350-701 Online Practice Questions and Answers
Which proxy mode must be used on Cisco WSA to redirect TCP traffic with WCCP?
A. transparent
B. redirection
C. forward
D. proxy gateway
What two mechanisms are used to redirect users to a web portal to authenticate to ISE for guest services? (Choose two)
A. multiple factor auth
B. local web auth
C. single sign-on
D. central web auth
E. TACACS+
Refer to the exhibit.
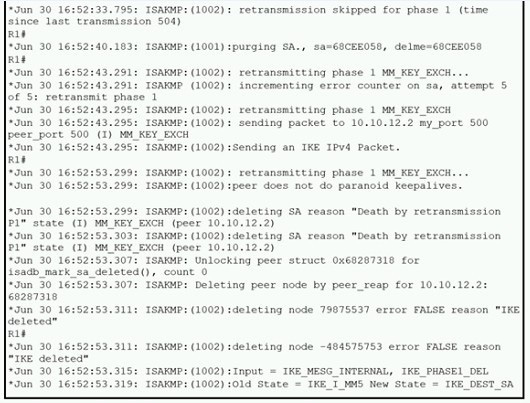
A network administrator configured a site-to-site VPN tunnel between two Cisco IOS routers, and hosts are unable to communicate between two sites of VPN. The network administrator runs the debug crypto isakmp sa command to track VPN status. What is the problem according to this command output?
A. hashing algorithm mismatch
B. encryption algorithm mismatch
C. authentication key mismatch
D. interesting traffic was not applied
What is a characteristic of a bridge group in ASA Firewall transparent mode?
A. It includes multiple interfaces and access rules between interfaces are customizable
B. It is a Layer 3 segment and includes one port and customizable access rules
C. It allows ARP traffic with a single access rule
D. It has an IP address on its BVI interface and is used for management traffic
Which statement describes a traffic profile on a Cisco Next Generation Intrusion Prevention System?
A. It allows traffic if it does not meet the profile.
B. It defines a traffic baseline for traffic anomaly deduction.
C. It inspects hosts that meet the profile with more intrusion rules.
D. It blocks traffic if it does not meet the profile.
Which two deployment modes does the Cisco ASA FirePower module support? (Choose two)
A. transparent mode
B. routed mode
C. inline mode
D. active mode
E. passive monitor-only mode
When Cisco and other industry organizations publish and inform users of known security findings and vulnerabilities, which name is used?
A. Common Security Exploits
B. Common Vulnerabilities and Exposures
C. Common Exploits and Vulnerabilities
D. Common Vulnerabilities, Exploits and Threats
What is a prerequisite when integrating a Cisco ISE server and an AD domain?
A. Place the Cisco ISE server and the AD server in the same subnet
B. Configure a common administrator account
C. Configure a common DNS server
D. Synchronize the clocks of the Cisco ISE server and the AD server
When a Cisco WSA checks a web request, what occurs if it is unable to match a user- defined policy?
A. It blocks the request.
B. It applies the global policy.
C. It applies the next identification profile policy.
D. It applies the advanced policy.
An engineer is implementing Cisco CES in an existing Microsoft Office 365 environment and must route inbound email to Cisco CE.. record must be modified to accomplish this task?
A. CNAME
B. MX
C. SPF
D. DKIM