CKS Online Practice Questions and Answers
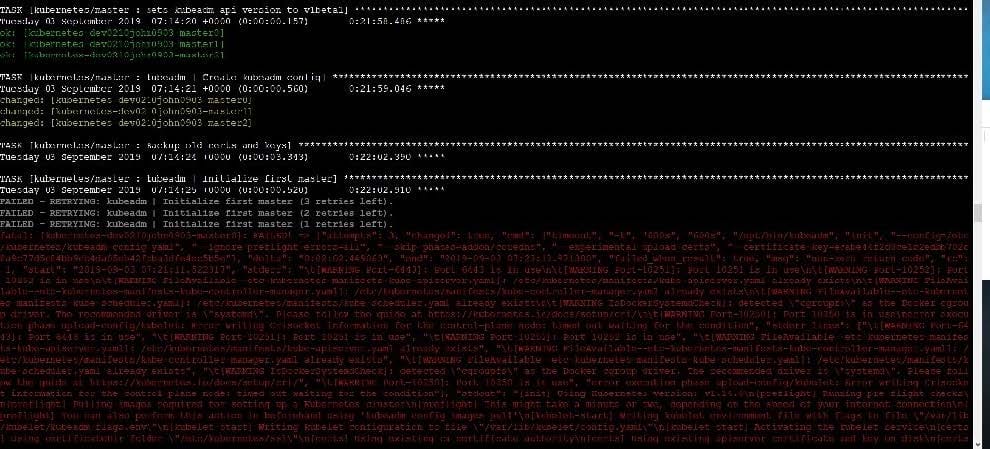
Create a Pod name Nginx-pod inside the namespace testing, Create a service for the Nginx-pod named nginx-svc, using the ingress of your choice, run the ingress on tls, secure port.
A. See explanation below.
B. PlaceHolder
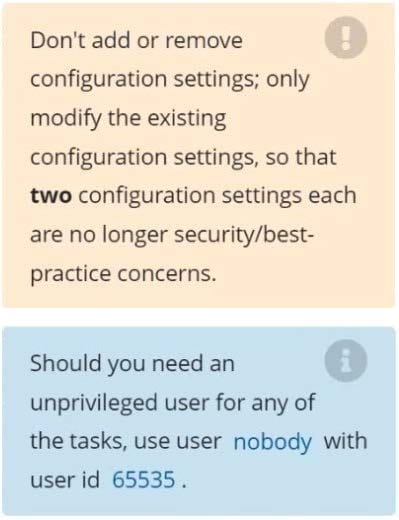
Task Analyze and edit the given Dockerfile /home/candidate/KSSC00301/Docker file (based on the ubuntu:16.04 image), fixing two instructions present in the file that are prominent security/best-practice issues. Analyze and edit the given manifest file /home/candidate/KSSC00301/deployment.yaml, fixing two fields present in the file that are prominent security/best-practice issues.
A. See explanation below.
B. PlaceHolder
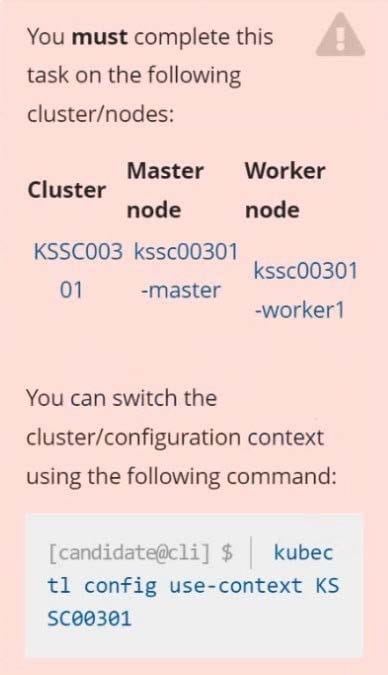
You must complete this task on the following cluster/nodes: Cluster: immutable-cluster
Master node: master1
Worker node: worker1
You can switch the cluster/configuration context using the following command:
[desk@cli] $ kubectl config use-context immutable-cluster
Context: It is best practice to design containers to be stateless and immutable.
Task:
Inspect Pods running in namespace prod and delete any Pod that is either not stateless or not immutable.
Use the following strict interpretation of stateless and immutable:
1.
Pods being able to store data inside containers must be treated as not stateless.
