350-401 Online Practice Questions and Answers
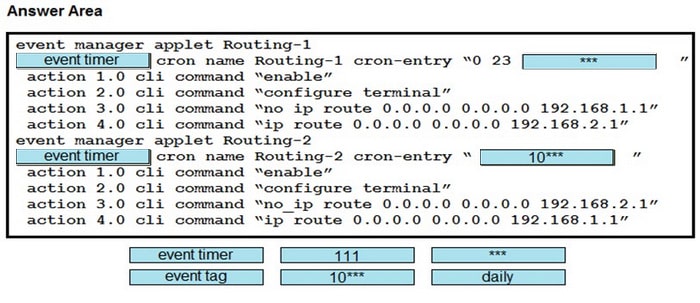
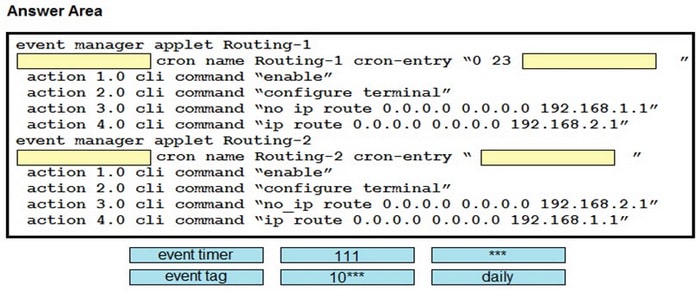
DRAG DROP
Drag and drop the snippets onto the blanks within the code to construct a script that changes the routing from gateway 1 to gateway 2 from 11:00 p.m. to 12:00 a.m. (2300 to 2400) only, daily. Not all options are used, and some options may be used twice.
Select and Place:
An engineer must create an EEM applet that sends a syslog message in the event a change happens in the network due to trouble with an OSPF process. Which action should the engineer use?

A. action 1 syslog msg "OSPF ROUTING ERROR"
B. action 1 syslog send "OSPF ROUTING ERROR"
C. action 1 syslog pattern "OSPF ROUTING ERROR"
D. action 1syslog write "OSPF ROUTING ERROR"
Refer to the exhibit.
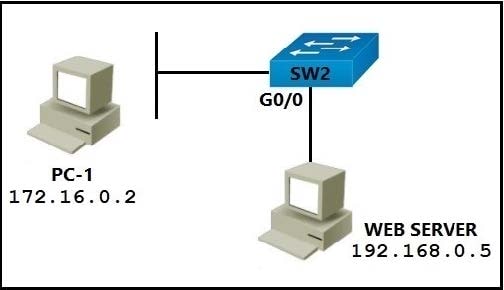
Refer to the exhibit. PC-1 must access the web server on port 8080. To allow this traffic, which statement must be added to an access control list that is applied on SW2 port G0/0 in the inbound direction?
A. permit host 172.16.0.2 host 192.168.0.5 eq 8080
B. permit host 192.168.0.5 host 172.16.0.2 eq 8080
C. permit host 192.168.0.5 eq 8080 host 172.16.0.2
D. permit host 192.168.0.5 it 8080 host 172.16.0.2
Refer to the exhibit.
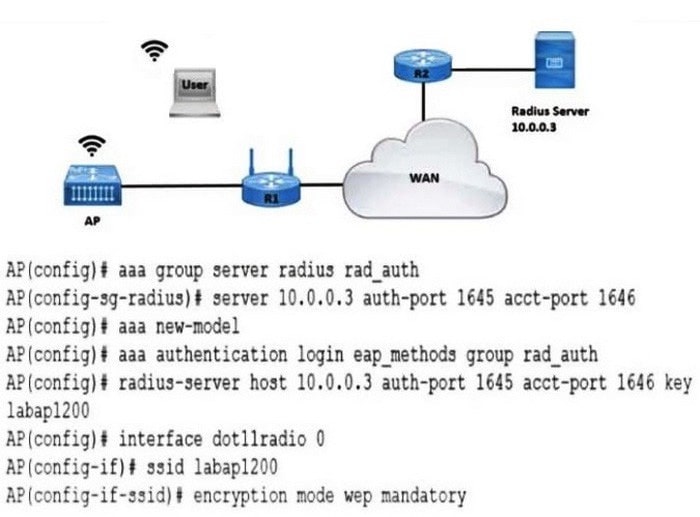
A company requires that all wireless users authenticate using dynamic key generation. Which configuration must be applied?
A. AP(config-if-ssid)# authentication open wep wep_methods
B. AP(config-if-ssid)# authentication dynamic wep wep_methods
C. AP(config-if-ssid)# authentication dynamic open wep_dynamic
D. AP(config-if-ssid)# authentication open eap eap_methods
Which resource is able to be shared among virtual machines deployed on the same physical server?
A. disk
B. operating system
C. VM configuration file
D. applications

What is a benefit of using segmentation with TrustSec?
A. Integrity checks prevent data from being modified in transit.
B. Packets sent between endpoints on a LAN are encrypted using symmetric key cryptography.
C. Security group tags enable network segmentation.
D. Firewall rules are streamlined by using business-level profiles.
An engineer must implement a configuration to allow a network administrator to connect to the console port of a router and authenticate over the network. Which command set should the engineer use?
A. aaa new-model aaa authentication login default enable
B. aaa new-model aaa authentication login console local
C. aaa new-model aaa authentication login console group radius
D. aaa new-model aaa authentication enable default
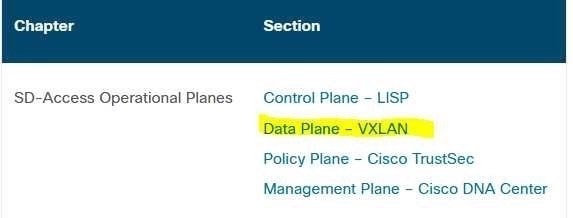
Which tunneling technique is used when designing a Cisco SD-Access fabric data plane?
A. LISP
B. VRF Lite
C. VRF
D. VXLAN
Which unit is used to express the signal-to-noise ratio?
A. mW
B. db
C. amp
D. dbm
A network administrator need to configure Netflow on the devices in his network. He has Source IP Address, Destination IP Address, Source Port number and Destination port number. What additional information do he need to configure Netflow?
A. Layer 3 Protocol type
B. Encryption type
C. ToS (Type of Service) byte
D. Input Logical Interface
E. Hashing Algorithm
F. Transform-set details