C4040-129 Online Practice Questions and Answers
In the Work With Shared Pools panel shown, what is the meaning of the "Minimum" column under the "Size" section?
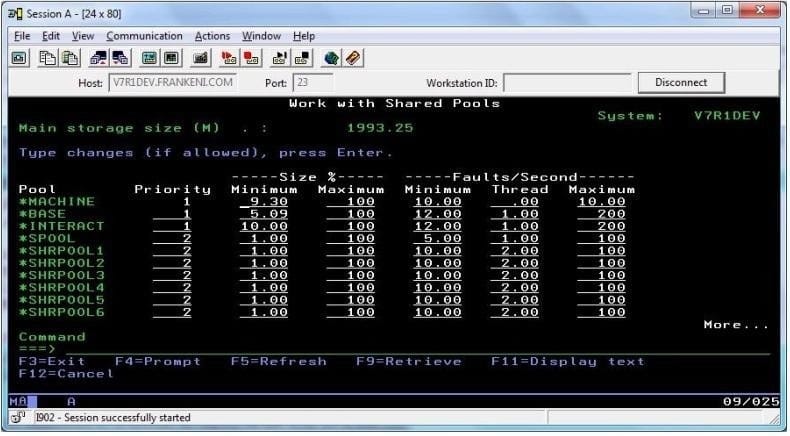
A. The minimum amount of main storage that can be assigned to the pool in GB
B. The minimum percentage of the total main storage that can be assigned to the pool
C. The minimum amount of main storage that the automatic tuner will assign to the pool in GB
D. The minimum percentage of the total main storage that the automatic tuner will assign to the pool
An administrator has been asked to create user profiles for4 operators.
In addition to adding each operator's user profile to the GRPOPR group, which sequence of actions will enable the operators to perform their functions, while maintaining the best possible system security?
A. Create a user profile (GRPOPR) with a user class of *SYSOPR Create a profile for each operator with no special authority
B. Create a user profile (GRPOPR) with no special authority Create a profile for each operator with *SAVSYS special authority
C. Create a user profile (GRPOPR) with *IOSYSCFG special authority Create a profile for each operator with no special authority'
D. Create a user profile (GRPOPR) with *SECADM special authority' and a user class of *SYSOPR Create a profile for each operator with no special authority'
Which URL will connect remotely to the HMC with a host name of HMC for partition management?
A. http://hmc1
B. https://hmc1
C. http://hmc1:2001
D. https://hmc1:2300
After resetting the QSECQER DST/SST password to the default value1 the password is expired and the administrator is unable to change it from the operating system due to security restrictions. How can the password be changed with the least interruption to other users and jobs on the system?
A. IPL the partition in manual mode, change the QSECOFR DST/SST password.
B. Issue a control panel function 21 to activate DST and change the password there.
C. Issue the command CHGDSTPWD again, but also special password expiration override.
D. Use the serial interface and ASMI Admin profile to enable the QSECOFR profile for DST/SST.
An application uses commitment control and has the following attributes: Physical files in library: APDATA Logical files in library: APLE Journals in library: APJRN Journal receivers in APJRNPCV
Application objects must be saved at a transaction boundary.
Which parameter of the SAVLIB command of the following supports this requirement?
A. ACCPTH(*YES)
B. SAVACT(*LIB)
C. TNSBND(*YES)
D. SAVACT(*SYNCLIB)
An IBM i 7.1 partition has a system ASP that has a combination of Solid State Drive (SSD) units and Hard Disk Drive (HDD) units. The system administrator needs to permanently migrate the logical files that are randomly accessed by the application jobs to the SSDs.
What is the appropriate method for identifying the most randomly accessed logical and physical files?
A. Query the table QSYS2/SYSIXSTAT for files with logical reads greater than U and sequence in descending order.
B. Use WRKACTJOB command to identify the application jobs.For each job, select option 5=Work with, then 14.Display open files, if active, than press Fl 1.
C. From Performance Tools, generate a system report to an output file.Query the output file for logical files with random reads greater than U and sort in descending order.
D. Trace the accessed file data using the TRCASPBAL SET(*ON) ASP(l) command.Print the report with the command PRTTRCRPTTYPE (*FILE) QRDER(*DESC), and look for Random Reads/sec.
A customer determines that run time of a weekly reporting job has begun to increase rapidly over the past several months. Examination of the file shows only normal size growth of less than 1%.
The entire file is read sequentially by key and is heavily I/O blocked for performance.
What should the administrator do to reduce run-time for the reporting job?
A. Override the file to SEQONLY(*YES).
B. Reorganize the file to remove deleted records.
C. Reorganize the rile in the sequence of the key field.
D. Increase the job's time slice and enable expert cache in the memory pool in which the job runs.
A customer with in-house developed applications has many custom commands in library APPLIB that relate to the application programs. As part of a system audit, the administrator needs to run a report to determine which user profiles have authority to run the commands. Given the application library APPLIB, which report from the Security Tools menu should the administrator use to complete this task?
A. Option 21 - Adopting Objects
B. Option 40 - Program Authority
C. Option 49- User Profile Authority
D. Option 25- Command Private Authority
Which object has the Routing Entry Compare Data that is used by the subsystem to route a job?
A. Class
B. Job Description
C. Routing Directory
D. Workstation Entries
A tape cycle consists of 5 daily save tapes. After restoring a library from the Monday tape the administrator discovered that the library restored was from 2 weeks ago rather than last week. Which action will allow the administrator to restore the correct version of the library in the future?
A. Modify the save procedure to initialize the tape prior to the save.
B. Use the OMITLIB parameter on the restore to omit the older versions of the library.
C. Use sequence number *LAST on the restore to restore the most recent version of the library.
D. Use the POSITION parameter on the restore to specify *LASTSAV restoring only the most recent version.