EC0-349 Online Practice Questions and Answers
What is the target host IP in the following command?
A. 172.16.28.95
B. 10.10.150.1
C. Firewalk does not scan target hosts
D. This command is using FIN packets, which cannot scan target hosts
What will the following command accomplish? dd if=/dev/xxx of=mbr.backup bs=512 count=1
A. Back up the master boot record
B. Restore the master boot record
C. Mount the master boot record on the first partition of the hard drive
D. Restore the first 512 bytes of the first partition of the hard drive
What encryption technology is used on Blackberry devices Password Keeper?
A. 3DES
B. AES
C. Blowfish
D. RC5
When investigating a wireless attack, what information can be obtained from the DHCP logs?
A. The operating system of the attacker and victim computers
B. IP traffic between the attacker and the victim
C. MAC address of the attacker
D. If any computers on the network are running in promiscuous mode
What feature of Windows is the following command trying to utilize?
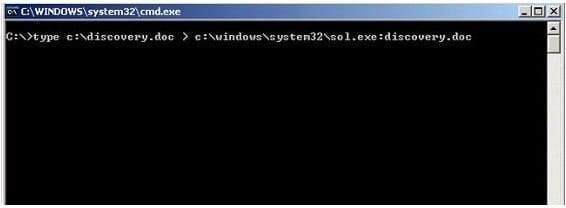
A. White space
B. AFS
C. ADS
D. Slack file
You are using DriveSpy, a forensic tool and want to copy 150 sectors where the starting sector is 1709 on the primary hard drive. Which of the following formats correctly specifies these sectors?
A. 0:1000, 150
B. 0:1709, 150
C. 1:1709, 150
D. 0:1709-1858
Area density refers to:
A. the amount of data per disk
B. the amount of data per partition
C. the amount of data per square inch
D. the amount of data per platter
When performing a forensics analysis, what device is used to prevent the system from recording data on an evidence disk?
A. a write-blocker
B. a protocol analyzer
C. a firewall
D. a disk editor
A state department site was recently attacked and all the servers had their disks erased. The incident response team sealed the area and commenced investigation. During evidence collection they came across a zip disks that did not have the standard labeling on it. The incident team ran the disk on an isolated system and found that the system disk was accidentally erased. They decided to call in the FBI for further investigation. Meanwhile, they short listed possible suspects including three summer interns. Where did the incident team go wrong?
A. They examined the actual evidence on an unrelated system
B. They attempted to implicate personnel without proof
C. They tampered with evidence by using it
D. They called in the FBI without correlating with the fingerprint data
What is the name of the Standard Linux Command that is also available as windows application that can be used to create bit-stream images?
A. mcopy
B. image
C. MD5
D. dd