3V0-624 Online Practice Questions and Answers
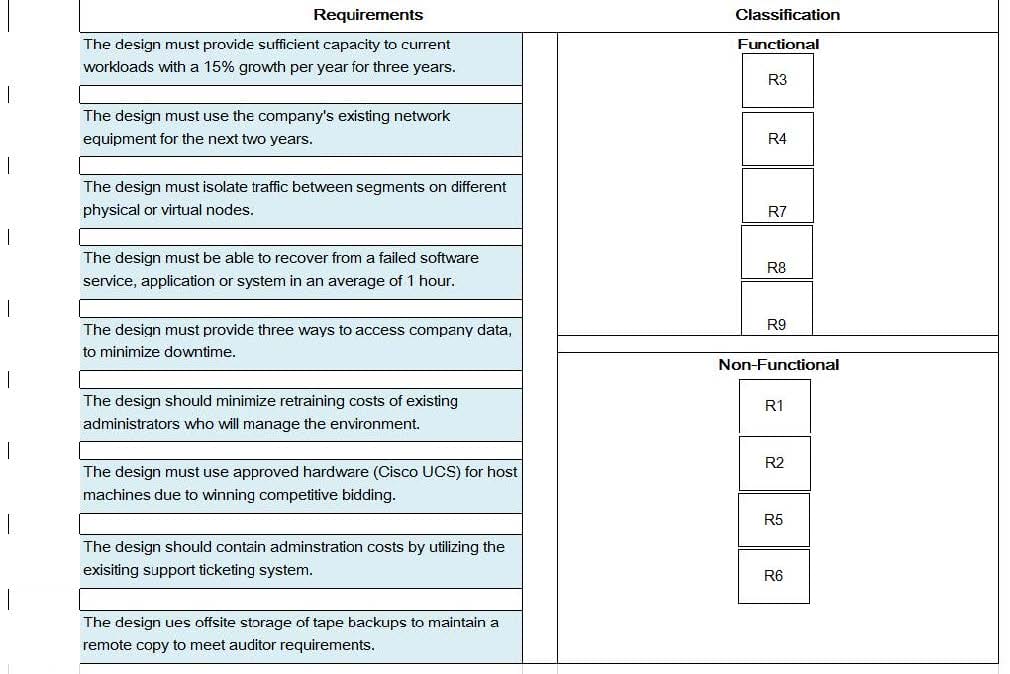
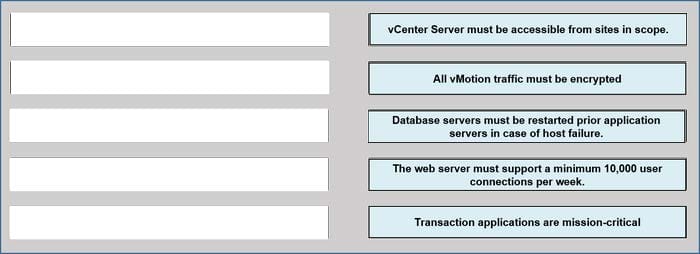
You have been tasked with creating a vSphere 6.5 data center design for an organization. The organization has provided information via requirements gathering. Evaluate each statement and determine if the requirement is functional or nonfunctional.
Match Requirements on the left by dragging the red buttons (R1-R9) over the text of the appropriate Classification.
