300-635 Online Practice Questions and Answers
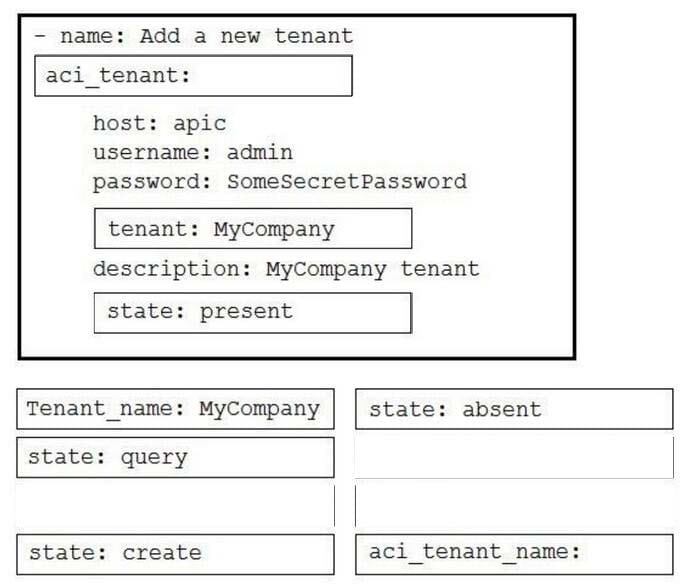
DRAG DROP
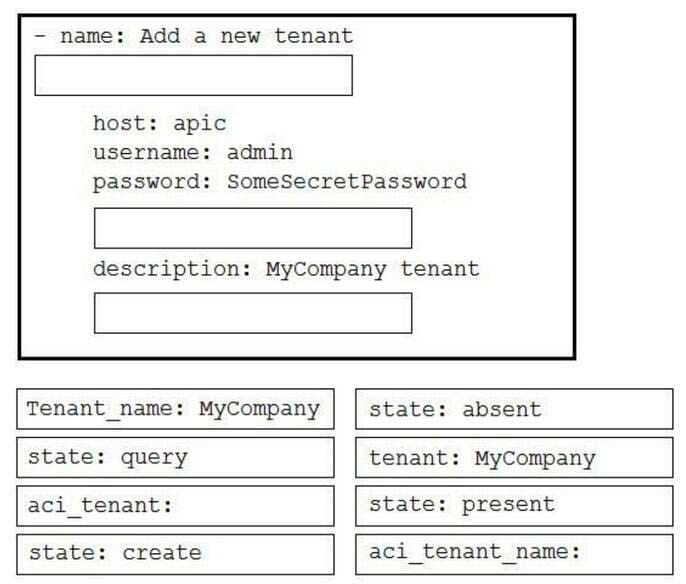
Drag and drop the code to complete an Ansible playbook that creates a new tenant. Not all options are used.
Select and Place:
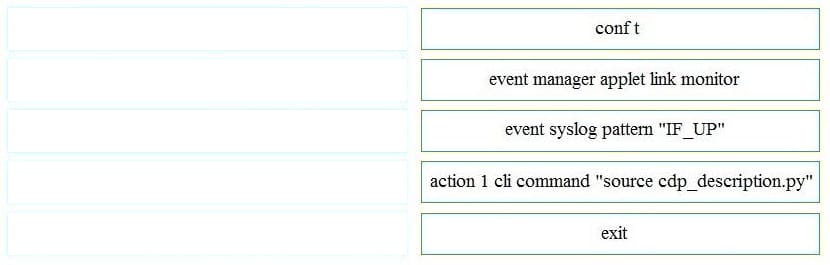
DRAG DROP
After a Cisco Nexus switch interface is enabled and in the up state, an engineer must automate the configuration of the interface descriptions using the EEM Python Module.
Drag and drop the steps the engineer must take from the left into the correct order on the right.
