250-440 Online Practice Questions and Answers
Refer to the traffic tree in the exhibit.
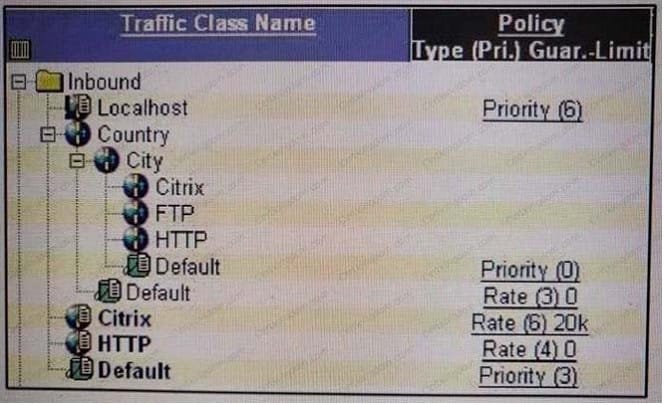
Which policy is applied to Inbound/Country/City/Citrix?
A. Priority 6
B. Priority 3
C. Rate(6) 20k
D. Rate(3) 0
What are the main two functional modules within the PacketShaper?
A. Shaping module and Monitoring module
B. Shaping module and Policy module
C. Compression module and Acceleration module
D. Monitoring module and Caching module
Which two (2) actions are most appropriate for controlling prohibited, unsanctioned traffic flows such as music downloads? (Select two)
A. Set a discard policy to block the traffic
B. Set a never-admit policy to redirect the traffic
C. Set a rate policy with 0 guaranteed, bur*table, at high priority
D. Set a rate policy with 0 guaranteed, burnable, at priority 6
E. Create a static partition for each branch
Refer to the exhibit.
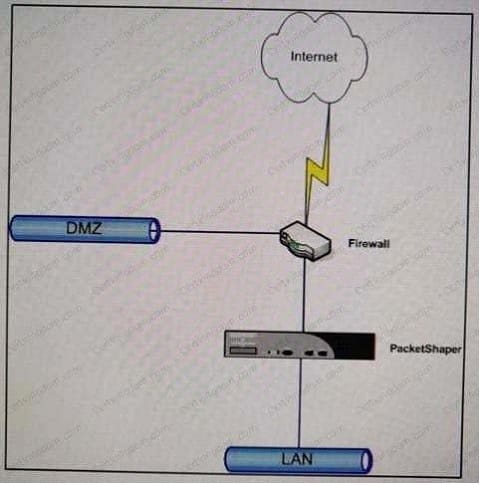
Which task must the administrator perform to make sure that traffic between (he IAN and DMZ is treated as pass-through PacketShaper installed as shown?
A. Create a class for LAN-to-DMZ traffic and apply a 100 MB partition to it. ..
B. Create a class for lANto-OMZ traffic and apply a 100-MB rate policy to it.
C. Create a class for lAN-tO-DMZ traffic and apply an ignore policy to it.
D. Configure the PacketShapet to automatically identify Inside and Outside hosts, therefor* no special configuration is required.
Which control limits the number of simultaneous TCP flows in a class?
A. class licenses
B. policy delay bound
C. system limits
D. policy flowlimit
Which scenario would the "burstable al priority" attribute be used in?
A. To enable a traffic class to access unused bandwidth at Priority 3 or above
B. When a limit is specified that is less than the policy's guaranteed rate
C. When a limit is specified that is greater than the policy's guaranteed rate
D. To enable a traffic class to access unused bandwidth at a specified priority level
A PacketSHaper is installed between the VPN Gateway and Internet i outer at the main site of a company's
network A server at the main site is hosting business critical applications. A local ionbased traffic tree has
been created which classifies traffic coming from three remote sites by subnet.
All traffic between the remote sites and the central sue is encrypted.
Which two (2) useful pieces of data can the PacketShaper provide in this scenario? (Select two)
A. Bandwidth utilization of each individual application
B. Bandwidth utilization of the total encrypted VPN traffic
C. lop talkers and Top Listeners at the remote site
D. Bandwidth utilization of each individual remote site
E. Subnets or host lists of location-based classes
Which statement accurately describes rate policies and priority policies?
A. Priority policies are most appropriate tor interactive traffic that is burstable
B. Rate polices apply only to non-IP traffic
C. Traffic classes without a specific policy assigned, are allocated no bandwidth
D. Traffic with rate policies are applied before the priority policy
What is the purpose of a "Traffic Class"?
A. It enforces the policy by normalizing all traffic
B. It applies source routing features for load balancing
C. It identities the traffic type, which allows a policy to be applied
D. It forwards traffic to the Measurement Engine
A network administrator is interested in protecting VoIP traffic on the network.
How can the administrator best accomplish this while maintaining visibility into overall VoIP bandwidth
utilization'
A. An administrator is unable to monitor and protect All VoIP traffic at once using a PacketShaper
B. Create a class based on the IP addresses of the IP phones so that all traffic between them can be measured and controlled
C. Use PacketShaper's Flow Detail Record (FDR) feature to have the PacketShaper export VoIP flow data to ReportCenter
D. Create a folder with a guaranteed minimum sue partition and move all of the VoIP related classes into the folder