200-201 Online Practice Questions and Answers
A security analyst notices a sudden surge of incoming traffic and detects unknown packets from unknown senders After further investigation, the analyst learns that customers claim that they cannot access company servers According to NIST SP800-61, in which phase of the incident response process is the analyst?
A. post-incident activity
B. detection and analysis
C. preparation
D. containment, eradication, and recovery
An engineer needs to fetch logs from a proxy server and generate actual events according to the data received. Which technology should the engineer use to accomplish this task?
A. Firepower
B. Email Security Appliance
C. Web Security Appliance
D. Stealthwatch
What is the difference between inline traffic interrogation (TAPS) and traffic mirroring (SPAN)?
A. TAPS interrogation is more complex because traffic mirroring applies additional tags to data and SPAN does not alter integrity and provides full duplex network.
B. SPAN results in more efficient traffic analysis, and TAPS is considerably slower due to latency caused by mirroring.
C. TAPS replicates the traffic to preserve integrity, and SPAN modifies packets before sending them to other analysis tools
D. SPAN ports filter out physical layer errors, making some types of analyses more difficult, and TAPS receives all packets, including physical errors.
Which of these describes SOC metrics in relation to security incidents?
A. time it takes to detect the incident
B. time it takes to assess the risks of the incident
C. probability of outage caused by the incident
D. probability of compromise and impact caused by the incident
Which type of evidence supports a theory or an assumption that results from initial evidence?
A. probabilistic
B. indirect
C. best
D. corroborative
An engineer must investigate suspicious connections. Data has been gathered using a tcpdump command on a Linux device and saved as sandboxmalware2022-12-22.pcaps file. The engineer is trying to open the tcpdump in the Wireshark tool. What is the expected result?
A. The file is opened.
B. The tool does not support Linux.
C. The file does not support the
Refer to the exhibit. Which type of evidence is this file?

A. direct evidence
B. corroborating evidence
C. best evidence
D. circumstantial evidence
What are the three critical security principles or goals of the CIA triad?
A. Protect the confidentiality of data, and ensure that protected data is unaltered at all stages and available for permitted requesters.
B. Validate the copyright of the data, and ensure that individual data owners are protected with a defense-in-depth approach.
C. Ensure that the connections are safe and the data delivery is improved continuously with appropriate monitoring and cross-checks.
D. Implement data tags to identify critical assets and data for preserving the secretness, and develop policies and procedures for accessing data.
A CMS plugin creates two files that are accessible from the Internet: myplugin.html and exploitable.php. A newly discovered exploit takes advantage of an injection vulnerability in exploitable.php. To exploit the vulnerability, an HTTP POST must be sent with specific variables to exploitable.php. A security engineer notices traffic to the webserver that consists of only HTTP GET requests to myplugin.html. Which category does this activity fall under?
A. exploitation
B. reconnaissance
C. installation
D. weaponization
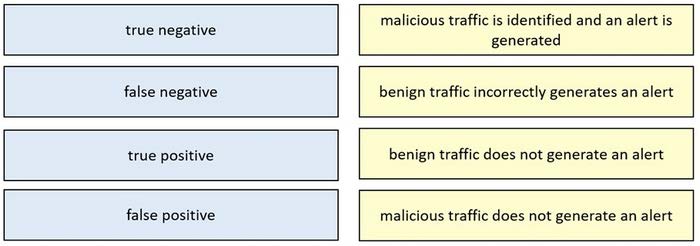
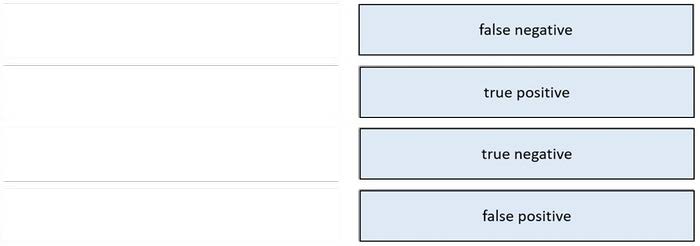
DRAG DROP
Drag and drop the event term from the left onto the description on the right.
Select and Place: