350-901 Online Practice Questions and Answers
Refer to the exhibit.
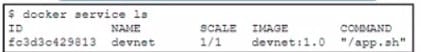
Refer to the exhibit A Docker swarm service is currently running m a local data center The service is hosting an HTML website it the container fads then the service becomes unavailable The design must meet these requirements
The service must be highly available and resilient against a data center outage. The service must be accessible from a single URL The HTTP session must remain on the server from which the original request was sent Failure of the server must force the client to reconnect
Which two design approaches must be used to meet the requirements? (Choose two.)
A. Create another swarm cluster within a data center and deploy a secondary instance of the service.
B. Create another node in the swarm duster to scale the service across the nodes over two replicas.
C. Configure an external load balancer to route requests to the swarm service by using session persistence
D. Scale the Docker swarm service to 2 and set endpoint-mode to DNSRR instead of the default value of VIP
E. Configure a routing mesh to route requests to the swarm service by using NAT on the network side
Which two countermeasures help reduce the risk of playback attacks? (Choose two.)
A. Store data in a NoSQL database.
B. Implement message authentication (HMAC).
C. Enable end-to-end encryption.
D. Remove stack traces from errors.
E. Use short-lived access tokens.
What is the result of a successful OAuth2 authorization grant flow?
A. The user has the application rights that correspond to the user's role within the application's database
B. The application is provided with a token that allows actions on services on the user's behalf
C. The user has administrative rights to the application's backend services
D. The third-party service is provided with a token that allows actions to be performed
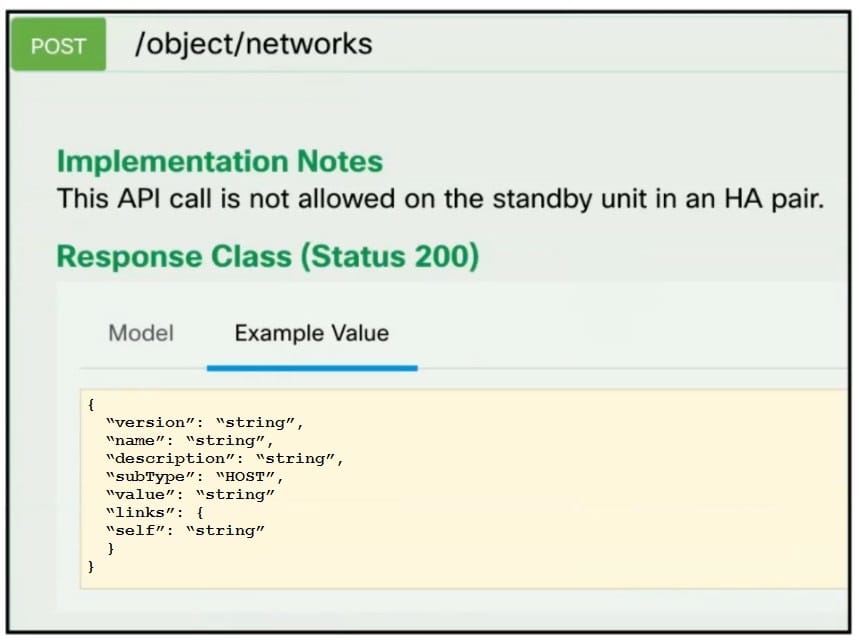
Refer to the exhibit. A developer must create a new network object named testnetwork by using the Cisco Firepower Device Management API. The script must also handle any exceptions that occur during the request and print out any resulting errors. Which script must be used?
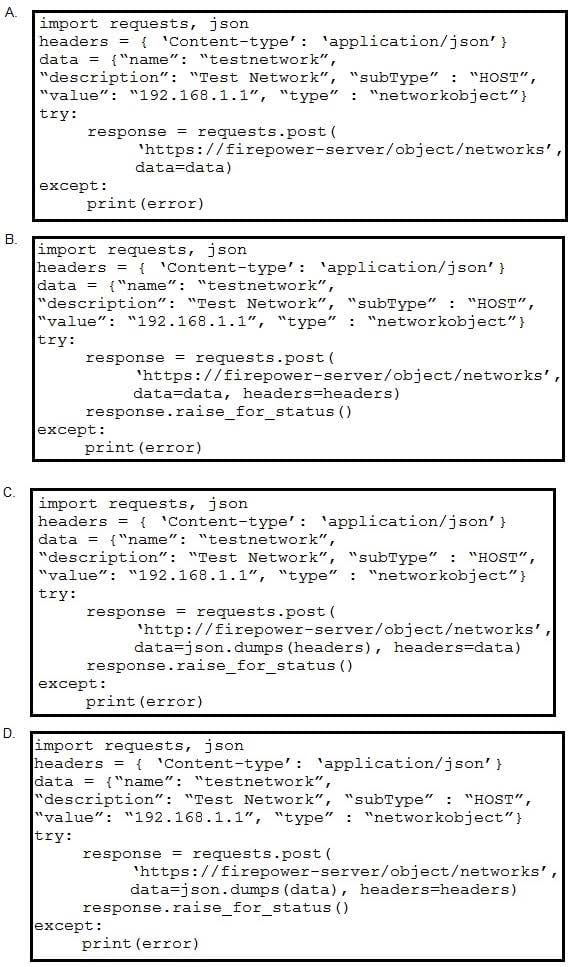
A. Option A
B. Option B
C. Option C
D. Option D
Which action enhances end-user privacy when an application is built that collects and processes the location data from devices?
