D-ISM-FN-23 Online Practice Questions and Answers
In a data archiving environment, which component scans primary storage to nd the les that are required to archive?
A. Archive stub le
B. Archive agent
C. Archive storage
D. Archive database server
What is an impact of a Denial of Service (DoS) attack?
A. Compromises user accounts and data to malicious insiders
B. Hijacks privileges to compromise data security
C. Prevents legitimate users from accessing IT resources or service
D. Duplicates user credentials to compromise data security
What is a function of a continuous data protection (CDP) appliance?
A. Migrates deduplicated data from the source volume to the target volume during replication
B. Intercepts writes to the production volume and splits each write into two copies
C. Runs data protection software and manages replications within and across data centers
D. Stores all data that has changed from the time the replication session started
Which components comprise a Fibre Channel SAN?
A. TOE HBA Gateways CAT6 cables
B. FC HBA Switches Fiber optic cables
C. FC HBA Gateways Fiber optic cables
D. TOE HBA Switches CAT6 cables
In a software-de ned networking architecture, which layer is responsible for handling data packet forwarding or dropping?
A. Infrastructure
B. Application
C. Control
D. Interface
What is a bene t of using a Scale-Out NAS system vs. general purpose le servers?
A. For high performance and security NAS supports only NFS protocol
B. File system grows dynamically as nodes are added to the NAS cluster
C. For high performance and security NAS supports only CIFS protocol
D. NAS servers are pooled into a cluster of independent NAS nodes
Which layer of modern data center architecture speci es the measures that help an organization mitigate downtime impact due to planned and unplanned outages?
A. Security layer
B. Business continuity layer
C. Application layer
D. Management layer
Under the PaaS model, which elements are managed by the consumer?
A. Applications and Data
B. OS and Runtime
C. Middleware and Networking
D. OS and Virtualization
Which option shows the correct sequence of steps to perform a data recovery operation?
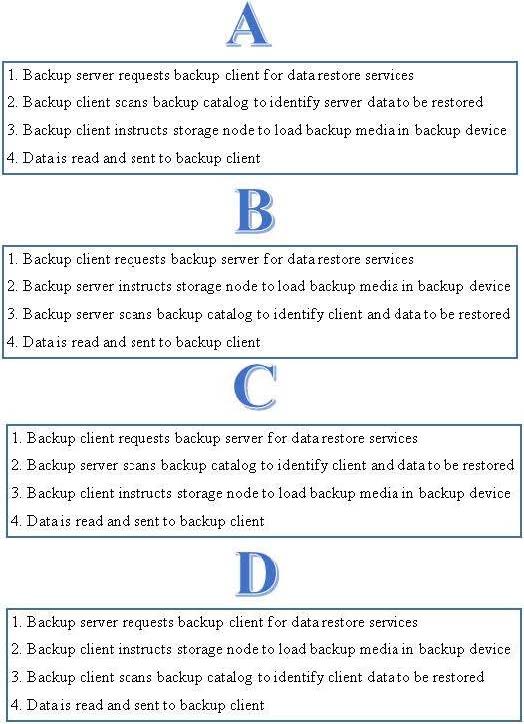
A. A
B. C
C. D
D. B
What method does FCIP use to transport Fibre Channel SAN data?
A. FCIP encapsulates and tunnels FC SAN data over Ethernet networks.
B. FCIP encapsulates and tunnels FC SAN data over IP networks.
C. FCIP splits LAN and FC SAN data and tunnels FC SAN data over Ethernet networks.
D. FCIP separates LAN and FC SAN data and tunnels FC SAN data over IP networks.