Select and Place:
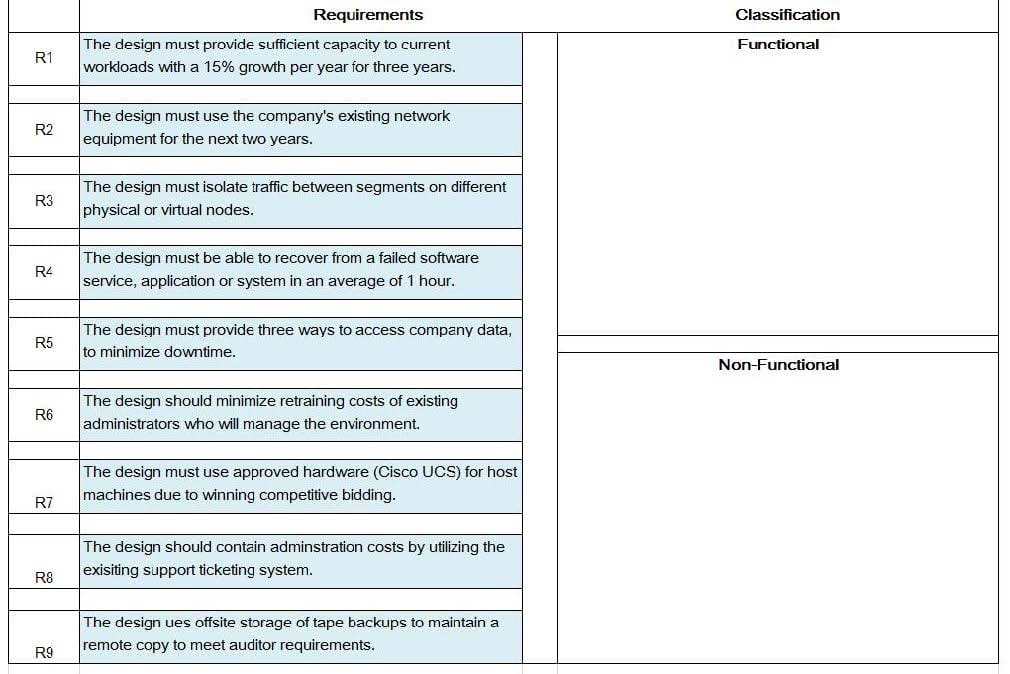
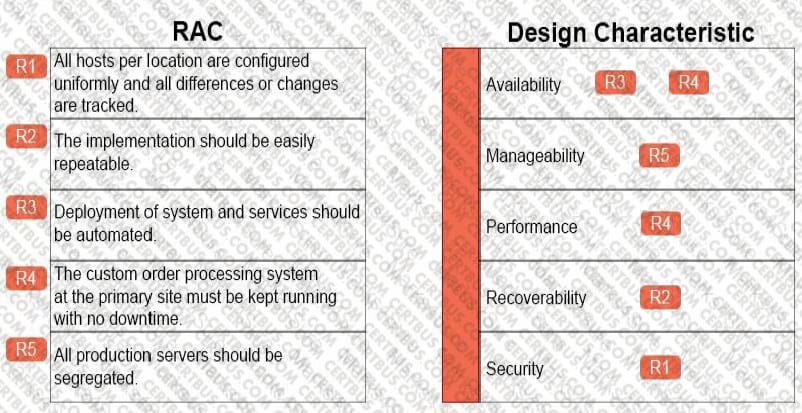
You have been tasked with creating a vSphere 6.5 data center design for an organization. During the key stakeholder and SME interviews. a set of goals, requirements, assumptions and constraints were identified.
Evaluate each of the requirements, assumptions, and constraints (RAC) and determine which design characteristics apply.
Match each of the Requirements, Assumptions and Constraints by dragging the RAC buttons (R1-R5) over the text of the appropriate Design Characteristic.
NOTE: RACs may fit one or more of the Design Characteristics.
Select and Place:
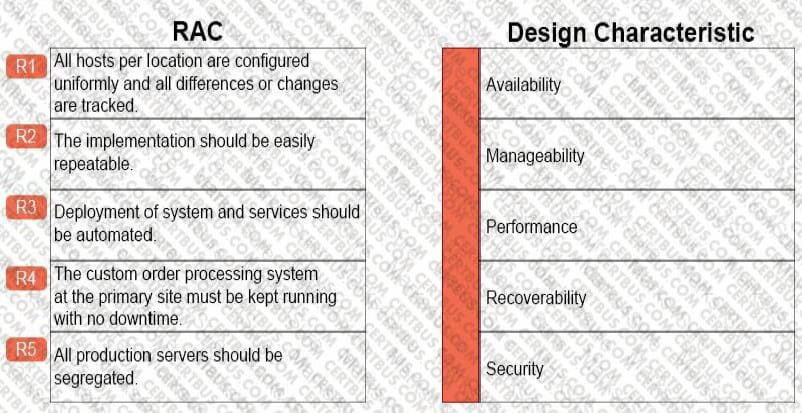
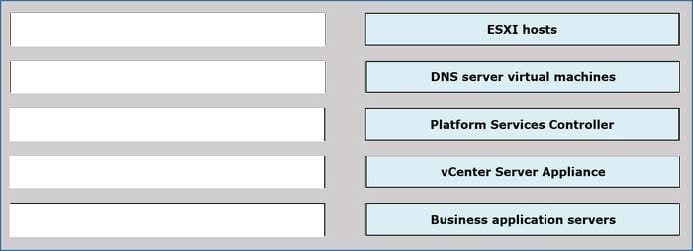
Power has just been restored to the data center after a catastrophic power failure. All storage and networks are back online.
In what order should the following systems be powered on?
Select and Place:
A virtualization administrator has been tasked with migrating several business applications from physical to virtual. The administrator must also migrate the virtual machines from VMware Workstation to vSphere 6.5, using vCenter Converter Standalone 6.1.
In this scenario, when two source types are supported? (Choose two.)
A. powered-off Windows Server 2008 physical machine
B. powered-on Windows Server 2000 Workstation virtual machine
C. powered-off Windows Server 2008 Workstation virtual machine
D. powered-on Windows Server 2008 physical machine
A company is implementing a new cluster to support its end user desktop workloads.
1.
The workload is required to support 200 virtual machines.
2.
Each end-user desktop is configured with two vCPUs, 8GB of RAM, and 40GB of thick-provisioned disk space.
3.
The architect has expressed concerns that virtual machine swap files will till the 8.5TB datastore available to the cluster.
Which two strategies would address the architect's concern? (Choose two.)
A. Configure an additional datastore for snapshot storage
B. Configure an additional datastore for vswap file storage
C. Configure each virtual machine with a 4GB memory reservation.
D. Configure each virtual machine with a 8GB memory reservation.
A customer is using blade servers with only one HBA.
Which two design concepts apply to this scenario? (Choose two.)
A. Assumption
B. Risk
C. Constraint
D. Requirement
A developer is tasked with building an application to process shipping requests. The developer is consulting the vSphere team to determine failover options and performance best practices.
1.
The development team is providing three physical ESXi hosts with 8 CPU cores and 256G8 of RAM per host.
2.
The developer does NOT know how many virtual machines they will require.
Which virtual machine (VM) sizing strategy will provide the highest level of uptime, individual VM performance, and failover capacity?
A. A few large 8 vCPU VMs per host protected by vSphere HA.
B. Many small 1 vCPU VMs participating in an OS level clustered application protected by vSphere HA.
C. A few large 8 vCPU VMs per host protected by vSphere Fault Tolerance.
D. Many small l vCPU VMs participating in an OS level clustered application protected by vSphere Fault Tolerance.
The customer has two sites that must operate independently of each other in the event of a WAN failure. During normal operations, administrators from each site must be able to manage the other site through the vSphere Web Client.
Which vCenter Server Appliance (VCSA) and Platform Services Controller (PSC) diagram shows the VMware-recommended design that satisfies these requirements?
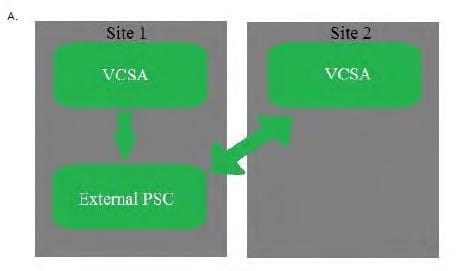
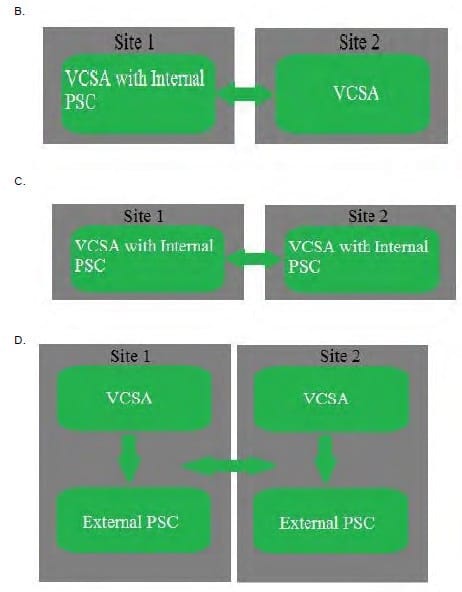
A. Exhibit A
B. Exhibit B
C. Exhibit C
D. Exhibit D
Two DCs with 10mb circuit:
1.
This comprise of vSphere replication and srm in place for DR and recovery
2.
it can tolerate up to 1 hour of data loss
3.
the data change rate is about 10Gb/hour What would be the logical concept? (Choose Two)
A. The company will be able to meet the RPO of 1 hour
B. The company will not be able to meet the RPO of 1 hour
C. Requirement: The distance between DCs will be less than 100KMs
D. Constraint: vSphere replication must be utilized
E. Assumption: the data center interconnects uses vSphere replication