2V0-651 Online Practice Questions and Answers
A View administrator needs to ensure that an environment is ready to use Smart Cards. The cards use certificates generated by a third-party Certificate Authority (CA). The administrator has verified that each certificate contains a UPN.
What must the administrator do to complete the preparation of the environment?
A. Import the root and intermediate CA certificates into the Trusted Root Certification Authorities group policy in Active Directory.
B. Import the root and intermediate CA certificates into the Trusted Root Certification Authorities store on the View Connection server.
C. Import the root and intermediate CA certificates into each user's Smart Card.
D. Enable Smart Card Authentication in the authentication settings in View Administrator.
Which two settings are required to prevent RDP access to a group of View desktops? (Choose two.)
A. Disable AllowDirectRDP.
B. Enable AllowDirectRDP.
C. Select the Pool Settings tab and select PCoIP as the default display protocol.
D. Select the Pool Settings tab and disable RDP as a possible display protocol.
A View environment consists of a Connection Server named connect-01 and a security server named security-01.
An administrator needs to configure RSA SecurID authentication for external users. Internal users must not be prompted for the RSA SecurID token code.
What should the administrator do?
A. Configure 2-factor authentication on the security-01 security server.
B. Configure 2-factor authentication on the connect-01 Connection Server.
C. Add a new Connection Server named connect-02 for internal users. Configure 2-factor authentication on the connect-01 Connection Server.
D. Add a new security server named security-02 for internal users. Configure 2-factor authentication on the security-01 security server.
An administrator is running a View Infrastructure with Linked Clones running on ESXi 5.x. Users should not be able to eject devices such as CD-ROMs from the virtual desktops.
What should the administrator do on the vSphere Client to prevent users from ejecting devices?
A. Right click on the parent image, and then in Edit Settings-->Options, disable Hot Add.
B. Modify the parent image .vmx file, and set devices.hotplug to False.
C. Modify the parent image .nvram file, and set devices.hotplug to False.
D. Right click on the parent image and then in Edit Settings-->Hardware, disable Hot Plug.
During the process of pairing a View security server, the administrator aborts the operation and attempts to run the pairing process again. The security server status displayed in the View Administrator dashboard is down, and remote users receive the following message when attempting to connect:
The View Connection Server authentication failed. No gateway is available to provide a secure connection to a desktop. Contact your network Administrator.
What should the administrator do to resolve the issue?
A. In the View Connection Server instance click More Commands>Specify a Security Server Pairing Password then enter a new password and install the security server again.
B. Run vdmadmin -S security_server_name and then install the security server again.
C. In the View Connection Server instance click More Commands>Specify a Security Server Pairing Passwords then enter a password and restart the View Connection Server service.
D. Run vdmadmin -S security_server_name and restart the View Connection Server service.
While deploying a View desktop pool, an administrator determines that the virtual desktops remain at a status of Customizing.
In the debug-timestamp.txt log file of the View Agent, the administrator finds the error message:
Debug - Unable to connect to JMS Server.com.vmware.vdi.agent.messageserver.Jmsmanager.a(SourceFile:238) javax.jms.JMSException:Unable to create a connection to:[ServerEntry, hostname, port=4001]
What should the administrator do to troubleshoot the connection problem?
A. Verify that the View Composer Guest Agent Server service is set Started on the virtual desktops.
B. Verify that the View Agent can communicate with the View Connection Server over port 4001.
C. Verify that the View Connection Server can resolve the DNS name of the vCenter Server.
D. Verify that the View Security Server can establish a connection using the AJP13 protocol over port 4001.
An administrator identifies PCoIP packet fragmentation on the network. The following items have been
discovered:
Network Path Maximum Transmission Unit (MTU) is 1200 PCoIP Traffic has Quality of Service (QoS)
What should the administrator do?
A. Set router buffers to tail drop.
B. Set router buffers to Weighted Random Early Detection (WRED).
C. Set PCoIP MTU to 1500
D. Set PCoIP MTU to 1100
An administrator needs to view Windows 7 Virtual Desktops from the vSphere Console while a user has a PCoIP session to the Virtual Desktop. When the administrator opens a vSphere Console to a Virtual Desktop, the Console screen is black.
The administrator enables the Session Variable Enable access to a PCoIP session from a vSphere console. After this change, a black screen still appears when the administrator opens a vSphere Console to the Virtual Desktops.
What is preventing the Virtual Desktop from showing in the vSphere Console?
A. The Virtual Desktop Hardware Version is 7.
B. The Virtual Desktop Hardware Version is 8.
C. The Virtual Desktop Hardware Version is 9.
D. The Virtual Desktop Hardware Version is 10.
An administrator has a list of users who should not have access to Workspace Portal services. Some users need access to other services using their directory services account. Other users no longer need access to any services on the corporate network.
Which two steps should the administrator take to restrict access to Workspace Portal services? (Choose two.)
A. Disable or delete the account in Active Directory for those accounts that no longer need access to Workspace Portal.
B. Disable the Virtual Users feature in the Class of Service (CoS).
C. Create filters with the Workspace Portal connector that filter out existing users who no longer need access to Workspace Portal.
D. Disable or delete the account in Active Directory for those accounts that no longer need access to any corporate network services.
Refer to the Exhibit.
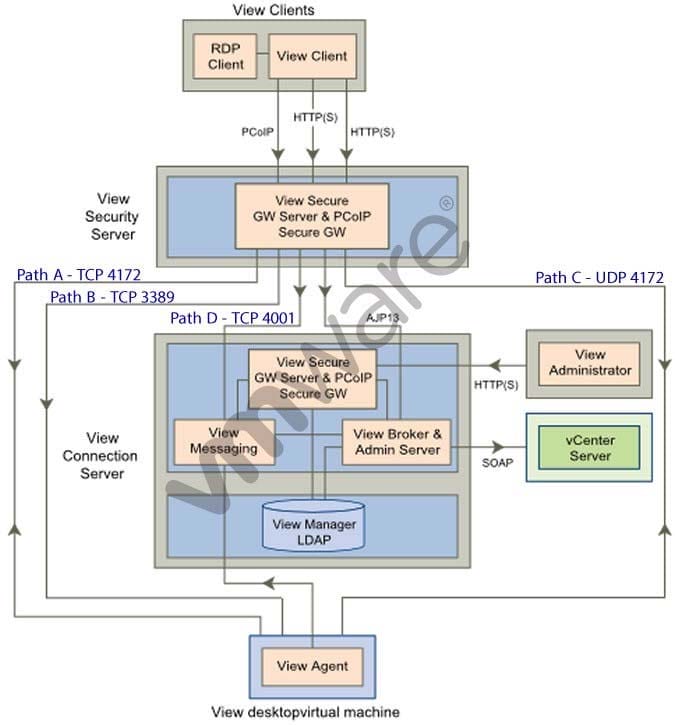
Based on the exhibit, which two paths are used for PCoIP traffic? (Choose two.)
A. Path A
B. Path B
C. Path C
D. Path D