A. Pepper the MAC address for each device.
B. Salt the MAC address for each device.
C. Implement an algorithmic information theoretic loss to the MAC address for each device.
D. Use the network device serial number to encrypt the MAC address for each device.
Refer to the exhibit.
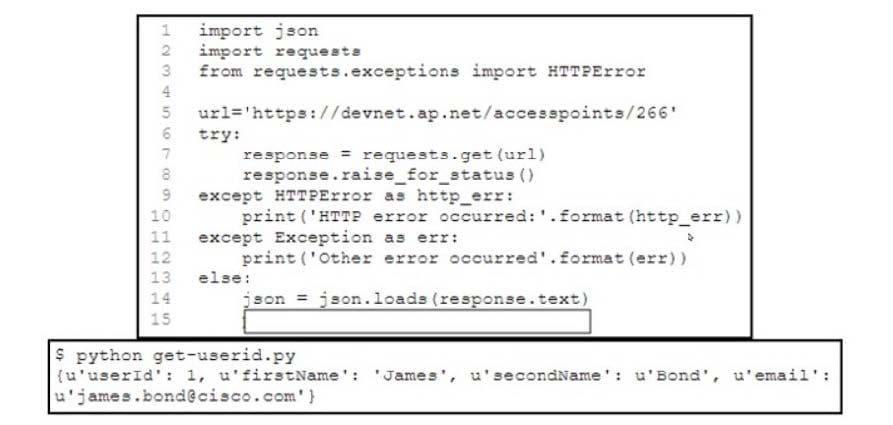
A developer has created a Python script that retrieves information about the deployment of Cisco wireless access points using REST API. Which two code snippets must be added to the blank in the code to print the value of the userid key instead of printing the full JSON response? (Choose two.)
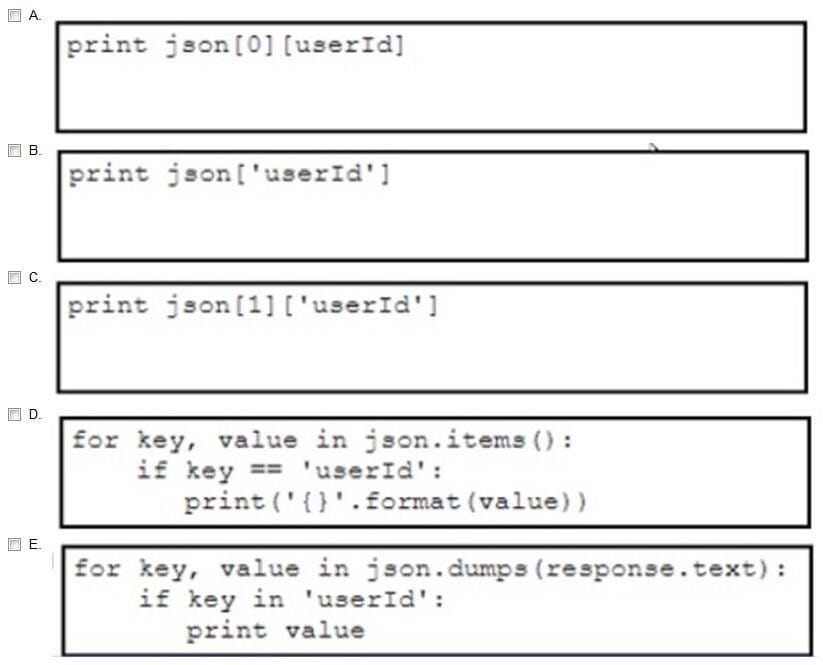
A. Option A
B. Option B
C. Option C
D. Option D
E. Option E
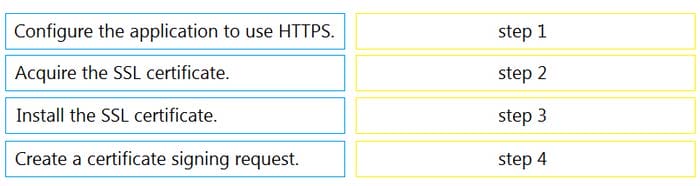
DRAG DROP
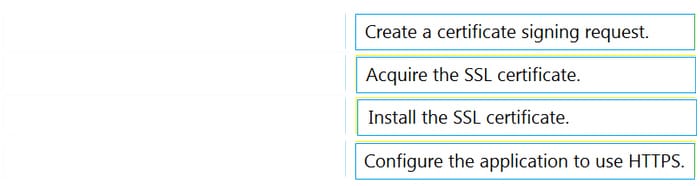
An engineer is developing a web-based application that will be used as a central repository for the HR department. The application needs to authenticate user access and encrypt communication. Drag and drop the steps from the left into the order on the right to install an application-specific SSL certificate.
Select and Place:
DRAG DROP
Refer to the exhibit.