Select and Place:

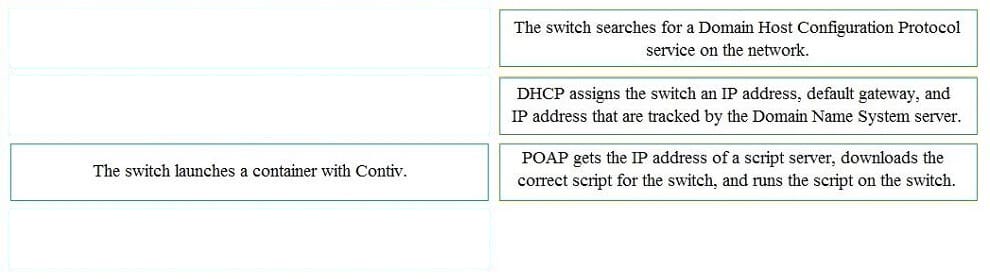
DRAG DROP
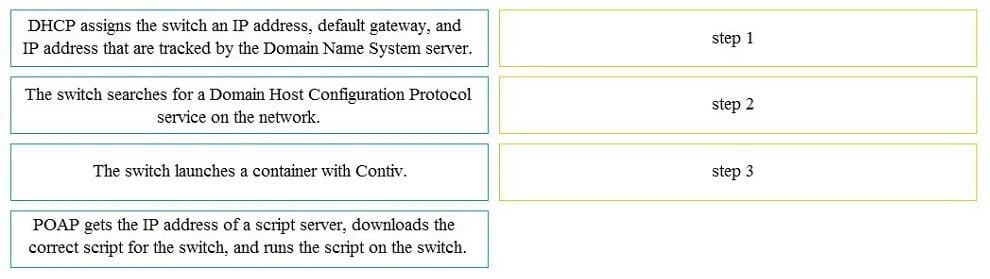
When a switch boots it does not find its startup-config file. Drag and drop the steps that Power-On Auto Provisioning goes through to configure the switch for remote management from the left into the correct order on the right. Not all options are used.
Select and Place:
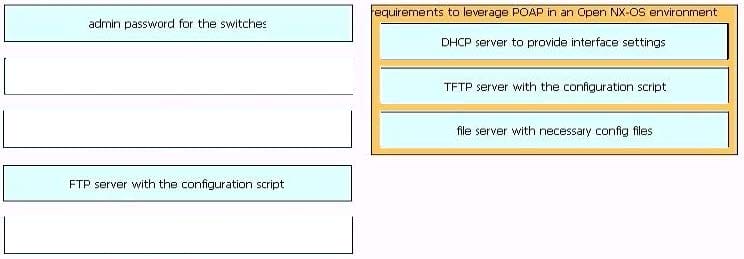
DRAG DROP
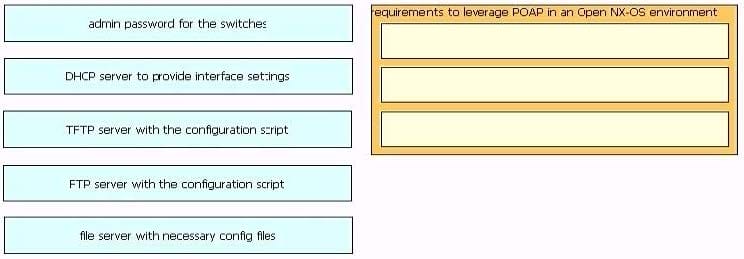
Drag and drop the requirements from the left that are needed to leverage POAP in an Open Cisco NX- OS environment onto the right. Not all options are used.
Select and Place:
Which two statements about gRPC are true? (Choose two.)
A. It is an IETF draft.
B. It is an IETF standard.
C. It runs over SSH.
D. It is an open source initiative.
E. It runs over HTTPS.
How should the Kubernetes manifests be modified to allow Kubernetes environment integration with Cisco ACI?
A. The metadata section must contain the Cisco APIC management IP.
B. The manifest does not have to be changed, but the Kubernetes object is not discovered by Cisco ACI if this is not defined in the manifest.
C. The manifests must include ACI EPG reference.
D. No change is needed to perform this action.
Which two bootstrap technologies are supported by Cisco NX-OS platforms? (Choose two.)
A. iPXE
B. PNP
C. POAP
D. BOOTP
E. DHCP
When the Cisco bigmuddy-network-telemetry-collector from GitHub is used, which command displays only the message headers?
A. --print
B. --all
C. --brief
D. --print-all
Which two statements describe the authentication method used with Cisco Intersight REST API Requests? (Choose two.)
A. The REST API request contains a base64-encoded signature of the message content and headers.
B. The REST API request message body is encoded as a SHA384 hash and then signed with the API Key ID.
C. The Cisco Intersight Web service verifies the signature of incoming request with the RSA public key for the API Key ID.
D. The incoming REST API request is challenged by the Cisco Intersight Web service with a request for the RSA private key.
E. The message body is encoded as a SHA256 hash if the message body is not empty and then signed with the API Key ID.
Refer to the exhibit.
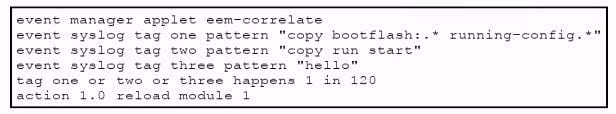
What results from the EEM script that runs on a Cisco Nexus 9000 switch?
A. Module 1 is reloaded if one of the specified console patterns occurs within 120 seconds.
B. Module 1 is reloaded if one of the specified syslog patterns occurs within 120 seconds.
C. Module 1 is reloaded if all of the specified syslog patterns occur within 120 seconds.
D. The message "reload module 1" is printed if one of the specified syslog patterns occurs within 120 seconds