Note: You don't have to worry whether data is actually stored inside containers or not already.
2.
Pods being configured to be privileged in any way must be treated as potentially not stateless or not immutable.
A. See the explanation below
B. PlaceHolder
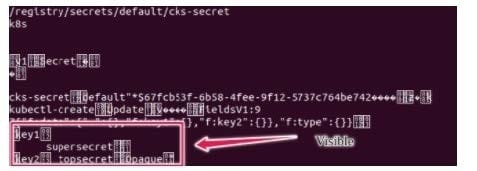
Secrets stored in the etcd is not secure at rest, you can use the etcdctl command utility to find the secret value for e.g:ETCDCTL_API=3 etcdctl get /registry/secrets/default/cks-secret --cacert="ca.crt" -- cert="server.crt" --key="server.key" Output
Using the Encryption Configuration, Create the manifest, which secures the resource secrets using the provider AES-CBC and identity, to encrypt the secret-data at rest and ensure all secrets are encrypted with the new configuration.
A. See explanation below.
B. PlaceHolder
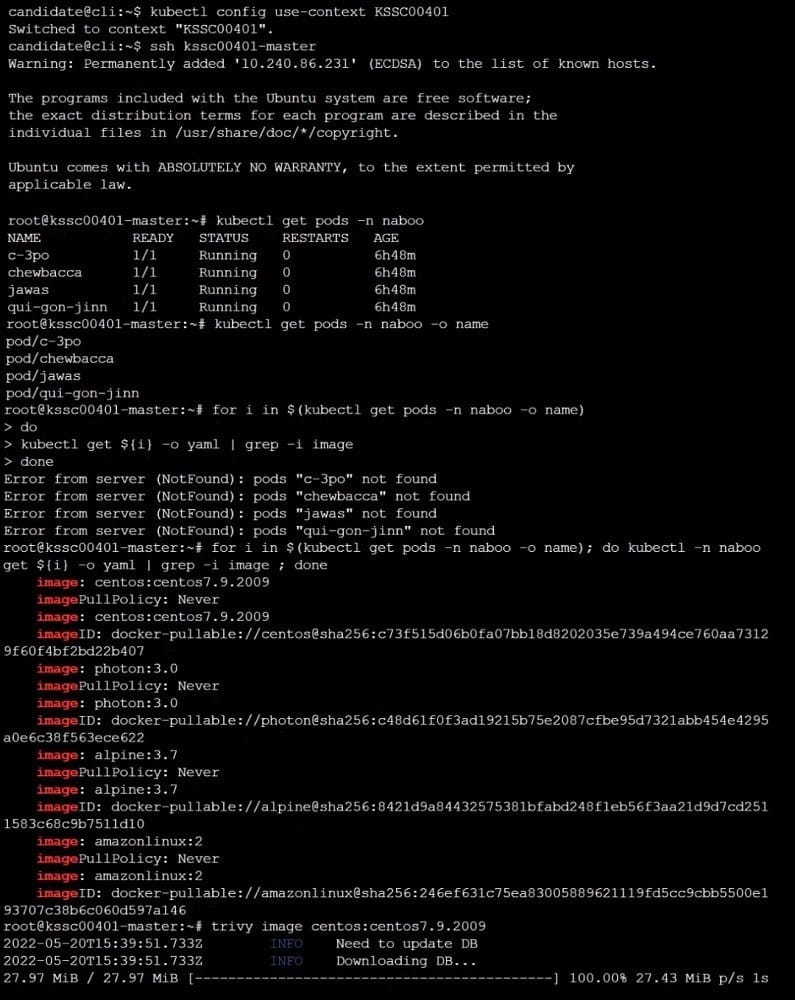
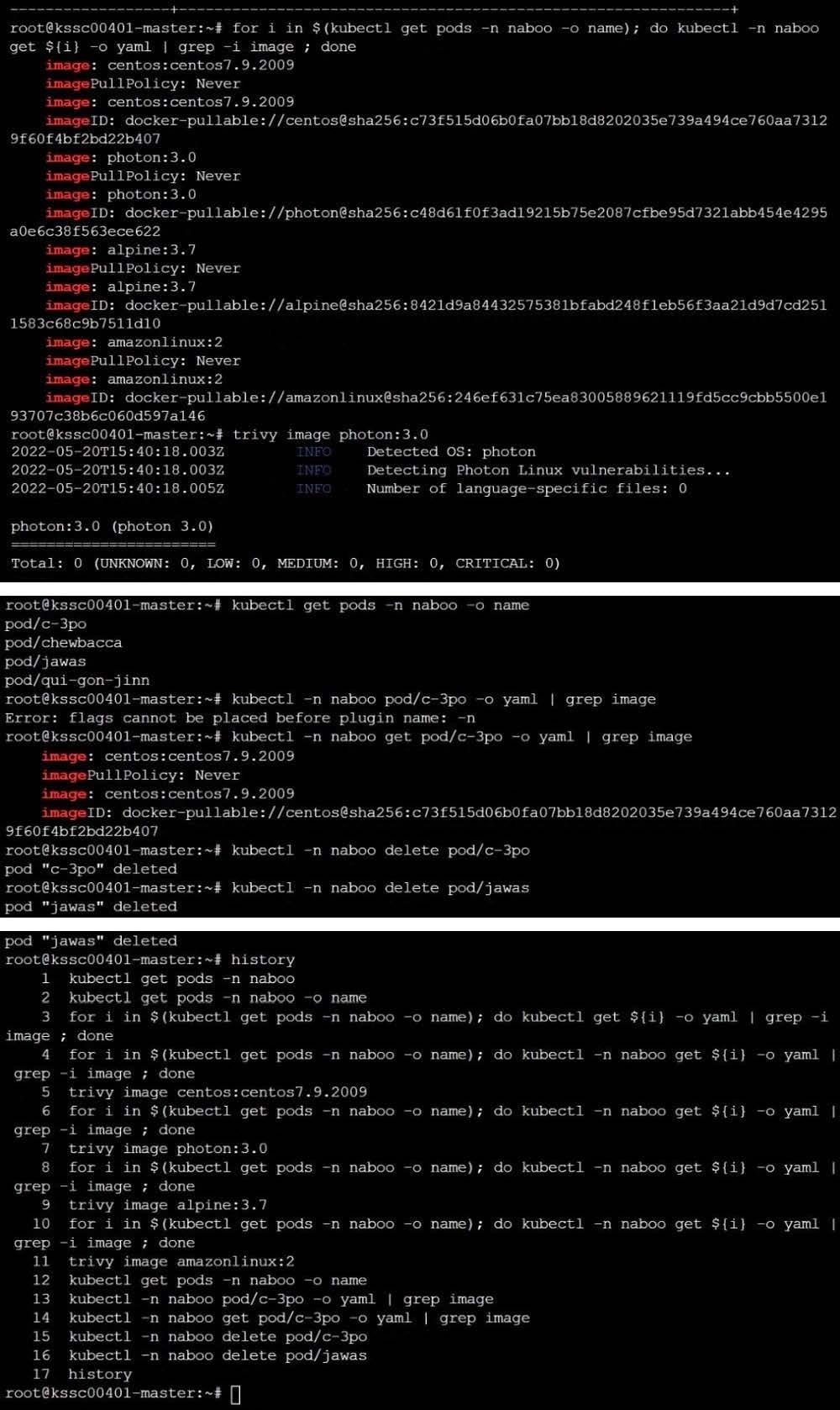
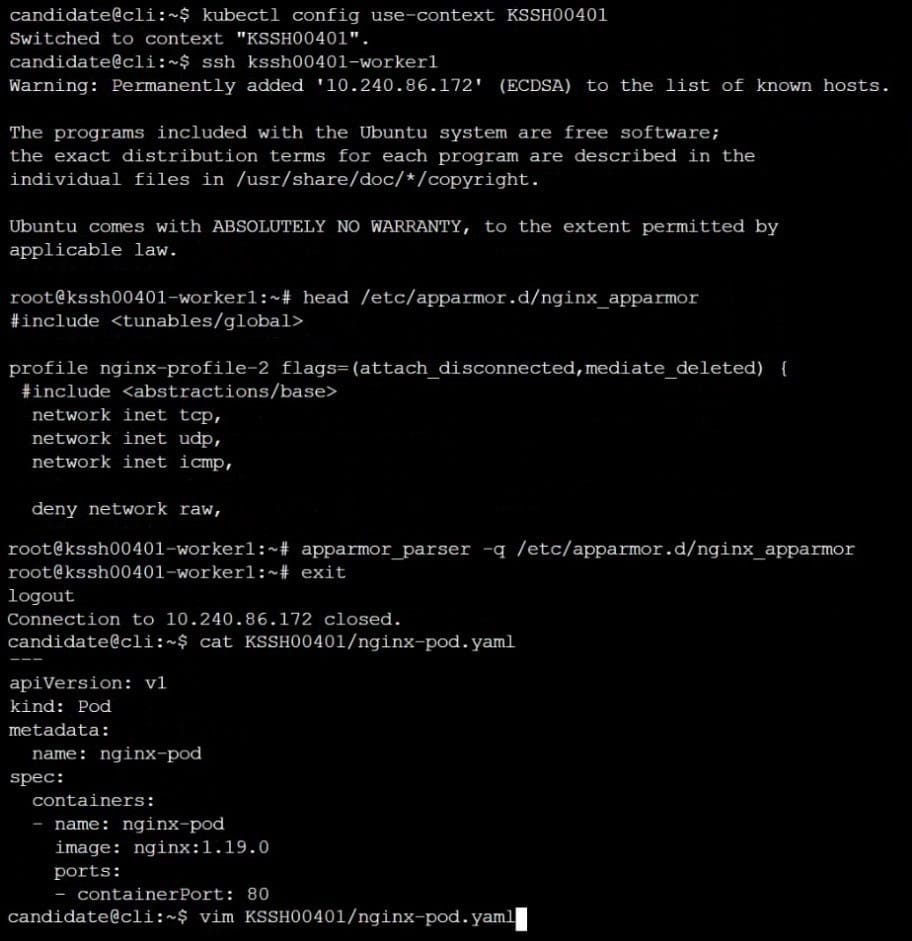
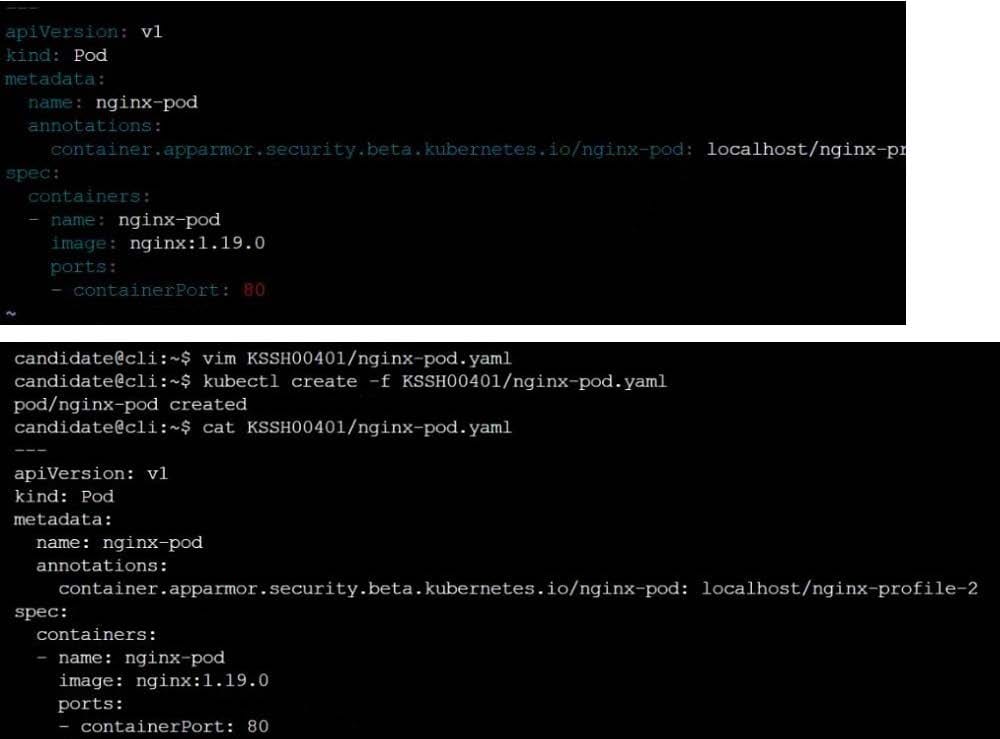
AppArmor is enabled on the cluster's worker node. An AppArmor profile is prepared, but not enforced yet.
