DATABRICKS-CERTIFIED-DATA-ANALYST-ASSOCIATE Online Practice Questions and Answers
Which of the following approaches can be used to connect Databricks to Fivetran for data ingestion?
A. Use Workflows to establish a SQL warehouse (formerly known as a SQL endpoint) for Fivetran to interact with
B. Use Delta Live Tables to establish a cluster for Fivetran to interact with
C. Use Partner Connect's automated workflow to establish a cluster for Fivetran to interact with
D. Use Partner Connect's automated workflow to establish a SQL warehouse (formerly known as a SQL endpoint) for Fivetran to interact with
E. Use Workflows to establish a cluster for Fivetran to interact with
Which of the following should data analysts consider when working with personally identifiable information (PII) data?
A. Organization-specific best practices for PII data
B. Legal requirements for the area in which the data was collected
C. None of these considerations
D. Legal requirements for the area in which the analysis is being performed
E. All of these considerations
Which of the following benefits of using Databricks SQL is provided by Data Explorer?
A. It can be used to run UPDATE queries to update any tables in a database.
B. It can be used to view metadata and data, as well as view/change permissions.
C. It can be used to produce dashboards that allow data exploration.
D. It can be used to make visualizations that can be shared with stakeholders.
E. It can be used to connect to third party BI cools.
Which of the following commands can the analyst use to complete the task without producing an error?
A. DROP DATABASE database_name;
B. DROP TABLE database_name.table_name;
C. DELETE TABLE database_name.table_name;
D. DELETE TABLE table_name FROM database_name;
E. DROP TABLE table_name FROM database_name;
A data analyst runs the following command:
INSERT INTO stakeholders.suppliers TABLE stakeholders.new_suppliers;
What is the result of running this command?
A. The suppliers table now contains both the data it had before the command was run and the data from the new_suppliers table, and any duplicate data is deleted.
B. The command fails because it is written incorrectly.
C. The suppliers table now contains both the data it had before the command was run and the data from the new_suppliers table, including any duplicate data.
D. The suppliers table now contains the data from the new_suppliers table, and the new_suppliers table now contains the data from the suppliers table.
E. The suppliers table now contains only the data from the new_suppliers table.
A business analyst has been asked to create a data entity/object called sales_by_employee. It should always stay up-to-date when new data are added to the sales table. The new entity should have the columns sales_person, which will be the name of the employee from the employees table, and sales, which will be all sales for that particular sales person. Both the sales table and the employees table have an employee_id column that is used to identify the sales person.
Which of the following code blocks will accomplish this task?
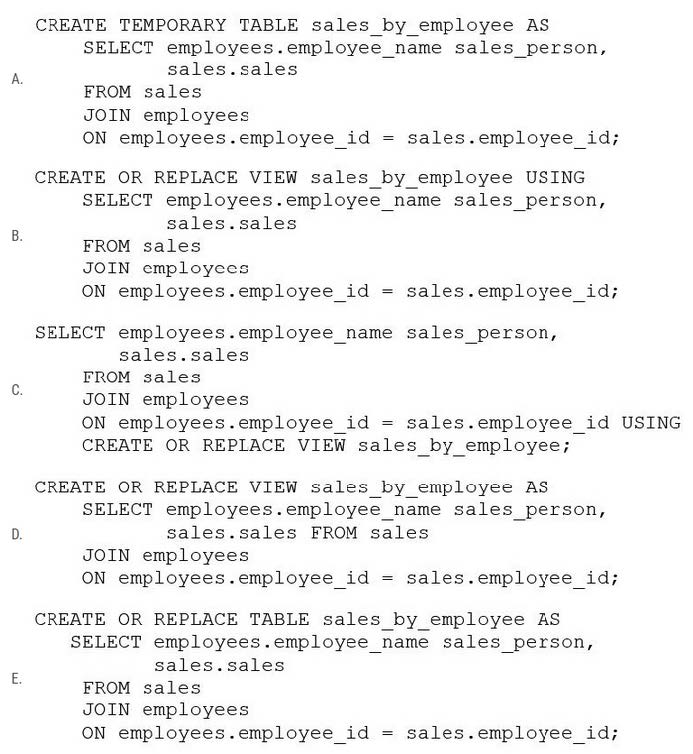
A. Option A
B. Option B
C. Option C
D. Option D
E. Option E
In which of the following situations should a data analyst use higher-order functions?
A. When custom logic needs to be applied to simple, unnested data
B. When custom logic needs to be converted to Python-native code
C. When custom logic needs to be applied at scale to array data objects
D. When built-in functions are taking too long to perform tasks
E. When built-in functions need to run through the Catalyst Optimizer
A data analyst has been asked to provide a list of options on how to share a dashboard with a client. It is a security requirement that the client does not gain access to any other information, resources, or artifacts in the database. Which of the following approaches cannot be used to share the dashboard and meet the security requirement?
A. Download the Dashboard as a PDF and share it with the client.
B. Set a refresh schedule for the dashboard and enter the client's email address in the "Subscribers" box.
C. Take a screenshot of the dashboard and share it with the client.
D. Generate a Personal Access Token that is good for 1 day and share it with the client.
E. Download a PNG file of the visualizations in the dashboard and share them with the client.
A data analyst has been asked to configure an alert for a query that returns the income in the accounts_receivable table for a date range. The date range is configurable using a Date query parameter.
The Alert does not work.
Which of the following describes why the Alert does not work?
A. Alerts don't work with queries that access tables.
B. Queries that return results based on dates cannot be used with Alerts.
C. The wrong query parameter is being used. Alerts only work with Date and Time query parameters.
D. Queries that use query parameters cannot be used with Alerts.
E. The wrong query parameter is being used. Alerts only work with dropdown list query parameters, not dates.
Which of the following statements describes descriptive statistics?
A. A branch of statistics that uses summary statistics to quantitatively describe and summarize data.
B. A branch of statistics that uses a variety of data analysis techniques to infer properties of an underlying distribution of probability.
C. A branch of statistics that uses quantitative variables that must take on a finite or countably infinite set of values.
D. A branch of statistics that uses summary statistics to categorically describe and summarize data.
E. A branch of statistics that uses quantitative variables that must take on an uncountable set of values.