CAS-004 Online Practice Questions and Answers
A company is moving most of its customer-facing production systems to the cloud-facing production systems to the cloud. IaaS is the service model being used. The Chief Executive Officer is concerned about the type of encryption available and requires the solution must have the highest level of security.
Which of the following encryption methods should the cloud security engineer select during the implementation phase?
A. Instance-based
B. Storage-based
C. Proxy-based
D. Array controller-based
A software house is developing a new application. The application has the following requirements:
1.
Reduce the number of credential requests as much as possible
2.
Integrate with social networks
3.
Authenticate users
Which of the following is the BEST federation method to use for the application?
A. WS-Federation
B. OpenID
C. OAuth
D. SAML
A forensic investigator would use the foremost command for:
A. cloning disks.
B. analyzing network-captured packets.
C. recovering lost files.
D. extracting features such as email addresses.
Given the following log snippet from a web server:
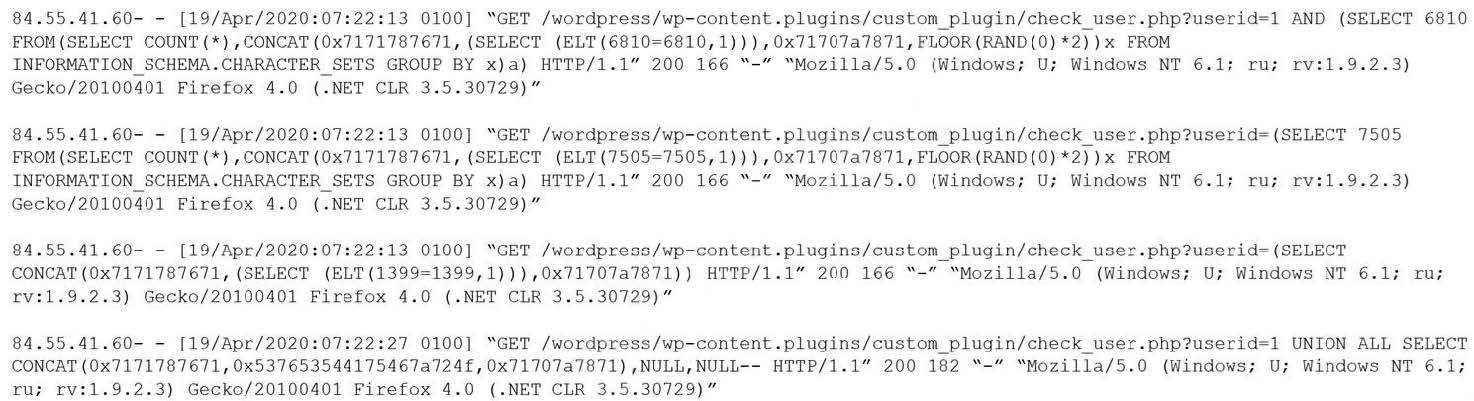
Which of the following BEST describes this type of attack?
A. SQL injection
B. Cross-site scripting
C. Brute-force
D. Cross-site request forgery
A company is repeatedly being breached by hackers who valid credentials. The company's Chief information Security Officer (CISO) has installed multiple controls for authenticating users, including biometric and token-based factors. Each successive control has increased overhead and complexity but has failed to stop further breaches. An external consultant is evaluating the process currently in place to support the authentication controls. Which of the following recommendation would MOST likely reduce the risk of unauthorized access?
A. Implement strict three-factor authentication.
B. Implement least privilege policies
C. Switch to one-time or all user authorizations.
D. Strengthen identify-proofing procedures
A large number of emails have been reported, and a security analyst is reviewing the following information from the emails:
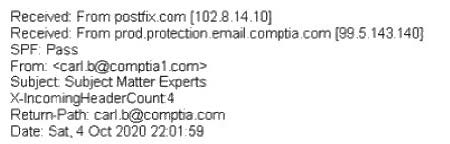
As part of the image process, which of the following is the FIRST step the analyst should take?
A. Block the email address carl b@comptia1 com, as it is sending spam to subject matter experts
B. Validate the final "Received" header against the DNS entry of the domain.
C. Compare the 'Return-Path" and "Received" fields.
D. Ignore the emails, as SPF validation is successful, and it is a false positive
A significant weather event caused all systems to fail over to the disaster recovery site successfully. However, successful data replication has not occurred in the last six months, which has resulted in the service being unavailable. Which of the following would BEST prevent this scenario form happening again?
A. Performing routine tabletop exercises
B. Implementing scheduled, full interruption tests
C. Backing up system log reviews
D. Performing department disaster recovery walk-throughs
An organization is moving its intellectual property data from on premises to a CSP and wants to secure the data from theft. Which of the following can be used to mitigate this risk?
A. An additional layer of encryption
B. A third-party, data integrity monitoring solution
C. A complete backup that is created before moving the data
D. Additional application firewall rules specific to the migration
An analyst received a list of IOCs from a government agency. The attack has the following characteristics:
1.
The attack starts with bulk phishing.
2.
If a user clicks on the link, a dropper is downloaded to the computer.
3.
Each of the malware samples has unique hashes tied to the user.
The analyst needs to identify whether existing endpoint controls are effective. Which of the following risk mitigation techniques should the analyst use?
A. Update the incident response plan.
B. Blocklist the executable.
C. Deploy a honeypot onto the laptops.
D. Detonate in a sandbox.
A security analyst is reviewing the data portion acquired from the following command:
tcpdump -lnvi icmp and src net 192.168.1.0/24 and dst net 0.0.0.0/0 -w output.pcap
The data portion of the packet capture shows the following:
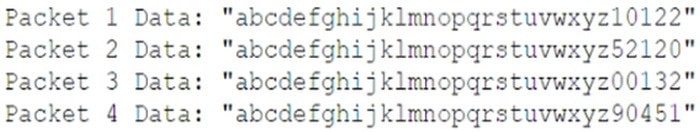
The analyst suspects that a data exfiltration attack is occurring using a pattern in which the last five digits are encoding sensitive information. Which of the following technologies and associated rules should the analyst implement to stop this specific attack? (Choose two.)
A. Intrusion prevention system
B. Data loss prevention
C. sed -e 's/a-z.*0-9.*//g'
D. reject icmp any any <> any any (msg:"alert"; regex [a-z]{26}[0-9]{5})
E. Second-generation firewall
F. drop icmp from 192.168.1.0/24 to 0.0.0.0/0