250-428 Online Practice Questions and Answers
A financial company enforces a security policy that prevents banking system workstations from connecting to the Internet. Which Symantec Endpoint Protection technology is ineffective on this company's workstations?
A. Insight
B. Intrusion Prevention
C. Network Threat Protection
D. Browser Intrusion Prevention
Which option is a characteristic of a Symantec Endpoint Protection (SEP) domain?
A. Each domain has its own management server and database.
B. Every administrator from one domain can view data in other domains.
C. Data for each domain is stored in its own separate SEP database.
D. Domains share the same management server and database.
In the virus and Spyware Protection policy, an administrator sets the First action to Clean risk and sets If first action fails to Delete risk. Which two factors should the administrator consider? (Select two.)
A. The deleted file may still be in the Recycle Bin.
B. IT Analytics may keep a copy of the file for investigation.
C. False positives may delete legitimate files.
D. Insight may back up the file before sending it to Symantec.
E. A copy of the threat may still be in the quarantine.
Which task should an administrator perform to troubleshoot operation of the Symantec Endpoint Protection embedded database?
A. verify that dbsrv11.exe is listening on port 2638
B. check whether the MSSQLSERVER service is running
C. verify the sqlserver.exe service is running on port 1433
D. check the database transaction logs in X:\Program Files\Microsoft SQL server
An administrator uses the search criteria displayed in the image below. Which results ore returned from the query?
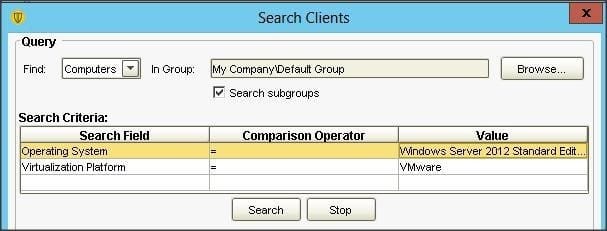
A. Only VMware Servers in the Default Group
B. All Windows 2012 Servers in the Default Group
C. Only Windows 2012 Servers that are Virtualized in the Default Group
D. All Windows 2012 Servers and all Virtualized Servers in the Default Group
Which two criteria should an administrator use when defining Location Awareness for the Symantec Endpoint Protection (SEP) client? (Select two.)
A. NIC description
B. SEP domain
C. geographic location
D. WINS server
E. Network Speed
What type of client remediation can an administrator perform in the SEPM with events in the Attack logs?
A. Free additional disk space by removing files from Quarantine
B. Review the operation status of client computers and enable protection technologies
C. Create a Firewall rule in the Firewall policy
D. Run Power Eraser remotely to resolve issues with heavily infected computers
An organization has a small group of servers with large drive volumes.
What setting in the Virus and Spyware Protection policy can the organization utilize when scheduling scans on these servers?
A. Use resumable scans
B. Use Shared Insight Cache
C. Adjust Auto Protect Settings
D. Randomize scheduled scans
An organization has a group of 500 SEP for Windows Clients running 12.1 RU5. The organization wants to migrate the clients to 14 RU1, but must minimize WAN bandwidth usage. What installation method should the organization use?
A. Push Deployment Wizard
B. Clients Install Package hosted on a local HTTP Server
C. Client Deployment Wizard
D. Auto Upgrade
Solusell recently deployed SEP 14 in their environment and created the following groups for their computers: Desktops Laptops Servers
What type of group structure does Solusell use?
A. Role
B. Combination
C. Folder
D. Geography