5V0-91.20 Online Practice Questions and Answers
Which ID in Endpoint Standard is associated with one specific action, involves up to three different hashes (Parent, Process, Target), and occurs on a single device at a specific time?
A. Threat ID
B. Process ID
C. Alert ID
D. Event ID
There is a requirement to block ransomware when a sensor is offline. Which blocking and isolation rule fulfills this requirement?
A. Known Malware --> Performs ransomware-like behavior --> Terminate process
B. Not Listed Application --> Performs ransomware-like behavior --> Deny operation
C. Suspect Malware --> Performs ransomware-like behavior --> Deny operation
D. Unknown Application --> Performs ransomware-like behavior --> Terminate process
A Carbon Black administrator received an alert for an untrusted hash executing in the environment. Which two information items are found in the alert pane? (Choose two.)
A. Launch Live Query
B. Launch process analysis
C. User quarantine
D. Add hash to banned list
E. IOC short name
Refer to the exhibit:
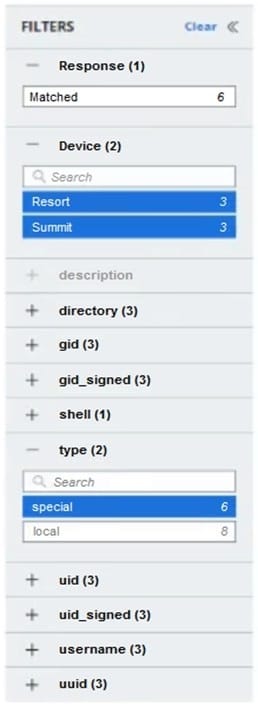
Which two logic statements correctly explain filtering within the UI? (Choose two.)
A. Filtering between fields is a logical OR
B. Filtering within the same field is a logical AND C. Filtering between fields is a logical AND
D. Filtering between fields is a logical XOR
E. Filtering within the same field is a logical OR
An administrator is reviewing an alert about a known and required application in the environment. The application has been given the reputation of PUP, with the alert reason being that the PUP was detected. As a result, this application is matching policy blocking and isolation rules for PUPs in the environment and Is not behaving as expected.
Which step should the administrator take to remediate this situation?
A. Add the file to the Approved List and Dismiss alert
B. Add the file to the Approved List
C. Dismiss the alert
D. Add the file to the Banned List and Delete application
An Enterprise EDR administrator has created a custom Watchlist and wants to add a custom query to a report in the custom Watchlist.
From which page can the administrator add this custom query?
A. Policies
B. Watchlists
C. Investigate
D. Cloud Analysis
An analyst has investigated two alerts on two separate HR workstations and found that notepad.exe has established communication to another IP address.
Which rule will kill notepad.exe entirely if this activity is detected in the future?
A. **\system32\notepad.exe --> Communicates over the network --> Terminate process
B. **\system32\notepad.exe --> Runs or is Running --> Deny operation
C. **/system32/notepad.exe --> Runs or is Running --> Terminate process
D. **/system32/notepad.exe--> Communicates over the network --> Deny operation
Which actions are available for Permissions?
A. Approve, Upload, No Upload
B. Deny Operation, Terminate Process
C. Allow, Allow and Log, Bypass
D. Performs any Operation, Runs or is running
What does the Aggressive setting do when configured in Local Scan Settings?
A. It adds a temporary reputation.
B. It scans all files on execution.
C. It scans new files on first execution.
D. It enables signature updates for the scanner.
A company uses Audit and Remediation to check configurations and adhere to compliance regulations. The regulations require monthly reporting and twelve months of data retained.
How can an administrator accomplish this requirement with Audit and Remediation?
A. Schedule the query to run monthly, and set the data retention to 12 months for the query.
B. Schedule the query to run monthly, and configure the audit log retention to 12 months.
C. Schedule the query to run monthly, and no further action is required.
D. Schedule the query to run monthly, and export the results for each run to an external location.