CEH-001 Online Practice Questions and Answers
What type of attack is shown here?
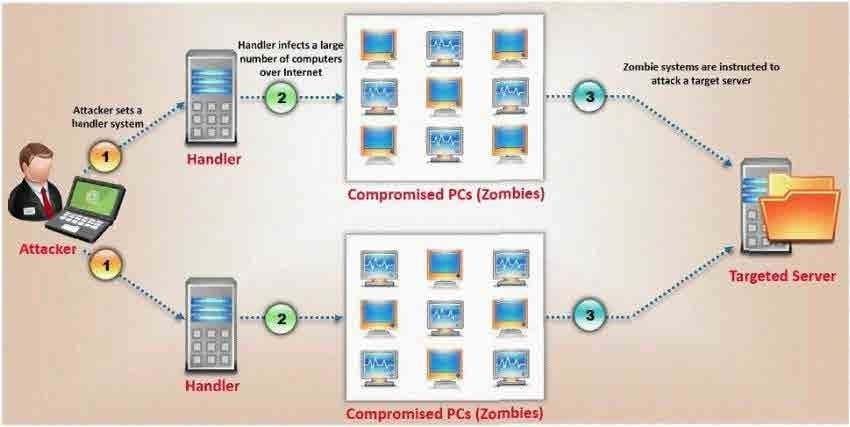
A. Bandwidth exhaust Attack
B. Denial of Service Attack
C. Cluster Service Attack
D. Distributed Denial of Service Attack
During a wireless penetration test, a tester detects an access point using WPA2 encryption. Which of the following attacks should be used to obtain the key?
A. The tester must capture the WPA2 authentication handshake and then crack it.
B. The tester must use the tool inSSIDer to crack it using the ESSID of the network.
C. The tester cannot crack WPA2 because it is in full compliance with the IEEE 802.11i standard.
D. The tester must change the MAC address of the wireless network card and then use the AirTraf tool to obtain the key.
Which tool would be used to collect wireless packet data?
A. NetStumbler
B. John the Ripper
C. Nessus
D. Netcat
Bluetooth uses which digital modulation technique to exchange information between paired devices?
A. PSK (phase-shift keying)
B. FSK (frequency-shift keying)
C. ASK (amplitude-shift keying)
D. QAM (quadrature amplitude modulation)
At a Windows Server command prompt, which command could be used to list the running services?
A. Sc query type= running
B. Sc query \\servername
C. Sc query
D. Sc config
Which of the following ICMP message types are used for destinations unreachables?
A. 0
B. 3
C. 11
D. 13
E. 17
Eric has discovered a fantastic package of tools named Dsniff on the Internet. He has learnt to use these tools in his lab and is now ready for real world exploitation. He was able to effectively intercept communications between the two entities and establish credentials with both sides of the connections. The two remote ends of the communication never notice that Eric is relaying the information between the two.
What would you call this attack?
A. Interceptor
B. Man-in-the-middle
C. ARP Proxy
D. Poisoning Attack
Which tool/utility can help you extract the application layer data from each TCP connection from a log file into separate files?
A. Snort
B. argus
C. TCPflow
D. Tcpdump
What are the differences between SSL and S-HTTP?
A. SSL operates at the network layer and S-HTTP operates at the application layer
B. SSL operates at the application layer and S-HTTP operates at the network layer
C. SSL operates at the transport layer and S-HTTP operates at the application layer
D. SSL operates at the application layer and S-HTTP operates at the transport layer
You have just installed a new Linux file server at your office. This server is going to be used by several individuals in the organization, and unauthorized personnel must not be able to modify any data.
What kind of program can you use to track changes to files on the server?
A. Network Based IDS (NIDS)
B. Personal Firewall
C. System Integrity Verifier (SIV)
D. Linux IP Chains