have before launching a penetration test?
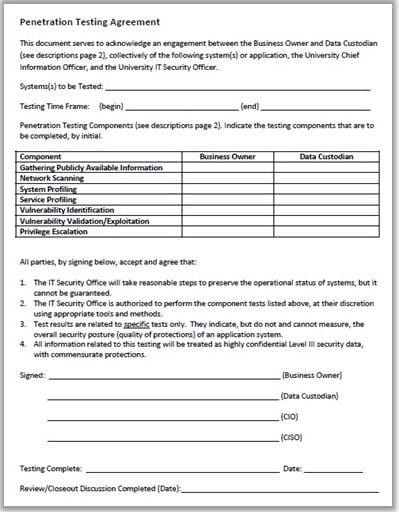
A. Guarantees your consultant fees
B. Allows you to perform a penetration test without the knowledge and consent of the organization's upper management
C. It establishes the legality of the penetration test by documenting the scope of the project and the consent of the company.
D. It is important to ensure that the target organization has implemented mandatory security policies
Which of the following protocol's traffic is captured by using the filter tcp.port==3389 in the Wireshark tool?
A. Reverse Gossip Transport Protocol (RGTP)
B. Real-time Transport Protocol (RTP)
C. Remote Desktop Protocol (RDP)
D. Session Initiation Protocol (SIP)
Which of the following is NOT generally included in a quote for penetration testing services?
A. Type of testing carried out
B. Type of testers involved
C. Budget required
D. Expected timescale required to finish the project
Which of the following is developed to address security concerns on time and reduce the misuse or threat of attacks in an organization?
A. Vulnerabilities checklists
B. Configuration checklists
C. Action Plan
D. Testing Plan
An automated electronic mail message from a mail system which indicates that the user does not exist on that server is called as?
A. SMTP Queue Bouncing
B. SMTP Message Bouncing
C. SMTP Server Bouncing
D. SMTP Mail Bouncing
Which of the following has an offset field that specifies the length of the header and data?
A. IP Header
B. UDP Header
C. ICMP Header
D. TCP Header