312-49V10 Online Practice Questions and Answers
Data files from original evidence should be used for forensics analysis
A. True
B. False
What is the First Step required in preparing a computer for forensics investigation?
A. Do not turn the computer off or on, run any programs, or attempt to access data on a computer
B. Secure any relevant media
C. Suspend automated document destruction and recycling policies that may pertain to any relevant media or users at Issue
D. Identify the type of data you are seeking, the Information you are looking for, and the urgency level of the examination
You have been asked to investigate the possibility of computer fraud in the finance department of a company. It is suspected that a staff member has been committing finance fraud by printing cheques that have not been authorized. You have exhaustively searched all data files on a bitmap image of the target computer, but have found no evidence. You suspect the files may not have been saved. What should you examine next in this case?
A. The registry
B. The swapfile
C. The recycle bin
D. The metadata
You are using DriveSpy, a forensic tool and want to copy 150 sectors where the starting sector is 1709 on the primary hard drive. Which of the following formats correctly specifies these sectors?
A. 0:1000, 150
B. 0:1709, 150
C. 1:1709, 150
D. 0:1709-1858
What type of attack occurs when an attacker can force a router to stop forwarding packets by flooding the router with many open connections simultaneously so that all the hosts behind the router are effectively disabled?
A. ARP redirect
B. Physical attack
C. Digital attack
D. Denial of service
Using Internet logging software to investigate a case of malicious use of computers, the investigator comes across some entries that appear odd.
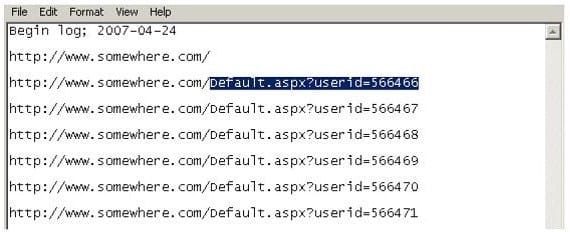
From the log, the investigator can see where the person in question went on the Internet. From the log, it
appears that the user was manually typing in different user ID numbers.
What technique this user was trying?
A. Parameter tampering
B. Cross site scripting
C. SQL injection
D. Cookie Poisoning
Office documents (Word, Excel, PowerPoint) contain a code that allows tracking the MAC, or unique identifier, of the machine that created the document.
What is that code called?
A. the Microsoft Virtual Machine Identifier
B. the Personal Application Protocol
C. the Globally Unique ID
D. the Individual ASCII String
When a file is deleted by Windows Explorer or through the MS-DOS delete command, the operating system inserts _______________ in the first letter position of the filename in the FAT database.
A. A Capital X
B. A Blank Space
C. The Underscore Symbol
D. The lowercase Greek Letter Sigma (s)
Which of the following protocols allows non-ASCII files, such as video, graphics, and audio, to be sent through the email messages?
A. MIME
B. BINHEX
C. UT-16
D. UUCODE
A section of your forensics lab houses several electrical and electronic equipment. Which type of fire extinguisher you must install in this area to contain any fire incident?
A. Class B
B. Class D
C. Class C
D. Class A