312-50V7 Online Practice Questions and Answers
The programmers on your team are analyzing the free, open source software being used to run FTP services on a server in your organization. They notice that there is excessive number of functions in the source code that might lead to buffer overflow. These C++ functions do not check bounds. Identify the line in the source code that might lead to buffer overflow?
A. 9A.9
B. 17B.17
C. 20C.20
D. 32D.32
E. 35E.35
Which of the following steganography utilities exploits the nature of white space and allows the user to conceal information in these white spaces?
A. Image Hide
B. Snow
C. Gif-It-Up
D. NiceText
Neil is closely monitoring his firewall rules and logs on a regular basis. Some of the users have complained to Neil that there are a few employees who are visiting offensive web site during work hours, without any consideration for others. Neil knows that he has an up-to-date content filtering system and such access should not be authorized. What type of technique might be used by these offenders to access the Internet without restriction?
A. They are using UDP that is always authorized at the firewall
B. They are using HTTP tunneling software that allows them to communicate with protocols in a way it was not intended
C. They have been able to compromise the firewall, modify the rules, and give themselves proper access
D. They are using an older version of Internet Explorer that allow them to bypass the proxy server
Buffer X in an Accounting application module for Brownies Inc. can contain 200 characters. The programmer makes an assumption that 200 characters are more than enough. Because there were no proper boundary checks being conducted, Bob decided to insert 400 characters into the 200-character buffer. (Overflows the buffer). Below is the code snippet: How can you protect/fix the problem of your application as shown above?

A. Because the counter starts with 0, we would stop when the counter is less than 200
B. Because the counter starts with 0, we would stop when the counter is more than 200
C. Add a separate statement to signify that if we have written less than 200 characters to the buffer, the stack should stop because it cannot hold any more data
D. Add a separate statement to signify that if we have written 200 characters to the buffer, the stack should stop because it cannot hold any more data
You generate MD5 128-bit hash on all files and folders on your computer to keep a baseline check for security reasons?
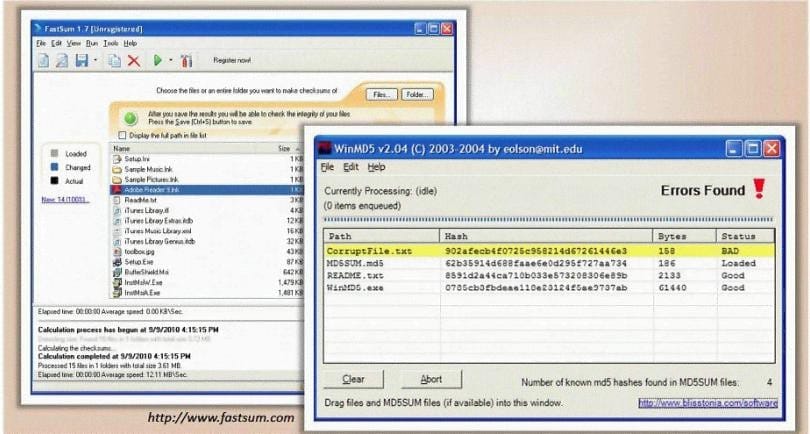
What is the length of the MD5 hash?
A. 32 character B. 64 byte
C. 48 char
D. 128 kb
Which of the following Exclusive OR transforms bits is NOT correct?
A. 0 xor 0 = 0
B. 1 xor 0 = 1
C. 1 xor 1 = 1
D. 0 xor 1 = 1
A company firewall engineer has configured a new DMZ to allow public systems to be located away from the internal network. The engineer has three security
zones set:
Untrust (Internet) (Remote network = 217.77.88.0/24)
DMZ (DMZ) (11.12.13.0/24)
Trust (Intranet) (192.168.0.0/24)
The engineer wants to configure remote desktop access from a fixed IP on the remote network to a remote desktop server in the DMZ. Which rule would best fit
this requirement?
A. Permit 217.77.88.0/24 11.12.13.0/24 RDP 3389
B. Permit 217.77.88.12 11.12.13.50 RDP 3389
C. Permit 217.77.88.12 11.12.13.0/24 RDP 3389
D. Permit 217.77.88.0/24 11.12.13.50 RDP 3389
Which of the following processes of PKI (Public Key Infrastructure) ensures that a trust relationship exists and that a certificate is still valid for specific operations?
A. Certificate issuance
B. Certificate validation
C. Certificate cryptography
D. Certificate revocation
How can rainbow tables be defeated?
A. Password salting
B. Use of non-dictionary words
C. All uppercase character passwords
D. Lockout accounts under brute force password cracking attempts
Company A and Company B have just merged and each has its own Public Key Infrastructure (PKI). What must the Certificate Authorities (CAs) establish so that the private PKIs for Company A and Company B trust one another and each private PKI can validate digital certificates from the other company?
A. Poly key exchange
B. Cross certification
C. Poly key reference
D. Cross-site exchange