300-820 Online Practice Questions and Answers
Refer to the exhibit.
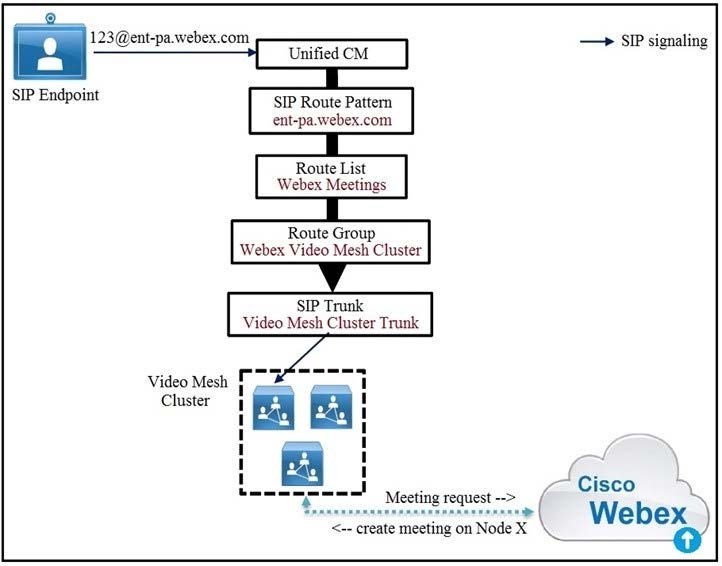
Cisco Unified Communications Manager routes the call via the Webex Meetings route list and route group to the Video Mesh cluster Node#1 in the Video Mesh cluster is hosting the meeting and has reached full capacity, but other nodes in the cluster still have spare capacity.
What happens to the participant's call?
A. Another node in the cluster is used and an intra-cluster cascade between the two Video Mesh nodes is formed.
B. The call is queued.
C. The call fails.
D. Another node in the cluster is used and an intra-cluster cascade between Webex and the new Video Mesh node is formed.
A Jabber user is being prompted to trust the Expressway-E certificate when using Mobile and Remote Access. The administrator has validated that the Expressway-E certificate is being trusted by the machine running the Jabber client. What else can be done to solve this problem?
A. Create a new CSR with new information on the SAN field.
B. Include Cisco Unified Communications Manager registration domain in the Expressway-E certificate as a SAN.
C. Change the domain name.
D. Change the FQDN of the Expressway.
An organization with a domain name of example.com.
Which two SRV records are valid for a SIP and H.323 communication? (Choose two.)
A. _sips._tcp.example.com
B. _sips._udp.example.com
C. _h323ls._udp.example com
D. _h323ls._tcp.example.com
E. _collab-edge._tls.example.com
Which zone is required on a B2B deployment between Expressway-C and Expressway-E?
A. traversal zone
B. DNS zone
C. default zone
D. neighbor zone
Which role does Call Policy play when preventing toll fraud on Expressways?
A. It controls which calls are allowed, which calls are rejected, and which calls are redirected to a different destination.
B. It changes the calling and called number on a call.
C. It changes the audio protocol used by a call through Expressways.
D. It changes the audio codec used in a call through Expressways.
What happens to the encrypted signaling traffic of a collaboration device if you place it inside a firewall with private IP addresses and try to make a call over IP without any collaboration infrastructure?
A. The signaling makes it back to the endpoint because the firewall is an application layer gateway and provides address translation.
B. Encrypted IP traffic for collaboration devices always is trusted by the firewall.
C. The signaling does not make it back to the endpoint because the firewall cannot inspect encrypted traffic.
D. The signaling makes it back to the endpoint because the endpoint sent the private address to the external endpoint.
When a Cisco Webex Video Mesh Node is configured for an organization, which process does the Webex Teams client use to discover the optimal bridging resource?
A. the lowest STUN round-trip delay to each node and cloud
B. a reachable Video Mesh Node and then overflows to the cloud, if needed
C. the SIP delay header during call setup
D. an HTTPS speed and latency test to each node and the cloud
Which two licenses are required for the Expressway B2B feature to work? (Choose two)
A. Traversal Server
B. Advanced Networking
C. Device Provisioning
D. Rich Media Sessions
E. TURN Relays
When designing the call control on a Cisco Expressway Core, which is the sequence of dial plan functions?
A. transforms, CPL, user policy, search rules
B. search rules, zones, local zones
C. DNS zone, local zone, search rules
D. search rules, transforms
What is a description of an Interactive Connectivity Establishment?
A. It is used by B2BUA to keep the firewall ports opened for inbound/outbound calls.
B. It allows Mobile and Remote Access endpoints to connect video calls signaling peer-to-peer.
C. It allows calling external endpoints with reduced overhead under VPN connections.
D. It is used to find the best media path between network elements in traversal calls.