412-79V10 Online Practice Questions and Answers
In the TCP/IP model, the transport layer is responsible for reliability and flow control from source to the destination. TCP provides the mechanism for flow control by allowing the sending and receiving hosts to communicate. A flow control mechanism avoids the problem with a transmitting host overflowing the buffers in the receiving host.
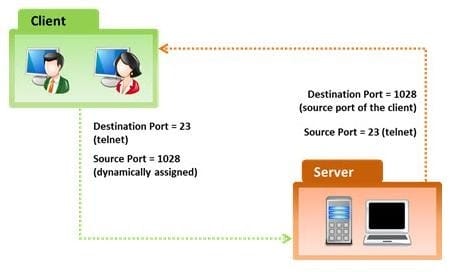
Which of the following flow control mechanism guarantees reliable delivery of data?
A. Sliding Windows
B. Windowing
C. Positive Acknowledgment with Retransmission (PAR)
D. Synchronization
What are the scanning techniques that are used to bypass firewall rules and logging mechanisms and disguise themselves as usual network traffic?
A. Connect Scanning Techniques
B. SYN Scanning Techniques
C. Stealth Scanning Techniques
D. Port Scanning Techniques
Application security assessment is one of the activity that a pen tester performs in the attack phase. It is designed to identify and assess threats to the organization through bespoke, proprietary applications or systems. It checks the application so that a malicious user cannot access, modify, or destroy data or services within the system.
Identify the type of application security assessment which analyzes the application-based code to confirm that it does not contain any sensitive information that an attacker might use to exploit an application.
A. Web Penetration Testing
B. Functionality Testing
C. Authorization Testing
D. Source Code Review
Which of the following are the default ports used by NetBIOS service?
A. 135, 136, 139, 445
B. 134, 135, 136, 137
C. 137, 138, 139, 140
D. 133, 134, 139, 142
By default, the TFTP server listens on UDP port 69. Which of the following utility reports the port status of target TCP and UDP ports on a local or a remote computer and is used to troubleshoot TCP/IP connectivity issues?
A. PortQry
B. Netstat
C. Telnet
D. Tracert
Vulnerability assessment is an examination of the ability of a system or application, including the current security procedures and controls, to withstand assault.
What does a vulnerability assessment identify?
A. Disgruntled employees
B. Weaknesses that could be exploited
C. Physical security breaches
D. Organizational structure
Which one of the following architectures has the drawback of internally considering the hosted services individually?
A. Weak Screened Subnet Architecture
B. "Inside Versus Outside" Architecture
C. "Three-Homed Firewall" DMZ Architecture
D. Strong Screened-Subnet Architecture
From where can clues about the underlying application environment can be collected?
A. From the extension of the file
B. From executable file
C. From file types and directories
D. From source code
Which of the following attributes has a LM and NTLMv1 value as 64bit + 64bit + 64bit and NTLMv2 value as 128 bits?
A. Hash Key Length
B. C/R Value Length
C. C/R Key Length
D. Hash Value Length
If a web application sends HTTP cookies as its method for transmitting session tokens, it may be vulnerable which of the following attacks?
A. Parameter tampering Attack
B. Sql injection attack
C. Session Hijacking
D. Cross-site request attack