DES-1423 Online Practice Questions and Answers
DRAG DROP Refer to the Exhibit.
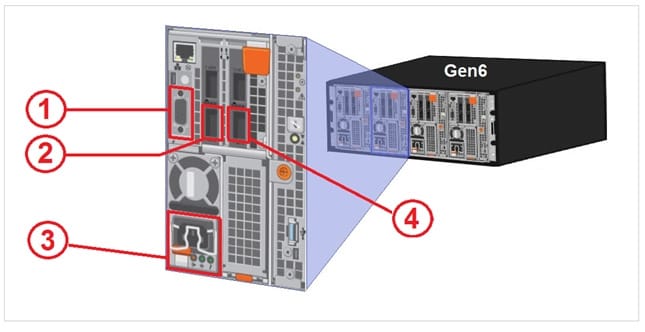
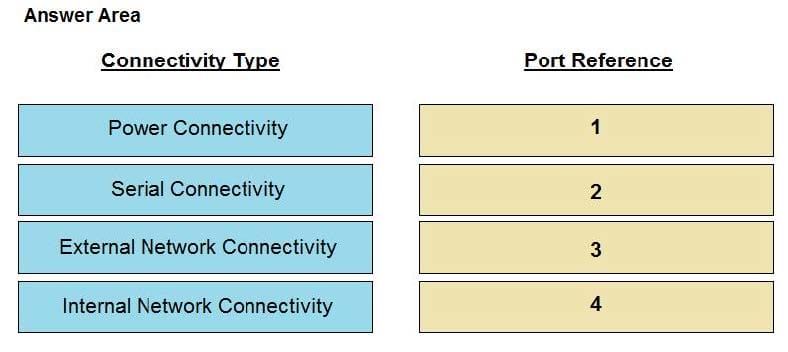
In an Isilon environment, match the connectivity type to the proper numerical port reference shown in the exhibit.
Select and Place:
DRAG DROP
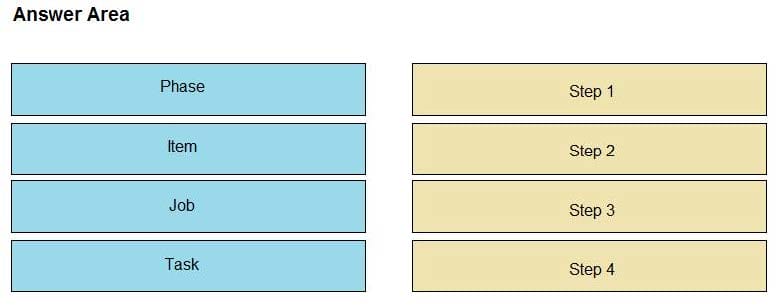
What is the correct hierarchy of the Job elements structure?
Select and Place:
A company has a 4-node Isilon H600 cluster dedicated for a high-performance workflow. The administrator wants to convert their cluster SSD strategy from L3 cache to use the SSDs for metadata acceleration.
What should be considered?
A. Migration of data and metadata from the SSDs to HDDs can take hours.
B. Once enabled, the L3 cache cannot be disabled without support assistance.
C. Converting to use SSDs for metadata acceleration turns off prefetching.
D. Deselecting L3 cache for an SSD strategy has no impact to the workflow.
A company deployed an Isilon cluster that consists of eight nodes connected to a main production subnet by all available 10GB ports. Later, the company decided to implement a disaster recovery solution with a separate replication subnet. During the reconfiguration, one of the 10Gb ports from each of the nodes 1-4 was moved into the new pool and SBR was activated. After activating the replication policies, the administrator noticed that the main production ports on nodes 1-4 reached the bandwidth limit. What is a possible reason for this behavior?
A. Default gateway for the replication subnet has a higher priority value.
B. Default gateway for the replication subnet is not specified.
C. Default gateway for the replication subnet has a lower priority value.
D. Main production ports have a smaller bandwidth limit than replication ports.
When configuring NTP on a 4-node Gen 6 cluster, how many chimer nodes are automatically configured on the cluster?
A. 1
B. 2
C. 3
D. 4
A company has an Isilon cluster that is joined to an Active Directory (AD) domain. Previously, the company replaced their primary NTP server and added new NTP settings to the Isilon cluster. Now the users are experiencing authentication failures.
What is a possible reason for this behavior?
A. Cluster and the AD are configured to use the same NTP server.
B. AD is not configured to synchronize its time from the cluster.
C. SMB time is not configured on the cluster to synchronize with the AD.
D. Time between the NTP and the AD differentiates by more than 5 minutes.
Which data access pattern makes the prefetch caching algorithm to be highly aggressive?
A. Random
B. Parallel
C. Concurrency
D. Streaming
An Isilon administrator wants to create a new SMB share to an existing directory structure. The directory contains migrated production data and has an active NFS export. What will happen if the administrator selects the "Apply Windows default ACLs" option during creation?
A. Windows default ACLs are overwritten by the existing mode bit rights.
B. Existing mode bit rights are overwritten by the Windows default ACLs.
C. Windows default ACLs are merged with the existing mode bit rights.
D. Creation of the SMB share fails due to the existing mode bit rights.
What information is required to enable the LDAP service on an Isilon cluster?
A. Administrator account and password, and LDAP server name and IP address
B. Port number, cluster name, and an LDAP server IP address
C. Base distinguished name, cluster name, and port number
D. Base distinguished name, port number, and at least one LDAP server
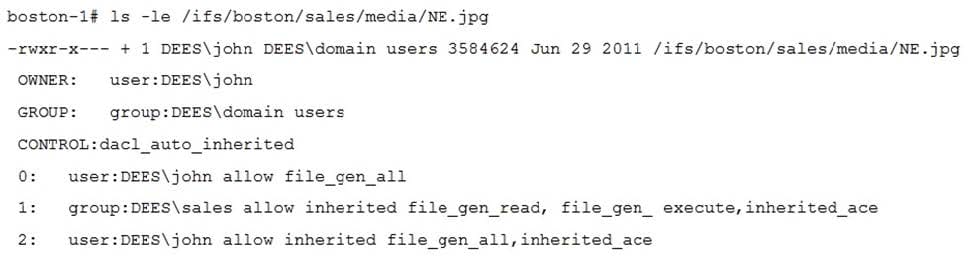
Which access information is represented in the exhibit?
A. Real ACL is applied and group "DEES\domain users" has read access to the file
B. Real ACL is applied and group "DEES\sales" has read access to the file
C. Synthetic ACL is applied and group "DEES\sales" has read access to the file
D. Synthetic ACL is applied and user "DEES\john" has read access to the file