312-49 Online Practice Questions and Answers
A(n) _____________________ is one that's performed by a computer program rather than the attacker manually performing the steps in the attack sequence.
A. blackout attack
B. automated attack
C. distributed attack
D. central processing attack
When examining a hard disk without a write-blocker, you should not start windows because Windows will write data to the:
A. Recycle Bin
B. MSDOS.sys
C. BIOS
D. Case files
Which of the following refers to the data that might still exist in a cluster even though the original file has been overwritten by another file?
A. Sector
B. Metadata
C. MFT
D. Slack Space
A law enforcement officer may only search for and seize criminal evidence with _______________________, which are facts or circumstances that would lead a reasonable person to believe a crime has been committed or is about to be committed, evidence of the specific crime exists and the evidence of the specific crime exists at the place to be searched.
A. Mere Suspicion
B. A preponderance of the evidence
C. Probable cause D. Beyond a reasonable doubt
As a CHFI professional, which of the following is the most important to your professional reputation?
A. Your Certifications
B. The correct, successful management of each and every case
C. The free that you charge
D. The friendship of local law enforcement officers
What must an investigator do before disconnecting an iPod from any type of computer?
A. Unmount the iPod
B. Mount the iPod
C. Disjoin the iPod D. Join the iPod
Jack Smith is a forensics investigator who works for Mason Computer Investigation Services. He is investigating a computer that was infected by Ramen Virus.
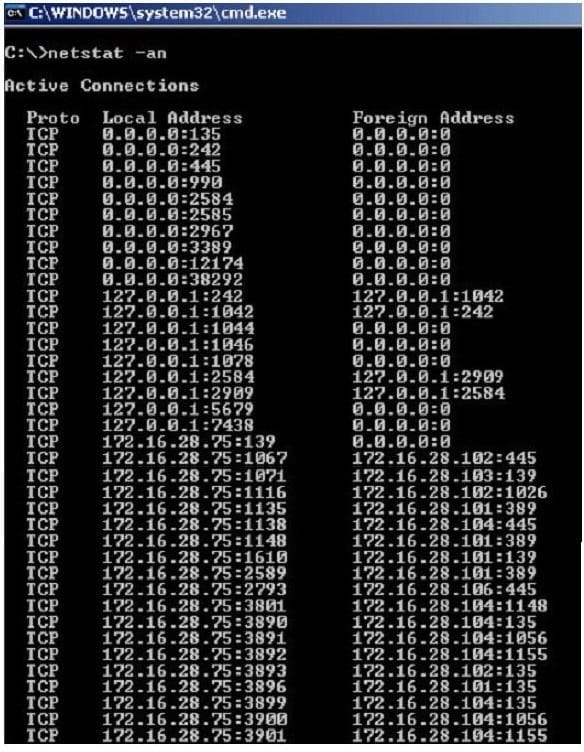
He runs the netstat command on the machine to see its current connections. In the following screenshot, what do the 0.0.0.0 IP addresses signify?
A. Those connections are established
B. Those connections are in listening mode
C. Those connections are in closed/waiting mode
D. Those connections are in timed out/waiting mode
Which of the following Android libraries are used to render 2D (SGL) or 3D (OpenGL/ES) graphics content to the screen?
A. OpenGL/ES and SGL
B. Surface Manager
C. Media framework
D. WebKit
You are assigned a task to examine the log files pertaining to MyISAM storage engine. While examining, you are asked to perform a recovery operation on a MyISAM log file. Which among the following MySQL Utilities allow you to do so?
A. mysqldump
B. myisamaccess
C. myisamlog
D. myisamchk
Centralized binary logging is a process in which many websites write binary and unformatted log data to a single log file. What extension should the investigator look to find its log file?
A. .cbl
B. .log
C. .ibl
D. .txt