C2150-197 Online Practice Questions and Answers
Separation of Duty policies create mutually exclusive relationship between what in order to protect sensitive information from conflicts of interest?
A. Provisioning policies
B. Accounts
C. Groups
D. Roles
The Recycle Bin has been activated, the Recycle Bin Age is set to 62 days, and the IdapClean script is set to run daily.
When IdapClean completes, which statement is true?
A. Some objects in the Directory Server's Recycle Bin may not be deleted even if age is greater than Recycle Bin Age Limit.
B. All objects in the Directory Server's Recycle Bin will be deleted regardless of age greater than Recycle Bin Age Limit.
C. All objects in the Directory Server's Recycle Bin will be deleted if their age is greater than Recycle Bin Age Limit.
D. Objects in the Directory Server's Recycle Bin will be deleted if their age is less than Recycle Bin Age Limit.
Life cycle rule is triggered automatically by which event?
A. A schedule and matching criteria evaluated against an entity.
B. External event.
C. Schedule only.
D. Internal event.
Your customer has four important business systems that drive their environment. Which of these systems would be the highest priority for a services design and adapter plan?
A. A virtualization host system used for application development and testing by everyone in the IT department.
B. A database system that is accessed by every individual enterprise application via a JDBC connector.
C. An employee portal system running on WebSphere used for general HR, email, and company news.
D. An accounting system accessed by the financial team only when authorized by the CFO.
Which document describes the relationship between the business requirements and the features of the Security Identity Manager that will be included in the initial solution rollout?
A. Solution Architecture Document
B. Security Policy Design
C. Feature Inclusion List
D. Initial Project Plan
Which TWO of the following components should be setup using secure SSL communication as best practice in an IBM Security Identity Manager environment?
A. Adapter installer
B. Report server
C. SMTP server
D. HTTP server
E. Adapters
When gathering requirements for workflows, which function uses workflows?
A. Organization Tree development
B. LDAP Adapter development
C. Reconciliation development
D. Lifecycle development
What does the following service selection policy return?
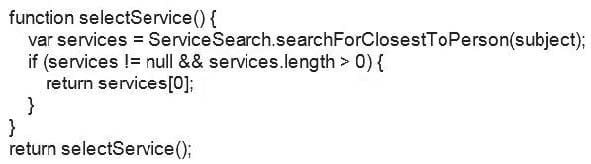
A. It returns multiple services of the same kind for the subject to choose in a dynamic workflow.
B. It returns the service closest to the subject based on the 'location' attribute of the subject.
C. It returns the service closest to the subject in the organizational tree defined in ISIM.
D. It returns the service closest to the service that the subject has requested.
Where is output from Enrole.logError() written?
A. access.log
B. trace.log
C. msg.log
D. ffdc.Iog
What is the main purpose of the IBM Security Identity Manager (ISIM) recycle bin?
A. To provide a quick failover mechanism if IBM Security Identity Manager LDAP fails
B. To provide a ready-recoverability of inadvertently deleted objects
C. To preserve a history of user IDs that have been used
D. To enhance LDAP performance