C9010-030 Online Practice Questions and Answers
Which TCP/IP ports are valid when used to remotely connect via SSL or non-SSL to the HMC for 5250 console access?
A. 23 and 992
B. 2300 and 2301
C. 2100 and 2300
D. 22 and 23
A system is configured with U.S. English as the primary language and Spanish as a secondary language. Where is the language specified when setting up a new user profile for a Spanish speaking user?
A. The Language ID parameter in the user profile
B. The Locale parameter in the user profile
C. This user's QLANGID environment variable
D. The Country ID parameter in the user profile
A CL program that runs after an IPL must complete and errors will be researched at a later time. How can all CPF massages be acknowledged so the program continues running?
A. Add a MONMSG(CPFOOOO) command immediately before the ENDPGM command.
B. Add a MONMSG(CPFOOOO) command after the ENDPGM command.
C. Add a MONMSG(CPFOOOO) command immediately after the PGM command.
D. Add a MONMSG(CPFOOOO) command before the PGM command.
A system administrator has just changed the password of the QSECOFR user profile. After verifying the new password with a successful login to the operating system, the administrator attempts a login to System Service Tools with STRSST. All Service Tools login attempts fail with the error CPF225D Requesting service tools ID password not correct. Why is the administrator unable to login to System Service Tools with the new QSECOFR password?
A. The Service Tools password must be set to the default value before It can be changed.
B. The Service Tools security environment has not been configured to allow QSECOFR passwords to be synchronized.
C. The QSECOFR user profiles for System Service Tools and IBM i are not interchangeable and passwords must be maintainedindependently
D. The system value QLMTSECOFR (Limit security officer device access) is set to block sharing of passwords for QSECOFR.
An administrator has bean directed to configure DDM using TCP/IP between two systems: "SYSTEM1"
and "SYSTEM2". Both systems are in the site DNS. Applications on both systems require DDM access to
files on the other system. The administrator has made sure that the Remote Database Directory has the
*LOCAL entry configured correctly on both systems.
What is additionally required so the communications will function correctly between the systems?
A. Add a Remote Database Directory entry for the other system
B. Add a host table entry for QDDMSERVER using address "LOOPBACK on each system
C. Add a host table entry for the local system in its hosts table
D. Change the "DDM Request Access" setting in the network attributes to QDDMSERVER
Given the following code sample:
DCL VAR(andUSER)TYPE(*CHAR) LEN(10)
DCL VAR(andEMAIL1)TYPE(*CHAR) LEN(30)
RTVUSRPRFRTNUSRPRF(andUSER)
SELECT
WHEN COND(andUSER*EQJOHN")THEN(CHGVAR+
VAR(andEMAIL1) VALUECJOHNtgCOMPANY.COM))
OTHERWISE CMD(DO)
SNDPGMMSG MSGID(CPF9898) MSGF(QCPFMSG) +
MSGDTA(YOU ARE NOT AUTHORIZED TO USE THE TOOL) MSGTYPE
(*INFO)
CHGUSRPRF USRPRF(andUSER)STATUS(*DISABLED)
GOTO CMDLBL(END)
ENDDO
ENDSELECT
STRSBS SBSD(BSTSBS)
END: ENDPGM
What will happen when user CARLA starts the program in interactive mode?
A. User gets the message YOU ARE NOT AUTHORIZED TO USE THE TOOLand disables the user profile.
B. User gets the message YOUARE NOTAUTHORIZED TOUSE THE TOOL.
C. User starts the BSTSBS subsystem.
D. User gets the message YOU ARE NOT AUTHORIZED TO USE THE TOOL, the user profile is disabled, and the BSTSBS subsystem is started.
Which product gives MacBook users 5250 emulation and allows for native spooled file copy to the laptop?
A. IBM i Access for Windows using Wine on OS X
B. IBM i Access for Windows running in a virtual machine running on OS X
C. IBM i Access for OS X
D. IBM i Access Client Solutions
An administrator has noticed that the number of security audit journal receivers on the system is getting
unmanageable.
How can the administrator adjust the journal to still capture and retain the required journal entries but
generate fewer receivers?
A. Change the security journal to delete journal receivers.
B. Change the current journal receiver to a higher threshold value.
C. Create a new security journal specifying the number of receivers to use.
D. Create a new journal receiver setting the threshold to a higher value.
Several printers were moved from one IP subnet to another overnight. The printers are accessed by their Fully Qualified Domain Name (FQDN). The FQDNs were changed to resolve to the new addresses the following morning, but the IBM i will still not print to the new printers. The printers can be pinged by their IP addresses.
What is the cause of this problem?
A. The DNS server was not restarted to present the new addresses.
B. The network route to the new subnet is missing.
C. IBM i has cached the resolved IP address before the change.
D. CHGDEVPRT was not run on each device to get the new address
A subsystem description is configured as shown in the following screens;
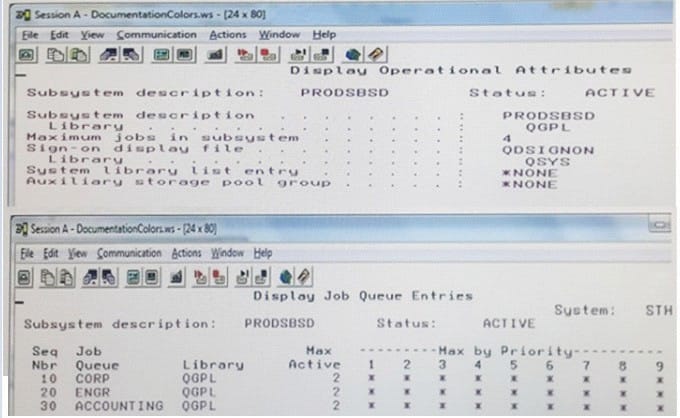
Users are assigned to each job queue to run their batch work. The users assigned to the ACCOUNTING
job queue are complaining that their batch jobs are occasionally not running. Other users do not
experience this issue.
Why are ACCOUNTING users experiencing this problem?
A. The jobs in the ACCOUNTING queue are run at the lowest execution pnonty based on the sequence number field Jobs from CORP and ENGR are consuming all the processing capability allowed for the subsystem.
B. The run priority of the job does not match the sequence number of the job queue entry.
C. The subsystem starts jobs up to the maximum allowed for each job queue starting with the lowest sequence number (SEQ NBR column)
D. The auxiliary storage pool group is not set to match the number of job queue entries in the subsystem.