300-630 Online Practice Questions and Answers
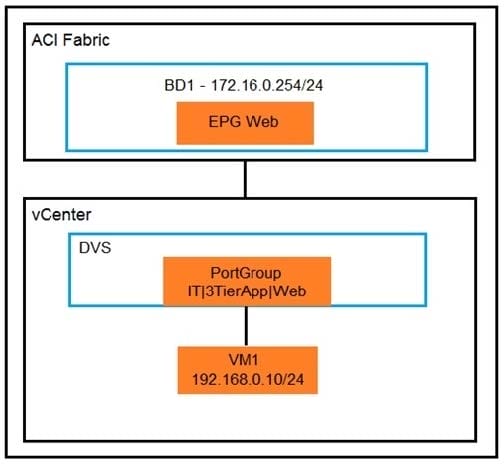
An organization migrates its virtualized servers from a legacy environment to Cisco ACI. VM1 is incorrectly attached to PortGroup IT|3TierApp|Web. Which action limits IP address learning in BD1?
A. Enable Enforce Subnet Check
B. Enable Rouge Endpoint Control
C. Enable GARP-based EP Move Detection Mode
D. Disable Remote EP Learn
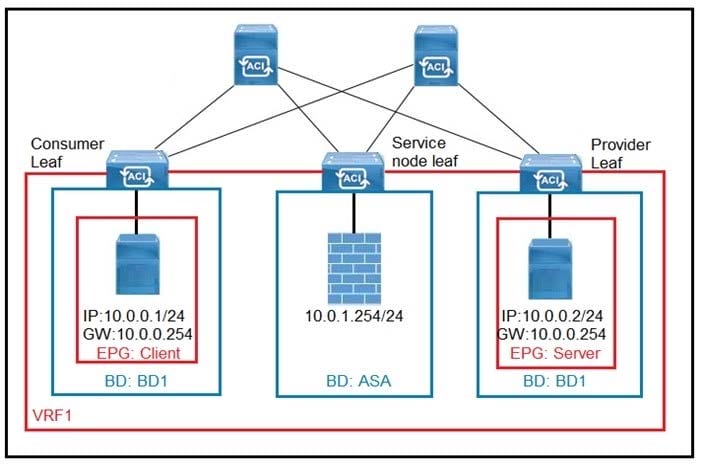
Refer to the exhibit. What must be configured in the service graph to redirect HTTP traffic between the EPG client and EPG server to go through the Cisco ASA firewall?
A. contract filter to allow ARP and HTTP
B. precise filter to allow only HTTP traffic
C. contract with no filter
D. permit-all contract filter
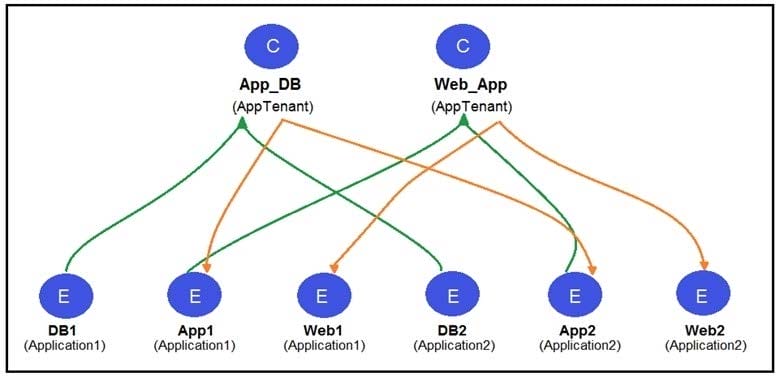
Refer to the exhibit. Two application profiles are configured in the same tenant and different VRFs. Which contract scope is configured to allow communication between the two application profiles?
A. global
B. VRF
C. application
D. tenant
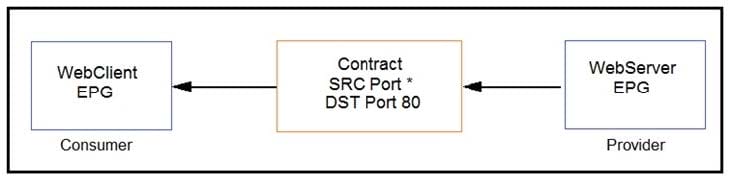
Refer to the exhibit. Which combination of flags in the Cisco ACI contract allows a client in WebClient EPG to establish an HTTP connection toward a server in WebServer EPG?
A. Apply Both Direction ENABLED and Reverse Port Filter ENABLED
B. Apply Both Direction DISABLED and Reverse Port Filter DISABLED
C. Apply Both Direction DISABLED and Reverse Port Filter ENABLED
D. Apply Both Direction ENABLED and Reverse Port Filter DISABLED
Which firewall connection allows for the integration of service nodes in transparent mode with a Cisco ACI Multi-Pod setup?
A. active-standby mode across pods
B. active-active mode per pods for communication between internal endpoints
C. active-standby mode per pods for communication between endpoints and external networks
D. active-active mode across pods
An engineer configures a new Cisco ACI Multi-Pod setup. Which action should be taken for fabric discovery to be successful for the nodes in Pod 2?
A. Select the Route Reflector field in Pod Peering
B. Enable the DSCP class-cos translation policy for Layer 3 traffic
C. Configure POD 2 Data Plane TEP under the Pod Connection Profile
D. Add the IPN subnet under the Fabric External Routing Profile

Refer to the exhibit. A network engineer configures a Layer 4 to Layer 7 device for an outside routed firewall that is connected to POD-1 inside a Cisco ACI fabric that consists of two pods. All traffic from POD-1 or POD-2 that uses the L3Out should pass through the routed firewall. Which Function Type must be implemented in the service graph for POD-2 to use L3Out?
A. GoThrough
B. L1
C. GoTo
D. L2
In a Cisco ACI Multi-Site fabric, the Inter-Site BUM Traffic Allow option is enabled in a specific stretched bridge domain. What is used to forward BUM traffic to all endpoints in the same broadcast domain?
A. ingress replication on the spines in the source site
B. egress replication on the source leaf switches
C. egress replication on the destination leaf switches
D. ingress replication on the spines in the destination site
What is a use of the Overlay Multicast TEP in Cisco ACI Multi-Site communication?
A. to perform headend replication
B. to act as the source IP for BUM traffic
C. to establish MP-BGP adjacencies with remote spines
D. to send and receive unicast VXLAN data plane traffic
A host that is connected to a Cisco ACI fabric leaf switch sends an ARP request. Which transmission method does the ingress switch use to send the ARP requests?
A. anycast
B. broadcast
C. multicast
D. unicast