312-50V8 Online Practice Questions and Answers
When you are getting informationabout a web server, it is very important to know the HTTP Methods (GET, POST, HEAD, PUT, DELETE, TRACE) that are available because there are two critical methods (PUT and DELETE). PUT can upload a file to the server and DELETE can delete a file from the server. You can detect all these methods (GET, POST, HEAD, PUT, DELETE, TRACE) using NMAP script engine.
What nmap script will help you with this task?
A. http enum
B. http-git
C. http-headers
D. http-methods
You have compromised a server and successfully gained a root access. You want to pivot and pass traffic undetected over the network and evade any possible Intrusion Detection System.
What is the best approach?
A. Install and use Telnet to encrypt all outgoing traffic from this server.
B. Install Cryptcat and encrypt outgoing packets from this server
C. Use Alternate Data Streams to hide the outgoing packets from this server.
D. Use HTTP so that all traffic can be routed via a browser, thus evading the internal Intrusion Detection Systems.
Null sessions are un-authenticated connections (not using a username or password.) to an NT or 2000 system.
Which TCP and UDP ports must you filter to check null sessions on your network?
A. 137 and 139
B. 137 and 443
C. 139 and 443
D. 139 and 445
What is the essential difference between an `Ethical Hacker' and a `Cracker'?
A. The ethical hacker does not use the same techniques or skills as a cracker.
B. The ethical hacker does it strictly for financial motives unlike a cracker.
C. The ethical hacker has authorization from the owner of the target.
D. The ethical hacker is just a cracker who is getting paid.
How do employers protect assets with security policies pertaining to employee surveillance activities?
A. Employers promote monitoring activities of employees as long as the employees demonstrate trustworthiness.
B. Employers use informal verbal communication channels to explain employee monitoring activities to employees.
C. Employers use network surveillance to monitor employee email traffic,network access,and to record employee keystrokes.
D. Employers provide employees written statements that clearly discuss the boundaries of monitoring activities and consequences.
Which of the following processes of PKI (Public Key Infrastructure) ensures that a trust relationship exists and that a certificate is still valid for specific operations?
A. Certificate issuance
B. Certificate validation
C. Certificate cryptography
D. Certificate revocation
Which of the following statements are true regarding N-tier architecture? (Choose two.)
A. Each layer must be able to exist on a physically independent system.
B. The N-tier architecture must have at least one logical layer.
C. Each layer should exchange information only with the layers above and below it.
D. When a layer is changed or updated,the other layers must also be recompiled or modified.
The following script shows a simple SQL injection. The script builds an SQL query by concatenating hard-coded strings together with a string entered by the user:
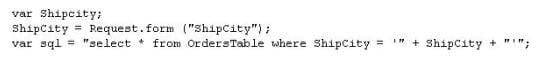
The user is prompted to enter the name of a city on a Web form. If she enters Chicago, the query
assembled by the script looks similar to the following:
SELECT * FROM OrdersTable WHERE ShipCity = 'Chicago'
How will you delete the OrdersTable from the database using SQL Injection?
A. Chicago'; drop table OrdersTable -
B. Delete table'blah'; OrdersTable -
C. EXEC; SELECT * OrdersTable > DROP -
D. cmdshell'; 'del c:\sql\mydb\OrdersTable' //
In Trojan terminology, what is required to create the executable file chess.exe as shown below?
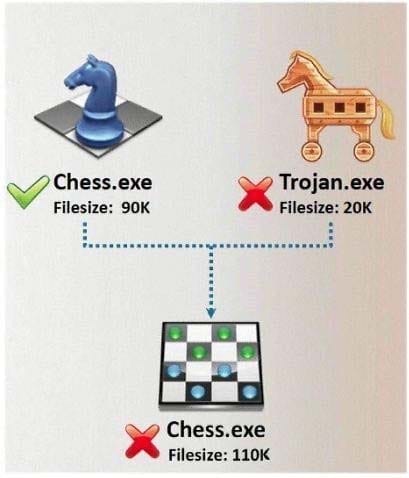
A. Mixer
B. Converter
C. Wrapper
D. Zipper
A Buffer Overflow attack involves:
A. Using a trojan program to direct data traffic to the target host's memory stack
B. Flooding the target network buffers with data traffic to reduce the bandwidth available to legitimate users
C. Using a dictionary to crack password buffers by guessing user names and passwords
D. Poorly written software that allows an attacker to execute arbitrary code on a target system