98-367 Online Practice Questions and Answers
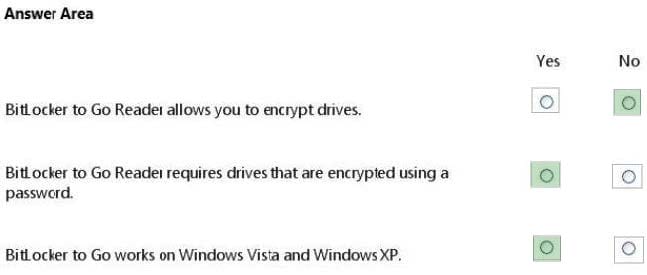
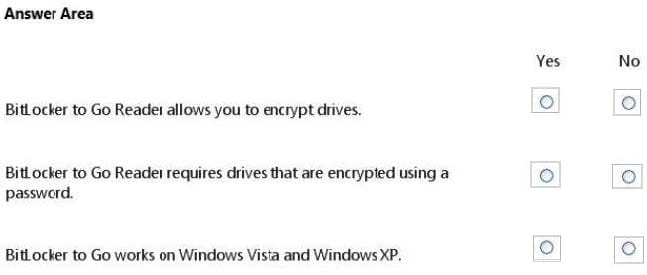
For each of the following statements, select Yes if the statement is true. Otherwise, select No. Each correct selection is worth one point.
Hot Area:
An attorney hires you to increase the wireless network security for the law firm's office. The office has a very basic network, with just a modem and a router. Which of these security modes offers the highest security?
A. WPA-Personal
B. WEP
C. WPA2-Personal
D. WPA-Enterprise
Mark works as a Network Administrator fot Blue Well Inc. The company has a Windows-based network. Mark is facing a series of problems with email spam and identifying theft via phishing scams. He wants to implement the various security measures and to provide some education because it is related to the best practices while using email. Which of the following will Mark ask to employees of his company to do when they receive an email from a company they know with a request to click the link to "verify their account information"?
A. Provide the required information
B. Hide the email
C. Use Read-only Domain Controller
D. Delete the email
Which of the following types of attack is used to configure a computer to behave as another computer on a trusted network by using the IP address or the physical address?
A. Distributed denial of service (DDOS) attack
B. Honeypot
C. RIP/SAP Spoofing
D. Identity spoofing
Which of the following security features of IE 7+ helps determine whether a Web site is a legitimate site?
A. Protected mode
B. Pop-up blocker
C. Security zones
D. Phishing filter
Which of the following MMC snap-in consoles is used to administer the replication of directory data among all sites in an Active Directory Domain Services (AD DS) forest?
A. Active Directory Domains and Trusts
B. Active Directory Administrative Center
C. Group Policy Management Console
D. Active Directory Sites and Services
John works as a Network Administrator for We-are-secure Inc. The We-are-secure server is based on Windows Server 2003. One day, while analyzing the network security, he receives an error message that Kernel32.exe is encountering a problem. Which of the following steps should John take as a countermeasure to this situation? Each correct answer represents a complete solution. Choose all that apply.
A. He should restore his Windows settings.
B. He should upgrade his antivirus program.
C. He should observe the process viewer (Task Manager) to see whether any new process is running on the computer or not. If any new malicious process is running, he should kill that process.
D. He should download the latest patches for Windows Server 2003 from the Microsoft site, so that he can repair the kernel.
Which of the following is often used for one-to-many communications using broadcast or multicast IP datagrams?
A. UDP
B. FTP
C. HTTP
D. SMTP
The reason for implementing Service Set IDentifier (SSID) masking is to:
A. enforce a more secure password policy
B. hide a wireless network name from unknown computers
C. hide a network share from unauthorized users
D. disable autologon
Encrypting a hard disk is an example of ensuring:
A. security be default
B. confidentially
C. integrity
D. least privilege