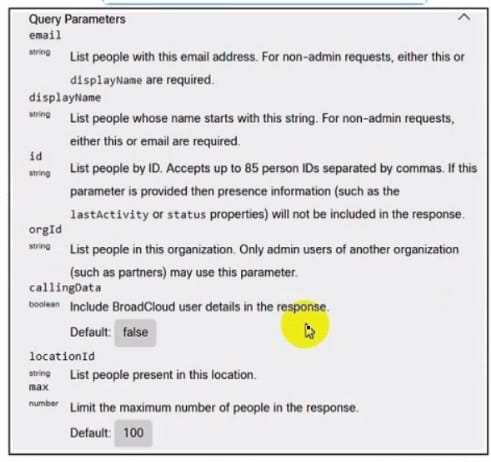
Drag and drop the code snippets from the bottom onto the boxes where the code is missing to retrieve a list of all the members of a specific Cisco Webex organization Not at options are used.
Select and Place:
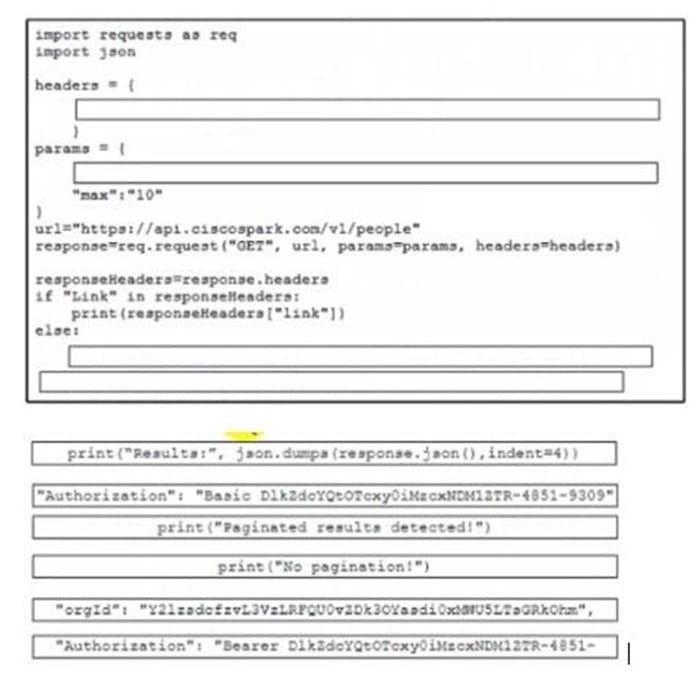
DRAG DROP
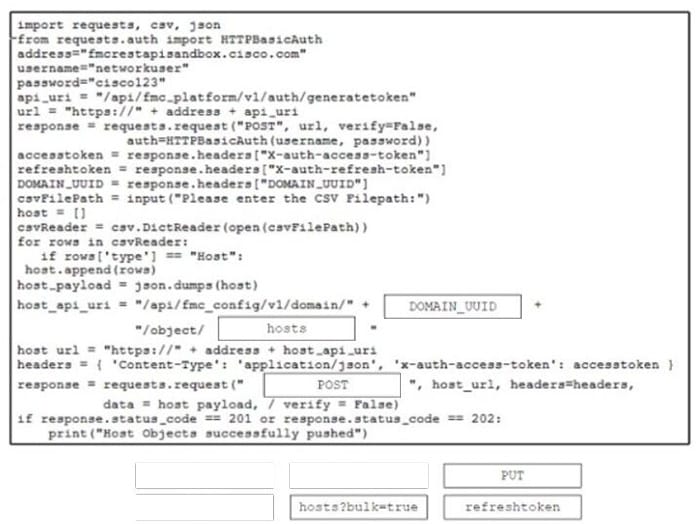
Refer to the exhibit.
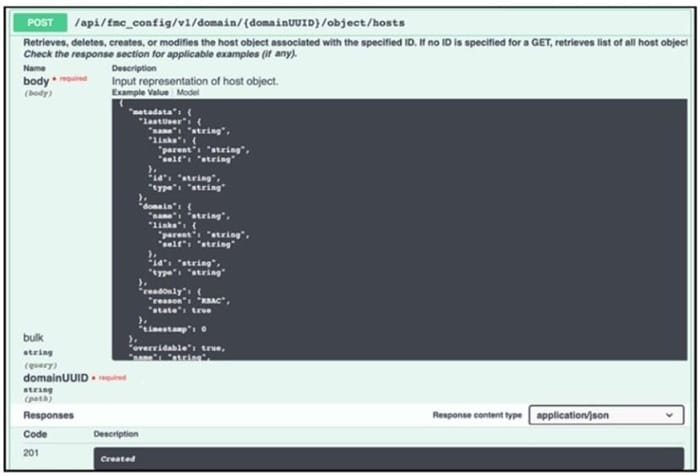
Drag and drop the code from the bottom onto the box where the code is missing in the script to read from a .csv file and import the host entries. The script uses the Cisco Firepower API to create the appropriate entries. The script will be used as part of the security analysis dashboard application to visualize data about network security and host information. Not all options are used.
Select and Place: