DCA Online Practice Questions and Answers
Which of the following is NOT backed up when performing a Docker Trusted backup operation?
A. Access control to repos and images
B. Repository metadata
C. Image blobs
D. DTR configurations
Will this action upgrade Docker Engine CE to Docker Engine EE? Solution: Manually download the 'docker-ee' package
A. Yes
B. No
You are troubleshooting a Kubernetes deployment called api, and want to see the events table for this object.
Does this command display it?
Solution: kubectl describe deployment api
A. Yes
B. No
What is the difference between the ADD and COPY dockerfile instructions? (choosen 2)
A. ADD supports compression format handling while COPY does not.
B. COPY supports regular expression handling while ADD does not.
C. COPY supports compression format handling while ADD does not.
D. ADD support remote URL handling while COPY does not.
E. ADD supports regular expression handling while COPY does not.
When seven managers are in a swarm cluster how would they be distributed across three datacenters or availability zones?
A. 5-1-1
B. 3-2-2
C. 3-3-1
D. 4-2-1
The Kubernetes yaml shown below describes a clusterIP service.
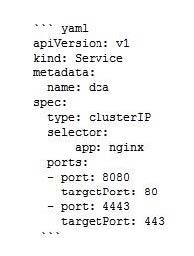
Is this a correct statement about how this service routes requests?
Solution: Traffic sent to the IP of any pod with the label app: nginx on port 8080 will be forwarded to port 80 in that pod.
A. Yes
B. No
Will this command ensure that overlay traffic between service tasks is encrypted? Solution: docker network create -d overlay --secure
A. Yes
B. No
Is this a type of Linux kernel namespace that provides container isolation? Solution: Network
A. Yes
B. No
Will this command mount the host's '/data' directory to the ubuntu container in read-only mode? Solution: 'docker run --volume /data:/mydata:ro ubuntu'
A. Yes
B. No
A user is having problems running Docker. Which of the following will start Docker in debug mode?
A. Set the debug key to true in the 'daemon.json' file.
B. Start the 'dockerd' process manually with the '--logging' flag set to debug
C. Set the logging key to debug in the 'daemon.json' file.
D. Start the 'dockerd' process manually with the '--raw-logs' flag set to debug