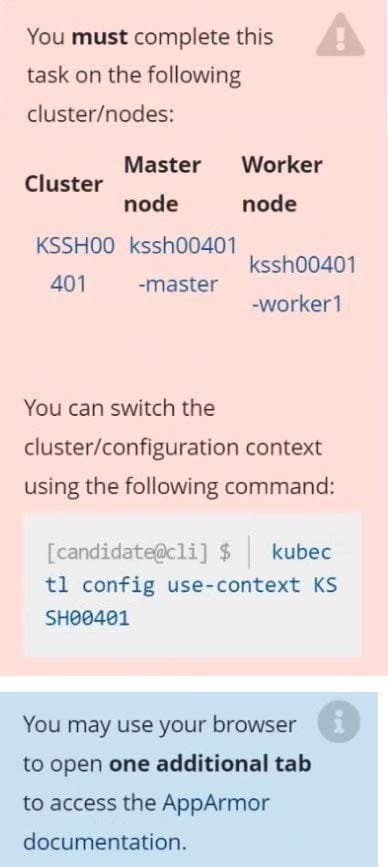
Task
On the cluster's worker node, enforce the prepared AppArmor profile located at /etc/apparmor.d/nginx_apparmor.
Edit the prepared manifest file located at /home/candidate/KSSH00401/nginx-pod.yaml to apply the AppArmor profile.
Finally, apply the manifest file and create the Pod specified in it.
A. See the explanation below
B. PlaceHolder
You can switch the cluster/configuration context using the following command:
[desk@cli] $ kubectl config use-context test-account
Task: Enable audit logs in the cluster.
To do so, enable the log backend, and ensure that:
1.
logs are stored at /var/log/Kubernetes/logs.txt
2.
log files are retained for 5 days
3.
at maximum, a number of 10 old audit log files are retained
A basic policy is provided at /etc/Kubernetes/logpolicy/audit-policy.yaml. It only specifies what not to log.
Note: The base policy is located on the cluster's master node.
Edit and extend the basic policy to log:
1.
Nodes changes at RequestResponse level
2.
The request body of persistentvolumes changes in the namespace frontend
3.
ConfigMap and Secret changes in all namespaces at the Metadata level
Also, add a catch-all rule to log all other requests at the Metadata level Note: Don't forget to apply the modified policy.
A. See the explanation below
B. PlaceHolder
Service is running on port 389 inside the system, find the process-id of the process, and stores the names of all the open-files inside the /candidate/KH77539/files.txt, and also delete the binary.
A. See explanation below.
B. PlaceHolder
CORRECT TEXT Your organization's security policy includes:
1.
ServiceAccounts must not automount API credentials
2.
ServiceAccount names must end in "-sa"
The Pod specified in the manifest file /home/candidate/KSCH00301 /pod-m
nifest.yaml fails to schedule because of an incorrectly specified ServiceAccount.
Complete the following tasks:
Task
1.
Create a new ServiceAccount named frontend-sa in the existing namespace qa. Ensure the ServiceAccount does not automount API credentials.
2.
Using the manifest file at /home/candidate/KSCH00301 /pod-manifest.yaml, create the Pod.
3.
Finally, clean up any unused ServiceAccounts in namespace qa.
A. See the explanation below
B. PlaceHolder
Enable audit logs in the cluster, To Do so, enable the log backend, and ensure that
1.
logs are stored at /var/log/kubernetes/kubernetes-logs.txt.
2.
Log files are retained for 5 days.
3.
at maximum, a number of 10 old audit logs files are retained. Edit and extend the basic policy to log:
1.
Cronjobs changes at RequestResponse
2.
Log the request body of deployments changes in the namespace kube-system.
3.
Log all other resources in core and extensions at the Request level.
4.
Don't log watch requests by the "system:kube-proxy" on endpoints or
A. See explanation below.
B. PlaceHolder
A container image scanner is set up on the cluster.
Given an incomplete configuration in the directory
/etc/kubernetes/confcontrol and a functional container image scanner with HTTPS endpoint https://test-server.local.8081/image_policy
1.
Enable the admission plugin.
2.
Validate the control configuration and change it to implicit deny.
Finally, test the configuration by deploying the pod having the image tag as latest.
A. See explanation below.
B. PlaceHolder