210-255 Online Practice Questions and Answers
Which feature is used to find possible vulnerable services running on a server?
A. CPU utilization
B. security policy
C. temporary internet files
D. listening ports
Which of the following are examples of some of the responsibilities of a corporate CSIRT and the policies it helps create? (Select all that apply.)
A. Scanning vendor customer networks
B. Incident classification and handling
C. Information classification and protection
D. Information dissemination
E. Record retentions and destruction
Refer to the following packet capture. Which of the following statements is true about this packet capture?
00:00:04.549138 IP omar.cisco.com.34548 > 93.184.216.34.telnet: Flags [S], seq 3152949738, win 29200,
options [mss 1460,sackOK,TS val 1193148797 ecr 0,nop,wscale 7], length 0 00:00:05.547084 IP omar.cisco.com.34548 > 93.184.216.34.telnet: Flags [S], seq 3152949738, win 29200,
options [mss 1460,sackOK,TS val 1193149047 ecr 0,nop,wscale 7], length 0 00:00:07.551078 IP omar.cisco.com.34548 > 93.184.216.34.telnet: Flags [S], seq 3152949738, win 29200,
options [mss 1460,sackOK,TS val 1193149548 ecr 0,nop,wscale 7], length 0 00:00:11.559081 IP omar.cisco.com.34548 > 93.184.216.34.telnet: Flags [S], seq 3152949738, win 29200,
options [mss 1460,sackOK,TS val 1193150550 ecr 0,nop,wscale 7], length 0
A. The host with the IP address 93.184.216.34 is the source.
B. The host omar.cisco.com is the destination.
C. This is a Telnet transaction that is timing out and the server is not responding.
D. The server omar.cisco.com is responding to 93.184.216.34 with four data packets.
Choose the option that best describes NIST data integrity
A. use only sha-1
B. use only md5
C. you must hash data and backup and compare hashes
D. no need to hash data and backup and compare hashes
Which two potions about deterministic and probabilistic analysis are true? (Choose two.)
A. probabilistic analysis uses data known beforehand and deterministic analysis is based off assumptions.
B. Deterministic analysis uses data known beforehand and probabilistic analysis based off of assumptions.
C. Deterministic analysis is based off of assumptions
D. Probabilistic analysis result in a result that is definitive.
E. probabilistic analysis results in a result that is not definitive.
According to NIST 86, which action describes the volatile data collection?
A. Collect data before rebooting
B. Collect data while rebooting
C. Collect data after rebooting
D. Collect data that contains malware
What define the roadmap for implementing the incident response plan?
A. Incident response plan
B. Incident response policy
C. Incident response procedures
Which event artifact can be used to identify HTTP GET requests for a specific file?
A. HTTP status code
B. TCP ACK
C. destination IP
D. URI
Which machine risk to be infected or something like that?
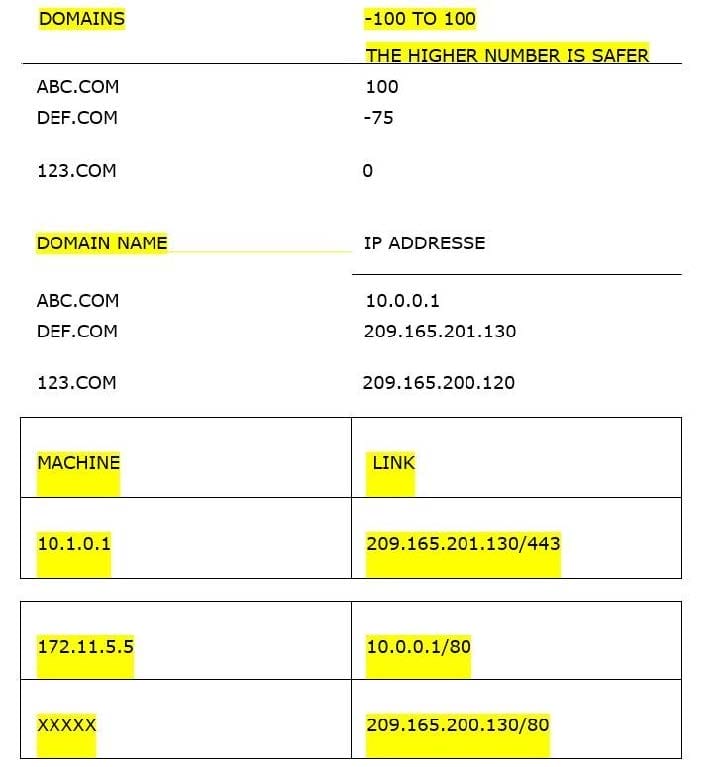
A. 10.1.0.1
B. 172.11.5.5
C. Other option
Which description of probabilistic analysis is true?
A. probable proof of a user's identity
B. lack of proof of a user's identity
C. definitive proof of a user's identity
D. false proof of a user's identity