300-215 Online Practice Questions and Answers
An engineer is investigating a ticket from the accounting department in which a user discovered an unexpected application on their workstation. Several alerts are seen from the intrusion detection system of unknown outgoing internet traffic from this workstation. The engineer also notices a degraded processing capability, which complicates the analysis process. Which two actions should the engineer take? (Choose two.)
A. Restore to a system recovery point.
B. Replace the faulty CPU.
C. Disconnect from the network.
D. Format the workstation drives.
E. Take an image of the workstation.
What is the steganography anti-forensics technique?
A. hiding a section of a malicious file in unused areas of a file
B. changing the file header of a malicious file to another file type
C. sending malicious files over a public network by encapsulation
D. concealing malicious files in ordinary or unsuspecting places
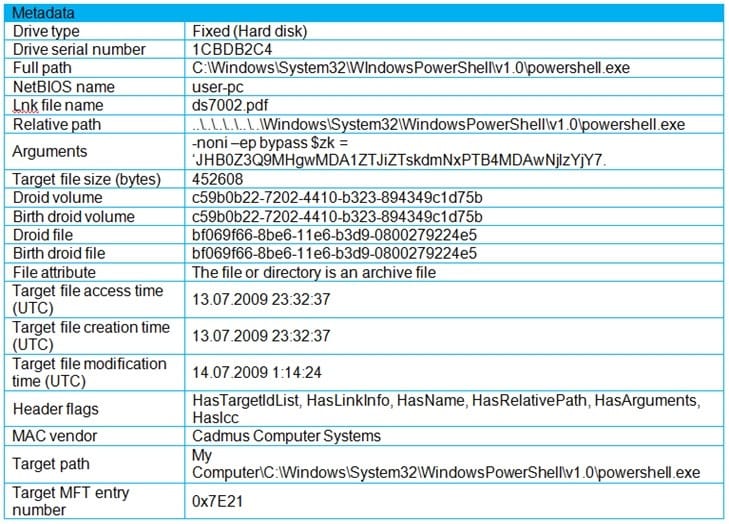
Refer to the exhibit. An engineer is analyzing a .LNK (shortcut) file recently received as an email attachment and blocked by email security as suspicious. What is the next step an engineer should take?
A. Delete the suspicious email with the attachment as the file is a shortcut extension and does not represent any threat.
B. Upload the file to a virus checking engine to compare with well-known viruses as the file is a virus disguised as a legitimate extension.
C. Quarantine the file within the endpoint antivirus solution as the file is a ransomware which will encrypt the documents of a victim.
D. Open the file in a sandbox environment for further behavioral analysis as the file contains a malicious script that runs on execution.
A threat actor attempts to avoid detection by turning data into a code that shifts numbers to the right four times. Which anti-forensics technique is being used?
A. encryption
B. tunneling
C. obfuscation
D. poisoning
Which magic byte indicates that an analyzed file is a pdf file?
A. cGRmZmlsZQ
B. 706466666
C. 255044462d
D. 0a0ah4cg
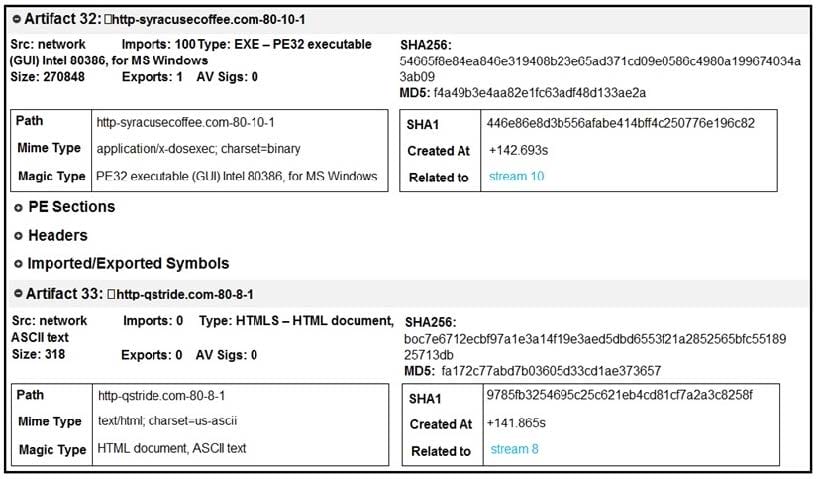
Refer to the exhibit. What do these artifacts indicate?
