C_AUDSEC_731 Online Practice Questions and Answers
You are to configure a compliant identity management process flow.
Which of the following components from SAP Access Control and SAP NetWeaver Identity Management (SAP NetWeaver ID Management) are required?
Note: There are 2 correct answers to this question.
A. SAP NetWeaver ID Management - Identity Center (IC) and Virtual Directory Server (VDS)
B. SAP BusinessObjects - Enterprise Role Management (ERM) and Superuser Privilege Management (SPM)
C. SAP NetWeaver ID Management - Dispatcher Runtime Engine and Event Agent Service
D. SAP BusinessObjects - Risk Analysis and Remediation (RAR) and Compliant User Provisioning (CUP) components
Which of the following activities are part of SAP roles design? Note: There are 2 correct answers to this question.
A. Determine the role naming convention
B. Design the SAP transports schedule.
C. Identify SAP and custom transactions and reports.
D. Analyze the data migration requirements.
You have to maintain authorizations for a new role in the Profile Generator (transaction PFCG).
What does the yellow triangle indicate (see attached screenshot)?
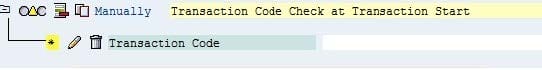
A. You must not give full authorization in this area.
B. The profile for the role has not been generated yet.
C. The maintenance of the authorizations is not done yet; additional work is needed.
D. You do not have the necessary authorization to maintain the authorizations below this level.
Which of the following is a characteristic of composite roles?
A. Users assigned to composite roles have their own authorization data.
B. They can be assigned to other composite roles.
C. They have their own authorization data.
D. Users assigned to composite roles are automatically assigned to the elementary roles.
When you logon to the system with the SAP_AUDITOR_SA role, which of the following reports can be found in the Top 10 Security Reports folder of the Audit Information System (AIS)?
Note: There are 2 correct answers to this question.
A. Date Monitoring (S_PH0_48000450)
B. Analysis of Security Audit Log (SM20N)
C. IDoc List (RSEIDOC2)
D. Check Passwords of Standard Users (RSUSR003)
Which of the following is a characteristic of the physical layer of the OSI model?
A. It passes data from one node to another and performs error detection.
B. It enables program-to-program communication.
C. It places data on the network media and takes the data off the network.
D. It ensures end-to-end integrity of data transmission.
What check must you carry out to analyze system data with Security Optimization Self Service?
A. The SAP Solution Manager system has the latest support plug-ins installed.
B. The system is connected to SAP Solution Manager.
C. SAP Solution Manager is connected to the Security Optimization Service.
D. The system landscape is registered with the Security Optimization Service.
Which of the following are benefits of using Security Optimization Self Service? Note: There are 2 correct answers to this question.
A. It requires no license key for configuration.
B. It updates an SAP system against intruders.
C. It automatically implements security recommendations.
D. It allows customized authorization checks.
Which of the following can the security audit log record? Note: There are 3 correct answers to this question.
A. Remote Function Calls (RFCs) to function modules
B. User license type usages
C. System performance statistics
D. Changes to user master records
E. Successful and unsuccessful transaction starts
Which of the following are reasons to use SAP Business Workflow? Note: There are 2 correct answers to this question.
A. To automate the control and processing of cross-application processes
B. To change existing functions of an SAP system
C. To record the progress of the execution of an application
D. To respond to errors and exceptions in existing business processes