300-730 Online Practice Questions and Answers
Which requirement is needed to use local authentication for Cisco AnyConnect Secure Mobility Clients that connect to a FlexVPN server?
A. use of certificates instead of username and password
B. EAP-AnyConnect
C. EAP query-identity
D. AnyConnect profile
What are two functions of ECDH and ECDSA? (Choose two.)
A. nonrepudiation
B. revocation
C. digital signature
D. key exchange
E. encryption
A user is trying to log in to a Cisco ASA using the clientless SSLVPN feature and receives the error message "clientless (browser) SSLVPN access is not allowed". Which step should the Cisco ASA administrator take to resolve this issue?
A. Enable the clientless VPN protocol on the group policy.
B. Validate that the correct license is in use on the ASA for WebVPN.
C. Increase the number of simultaneous logins allowed on the group policy.
D. Verify that a user account exists in the local AAA database for the user.
Refer to the exhibit.
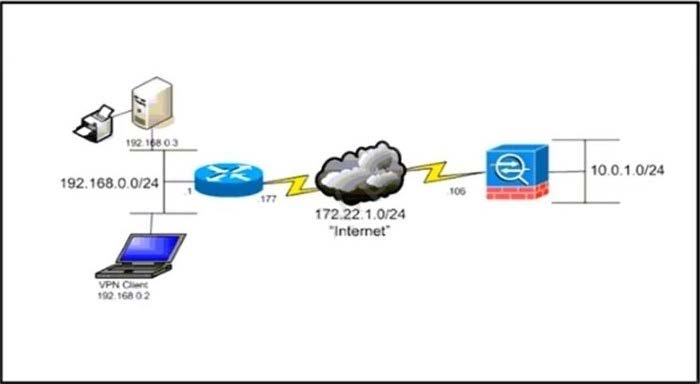
The network administrator must allow the Cisco AnyConnect Secure Mobility Client to securely access the corporate resources via IKEv2 and print locally. Traffic that is destined for the Internet must still be tunneled to the Cisco ASA. Which configuration does the administrator use to accomplish this goal?
A. Split exclude policy with a deny for 192.168.0.3/32.
B. Split exclude policy with a permit for 0.0.0.0/32.
C. Tunnel all policy.
D. Split include policy with a permit for 192.168.0.0/24.
Which VPN technology minimizes the impact on VPN performance when encrypting multicast traffic on a Private WAN?
A. DMVPN
B. IPsec VPN
C. FlexVPN
D. GETVPN
A network engineer must design a remote access solution to allow contractors to access internal servers. These contractors do not have permissions to install applications on their computers. Which VPN solution should be used in this design?
A. IKEv2 AnyConnect
B. Clientless
C. Port forwarding
D. SSL AnyConnect
While troubleshooting, an engineer finds that the show crypto isakmp sa command indicates that the last state of the tunnel is MM_KEY_EXCH. What is the next step that should be taken to resolve this issue?
A. Verify that the ISAKMP proposals match.
B. Ensure that UDP 500 is not being blocked between the devices.
C. Correct the peer's IP address on the crypto map.
D. Confirm that the pre-shared keys match on both devices.
What are two purposes of the key server in Cisco IOS GETVPN? (Choose two.)
A. to download encryption keys
B. to maintain encryption policies
C. to distribute routing information
D. to encrypt data traffic
E. to authenticate group members
On an ASA with multiple connection profiles for different departments, what is the best design to ensure that AnyConnect users are assigned the correct connection profile based on their department and do not have the ability to choose a different connection profile?
A. group URL
B. group alias
C. dynamic access policy
D. certificate mapping
A network administrator is deploying a Cisco IPS appliance and needs it to operate initially without affecting traffic flows. It must also collect data to provide a baseline of unwanted traffic before being reconfigured to drop it. Which Cisco IPS mode meets these requirements?
A. failsafe
B. inline tap
C. promiscuous
D. bypass