A. An executable file is requesting an application download.
B. A malicious file is redirecting users to different domains.
C. The MD5 of a file is identified as a virus and is being blocked.
D. A forged DNS request is forwarding users to malicious websites.
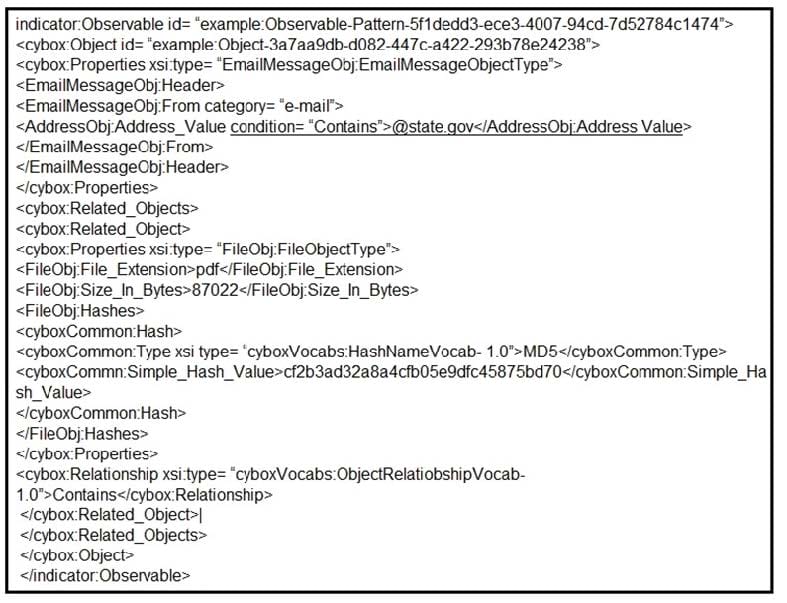
Refer to the exhibit. Which two actions should be taken as a result of this information? (Choose two.)
A. Update the AV to block any file with hash "cf2b3ad32a8a4cfb05e9dfc45875bd70".
B. Block all emails sent from an @state.gov address.
C. Block all emails with pdf attachments.
D. Block emails sent from [email protected] with an attached pdf file with md5 hash "cf2b3ad32a8a4cfb05e9dfc45875bd70".
E. Block all emails with subject containing "cf2b3ad32a8a4cfb05e9dfc45875bd70".
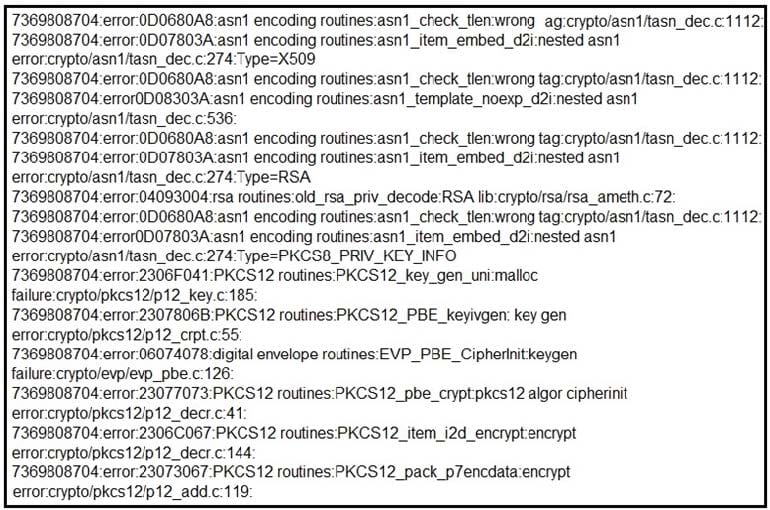
Refer to the exhibit. What should be determined from this Apache log?
A. A module named mod_ssl is needed to make SSL connections.
B. The private key does not match with the SSL certificate.
C. The certificate file has been maliciously modified
D. The SSL traffic setup is improper

Refer to the exhibit. According to the Wireshark output, what are two indicators of compromise for detecting an Emotet malware download? (Choose two.)
A. Domain name:iraniansk.com
B. Server: nginx
C. Hash value: 5f31ab113af08=1597090577
D. filename= "Fy.exe"
E. Content-Type: application/octet-stream
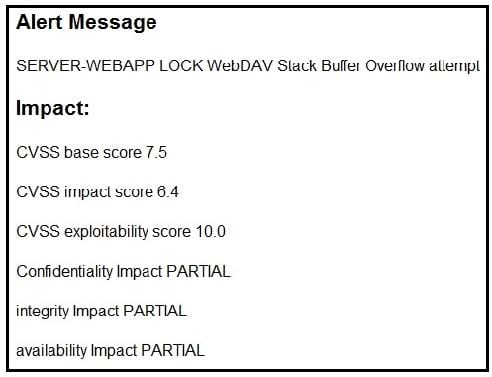
Refer to the exhibit. After a cyber attack, an engineer is analyzing an alert that was missed on the intrusion detection system. The attack exploited a vulnerability in a business critical, web-based application and violated its availability. Which two migration techniques should the engineer recommend? (Choose two.)
A. encapsulation
B. NOP sled technique
C. address space randomization
D. heap-based security
E. data execution prevention