DEA-1TT4 Online Practice Questions and Answers
DRAG DROP
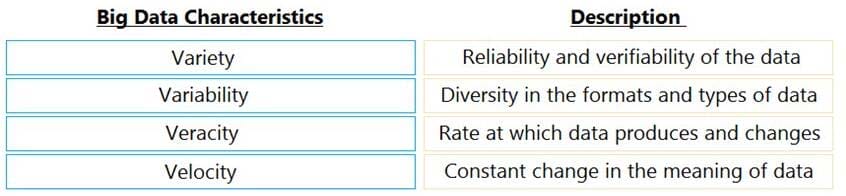
Match the characteristics of big data with their respective descriptions.
Select and Place:
What is an accurate statement about Governance?
A. Restrict access to certain users
B. Ensure removal of security risks
C. Authorize policy-making decisions
D. Demonstrate adherence to polices
An Ethernet switch has eight ports and all ports must be operational for 24 hours, from Monday through Friday. However, a failure of Port4 occurs as follows:
?Monday = 8 PM to 9 PM ?Wednesday 7 PM to 9 PM ?Thursday = 6 AM to 9 AM ?Saturday = 4 PM to 7 PM
What is the MTTR of Port 4?
A. 2 hours
B. 3 hours
C. 28 hours
D. 38 hours
What is a function of the metadata service in an object-based storage device (OSD)?
A. Generates the file system namespace from the file contents.
B. Manages both physical and logical disks on which the user data is stored.
C. Manages the storage space for all remote clients.
D. Maintains the object IDs and file system namespace mappings.
If a company has experienced a passive attack on its IT infrastructure, how is the company's security impacted?
A. Access to services is denied.
B. Availability of data is affected.
C. Information privacy is compromised.
D. Data is altered by an unauthorized user.
A company is planning to perform a cloud-based backup. They want to send their data over a public network to a cloud backup device. Which security control mechanism helps to protect the data from an attacker?
A. Multi-factor authentication
B. Demilitarized zone
C. Data shredding
D. Encryption
Why is it important for organization to deploy intelligent storage systems in their data centers?
A. Reduce the complexity of managing information by creating silos of storage
B. Effectively migrate data from a data center to the cloud at no cost
C. Reduce the amount of data to be replicated, migrated, and backed up
D. Effectively store and manage information across data centers
Which data deduplication method increases the probability of identifying duplicate data even when there is only a minor difference between two documents?
A. Variable-length segment
B. Single-instance
C. File-level
D. Object-level
An Ethernet switch has eight ports and all ports must be operational for 24 hours; from Monday through Friday. However, a failure of Port 5 occurs as follows: Tuesday = 6 AM to 7 AM
Thursday = 5 PM to 9 PM
Friday = 8 AM to 9 AM
What is the MTBF of Port 5?
A. 30 hours
B. 32 hours
C. 40 hours
D. 38 hours
