CAS-005 Online Practice Questions and Answers
DRAG DROP
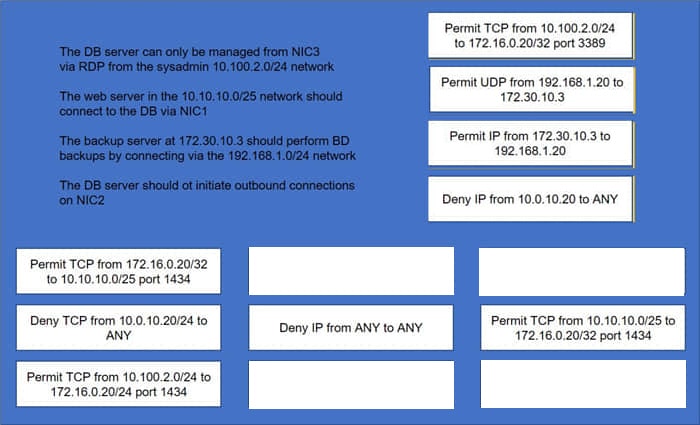
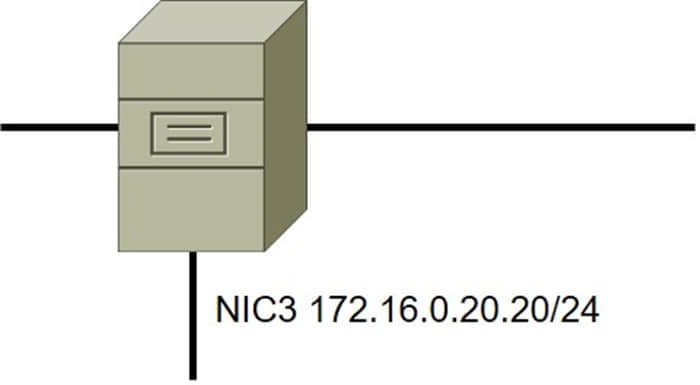
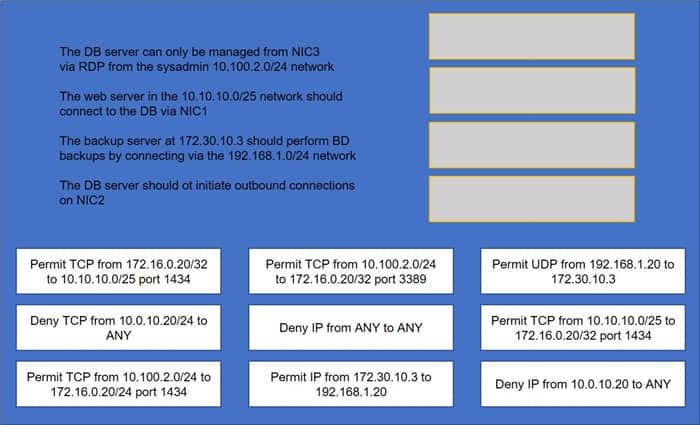
A security administrator must configure the database server shown below the comply with the four requirements listed. Drag and drop the appropriate ACL that should be configured on the database server to its corresponding requirement. Answer options may be used once or not at all.
Select and Place:
A company's security policy states that any publicly available server must be patched within 12 hours after a patch is released A recent llS zero-day vulnerability was discovered that affects all versions of the Windows Server OS:
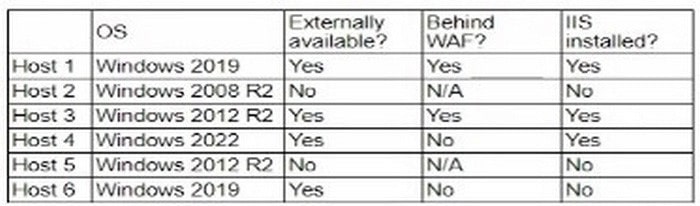
Which of the following hosts should a security analyst patch first once a patch is available?
