300-725 Online Practice Questions and Answers
Which two features can be used with an upstream and downstream Cisco WSA web proxy to have the upstream WSA identify users by their client IP address? (Choose two.)
A. X-Forwarded-For
B. high availability
C. web cache
D. via
E. IP spoofing
Which two configuration options are available on a Cisco WSA within a decryption policy? (Choose two.)
A. Pass Through
B. Warn
C. Decrypt
D. Allow
E. Block
Which two parameters are mandatory to control access to websites with proxy authentication on a Cisco WSA? (Choose two.)
A. External Authentication
B. Identity Enabled Authentication
C. Transparent User Identification
D. Credential Encryption
E. Authentication Realm
Which two types of reports are scheduled on the Cisco WSA to analyze traffic? (Choose two.)
A. Layer 3 traffic monitor
B. URL categories
C. host statistics
D. application visibility
E. system capacity
What must be configured first when creating an access policy that matches the Active Directory group?
A. authentication, authorization, and accounting of groups
B. FQDN specification
C. authentication realm
D. authorized groups specification
Which IP address and port are used by default to run the system setup wizard?
A. http://192.168.42.42:80
B. https://192.168.42.42:8080
C. https://192.168.42.10:8443
D. http://192.168.43.42:8080
A network administrator noticed that all traffic that is redirected to the Cisco WSA from the Cisco ASA firewall cannot get to the Internet in a Transparent proxy environment using WCCP. Which troubleshooting action must be taken on the CLI to make sure that WCCP communication is not failing?
A. Disable WCCP to see if the WCCP service is causing the issue
B. Explicitly point the browser to the proxy
C. Ping the WCCP device
D. Check WCCP logs in debug mode
Which type of FTP proxy does the Cisco WSA support?
A. non-native FTP
B. FTP over UDP tunneling
C. FTP over HTTP
D. hybrid FTP
When an access policy is created, what is the default option for the Application Settings?
A. Use Global Policy Applications Settings
B. Define the Applications Custom Setting
C. Set all applications to Block
D. Set all applications to Monitor
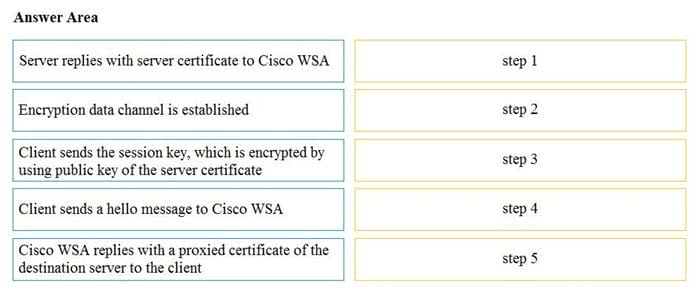
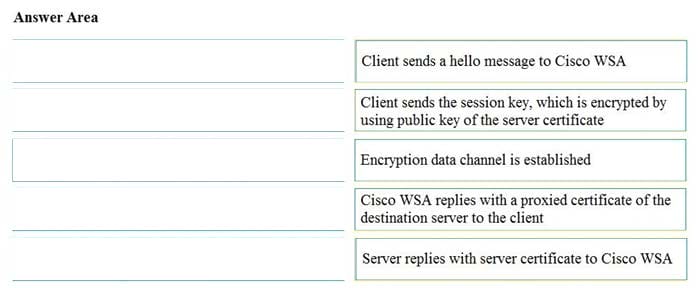
DRAG DROP
Drag and drop the actions from the left into the correct order on the right in which they occur as an HTTPS session passes through the Cisco WSA.
Select and Place: