C2090-600 Online Practice Questions and Answers
What is the schema name of the DB2 built-in global variable TRUSTED_CONTEXT?
A. SYSIBM
B. SYSFUN
C. SYSCAT
D. SYSIBMADM
When the DB2_WORKLOAD registry variable is assigned the value ANALYTICS and then a new database is created, what happens? (Choose two.)
A. The PAGESIZE database configuration parameter is set to 32K.
B. The AUTO_REORG database configurationparameter is set to NO.
C. The DFT_EXTENT_SZ database configuration parameter is set to 8.
D. The DFT_TABLE_ORG database configuration parameter is set to COLUMN.
E. The INTRA_PARALLEL database manager configuration parameter is set to NO.
Assuming no database connections exist, which of the following will dynamically change the LOCKLIST database configuration parameter for a database named SAMPLE to AUTOMATIC?
A. UPDATE DB CFG FOR sample USING LOOCKLIST AUTOMATIC IMMEDIATE
B. UPDATE DB CFG FOR sample USING LOOCKLIST 8192 AUTOMATIC IMMEDIATE
C. CONNECT TO sample;UPDATE DB CFG FOR sample USINGLOCKLIST AUTOMATIC IMMEDIATE;CONNECT RESET;
D. ATTACH TO db2inst1;UPDATE DB CFG FOR sample USING LOCKLIST AUTOMATIC;DETACH;
What is the result of the following scenario?
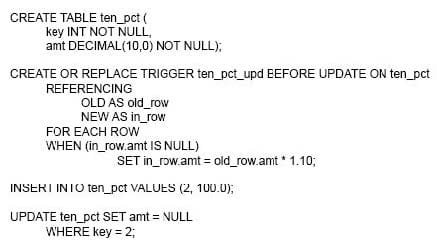
A. The row is updated to (2, NULL)
B. The row is updated to (2, 110.00)
C. SQL0407N Assignment of a NULL value to a NOT NULL column is not allowed
D. The CREATE TRIGGER statement will fail because amt is defined as NOT NULL
Which ALTER TABLE statements will put a table named TAB1 in "reorg-pending" state? (Choose two.)
A. ALTER TABLE tab1 APPEND ON
B. ALTER TABLE tab1 DROP COLUMN col1
C. ALTER TABLE tab1 ALTER COLUMN col1 SET NOT NULL
D. ALTER TABLE tab1 DETACH PARTITION part1 INTO tab_part1
E. ALTER TABLE tab1 ADD CONSTRAINT pk_tab1 PRIMARY KEY (col1)
Which security mechanism is responsible for verifying that users are indeed who the claim to be?
A. Authentication
B. Roles and privileges
C. Mandatory access control
D. Discretionary access control
When choosing the dimensions for an MDC table, poor space utilization can occur due to low cell density. What can cause an MDC table to use much more space?
A. The page size is too small.
B. The extent size is too small.
C. Low cardinality of the dimension(s) chosen.
D. High cardinality of the dimension(s) chosen.
What is the main benefit of performing an ADMIN_MOVE_TABLE operation in multiple steps?
A. It does not acquire locks on the table
B. It does not require additional temporary disk space
C. It enables the user to control when the table will be offline
D. It allows the ADMIN_MOVE_TABLE procedure to be used in HADR environments
Which operation can be performed with trusted context privileges that are acquired through a role?
A. DML operations
B. DDL operations
C. Server maintenance operations
D. Security administration operations
Which statement about label-based access control (LBAC) is TRUE?
A. LBAC protection can be applied to a nickname
B. LBAC cannot be used to restrict access to a staging table
C. LBAC cannot be used to restrict access to data of columns and rows in the same table
D. LBAC protection for columns requires a table to contain a column that has a DB2SECURITYLABEL data type