A. 1
B. 2
C. 3
D. 4
E. 5
F. 6
A senior security engineer flags me following log file snippet as hawing likely facilitated an attacker's lateral movement in a recent breach:
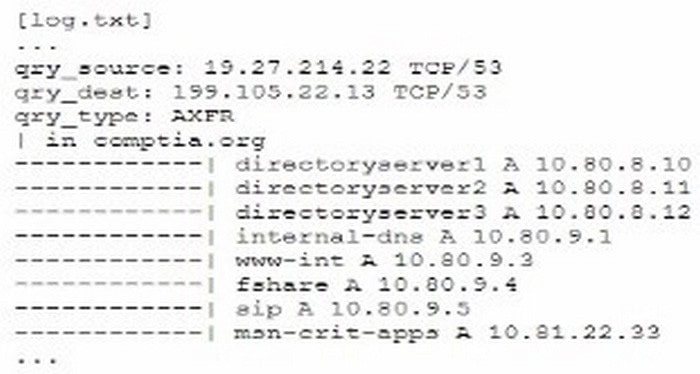
Which of the following solutions, if implemented, would mitigate the nsk of this issue reoccurnnp?
A. Disabling DNS zone transfers
B. Restricting DNS traffic to UDP'W
C. Implementing DNS masking on internal servers
D. Permitting only clients from internal networks to query DNS
A company receives several complaints from customers regarding its website. An engineer implements a parser for the web server logs that generates the following output:
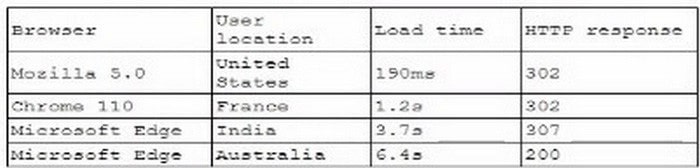
which of the following should the company implement to best resolve the issue?
A. IDS
B. CDN
C. WAF
D. NAC
A company is having issues with its vulnerability management program New devices/lPs are added and dropped regularly, making the vulnerability report inconsistent
Which of the following actions should the company lake to most likely improve the vulnerability management process'
A. Request a weekly report with all new assets deployed and decommissioned
B. Extend the DHCP lease lime to allow the devices to remain with the same address for a longer period.
C. Implement a shadow IT detection process to avoid rogue devices on the network
D. Perform regular discovery scanning throughout the 11 landscape using the vulnerability management tool
After some employees were caught uploading data to online personal storage accounts, a company becomes concerned about data leaks related to sensitive, internal documentation.
Which of the following would the company most likely do to decrease this type of risk?
A. Improve firewall rules to avoid access to those platforms.
B. Implement a cloud-access security broker
C. Create SIEM rules to raise alerts for access to those platforms
D. Deploy an internet proxy that filters certain domains
An application engineer is using the Swagger framework to leverage REST APIs to authenticate endpoints. The engineer is receiving HTTP 403 responses. Which of the following should the engineer do to correct this issue? (Choose two.)
A. Obtain a security token.
B. Obtain a public key.
C. Leverage Kerberos for authentication
D. Leverage OAuth for authentication.
E. Leverage LDAP for authentication.
F. Obtain a hash value.
A company has data it would like to aggregate from its PLCs for data visualization and predictive maintenance purposes. Which of the following is the most likely destination for the tag data from the PLCs?
A. External drive
B. Cloud storage
C. System aggregator
D. Local historian
An organization has deployed a cloud-based application that provides virtual event services globally to clients. During a typical event, thousands of users access various entry pages within a short period of time. The entry pages include sponsor-related content that is relatively static and is pulled from a database. When the first major event occurs, users report poor response time on the entry pages. Which of the following features is the most appropriate for the company to implement?
A. Horizontal scalability
B. Vertical scalability
C. Containerization
D. Static code analysis
E. Caching
Two companies that recently merged would like to unify application access between the companies, without initially merging internal authentication stores. Which of the following technical strategies would best meet this objective?
A. Federation
B. RADIUS
C. TACACS+
D. MFA
E. ABAC