1Z0-888 Online Practice Questions and Answers
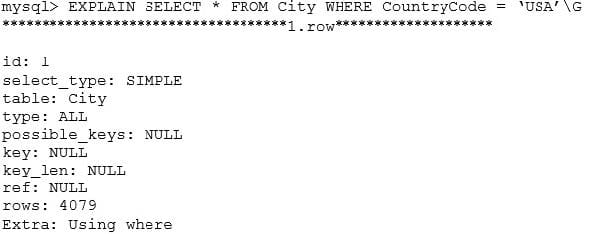
What does the possible_keys column in this output denote?
A. if it is possible for you to include any indexes in your query
B. whether there are any indexes on the tables that you are querying
C. if there are any indexes that may be used to solve this query
D. whether you are using any indexes in your query
MySQL is installed on a Linux server and has this configuration:
[mysqld]
user=mysql
datadir=/data/mysql/
As the ‘root’ user, you change the datadir location by executing:
shell> cp –R /var/lib/mysql /data/mysql/
shell> chown –R mysql /data/mysql
What is the purpose of changing ownership of datadir to the ‘mysql’ user?
A. MySQL needs to be run as the root user, but files cannot be owned by it.
B. The mysqld process requires all permissions within datadir to be the same.
C. MySQL cannot be run as the root user.
D. MySQL requires correct file ownership while remaining secure.
You created a backup of the world database with this command: shell> mysqldump --opt world > dump.sql
Which two will import the data from dump.sql? (Choose two.)
A. shell> mysqladmin recover test dump.sql
B. shell> mysql test < dump.sql
C. shell> mysqlimport test dump.sql
D. mysql> USE test; mysql> LOAD DATA INFILE `dump.sql';
E. mysql>USE test; mysql>SOURCE dump.sql;
An administrator installs MySQL to run under a mysql OS account. The administrator decides to disable logins to the mysql account by using /nologin or /bin/false as the user's shell setting.
Which statement is true?
A. The mysql user needs a login and its home directory must be the base directory of the installation.
B. The OS needs to allow logging in as mysql so that administrative tasks can be performed.
C. This prevents mysqld from starting when standard startup scripts are used.
D. This prevents creation of a command shell with the mysql account, while allowing mysqld to run.
In which order does MySQL process an incoming INSERT statement?
A. It checks whether the user is authorized to perform the query, writes to the binary log, and then optimizes it.
B. It checks whether the user is authorized to perform the query, optimizes it, and then writes to the binary log.
C. It writes the query to the binary log, optimizes it, and then checks whether the user is authorized to perform the query.
D. It optimizes the query, checks whether the user is authorized to perform it, and then writes to the binary log.
You are asked to examine user accounts and find:
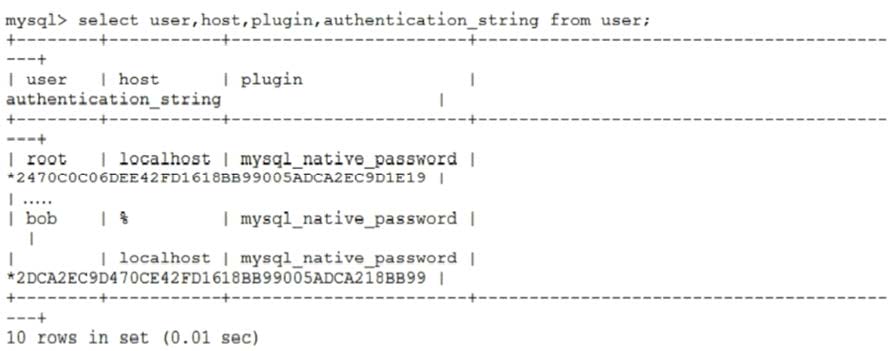
Which two statements will best secure this environment? (Choose two.)
A. DROP USER `'@'localhost';
B. ALTER USER `'@'localhost' PASSWORD = `secret_password';
C. ALTER USER bob@'%' IDENTIFIED BY `secret_password';
D. ALTER USER `root'@'localhost' ACCOUNT LOCK;
E. ALTER USER bob PASSWORD = `secret_password';
F. REVOKE ALL PRIVILEGES FROM `'@'localhost';
The InnoDB tablespace is corrupted and you start the server with option --innodb_force_recover=4. Which backup method would you use to reload the corrupted InnoDB tables?
A. a binary backup that uses transportable tablespaces and allows you to reload a corrupted table
B. A text backup. A binary backup will still contain the corrupted segments.
C. A text backup. InnoDB does not allow you to make binary backups while the server is running.
D. a binary backup taken with MySQL Enterprise Backup that can back up even corrupted tables
Given these table definitions and the explain plan: Which ALTER TABLE statement will improve the performance of the query?
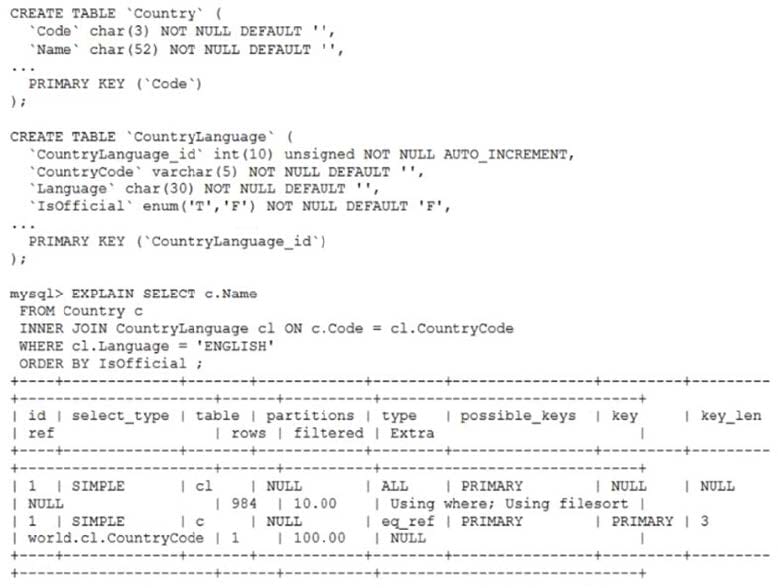
A. ALTER TABLE `CountryLanguage` ADD INDEX `idx_Lang` (`Language`);
B. ALTER TABLE `Country` ADD INDEX `idx_Code` (`Code`);
C. ALTER TABLE `CountryLanguage` ADD INDEX `idx_OffLang` (`IsOfficial`, `Language`);
D. ALTER TABLE `Country` ADD INDEX `idx_NameCont` (`Name`, `CountryCode`);
You have a MySQL instance running in a single cpu (1vCPU) VM in a shared infrastructure environment.
Your users are complaining that MySQL is sporadically slow and you have a suspicion that the VM infrastructure host is at fault due to resource contention.
You review the output of your scripts that monitor the database VM operating system during an extended period of slowdown.
What are the two most common indicators of the VM infrastructure host being at fault due to resource contention? (Choose two.)
A. 10% CPU
B. 90% RAM
C. 9.1 five minute load average, 10% iowait
D. 100% CPU use, 50% RAM
E. 100% iowait
F. 100% SWAP, 100% RAM
You have issued this statement:
GRANT PROXY ON 'a' FOR 'b';
When user account 'b' issues a query, the query returns an access denied error.
What could have caused that error?
A. When connecting, user account 'b' is not entering the correct password for user account 'a'.
B. You have not set the proxy_user variable in the configuration file.
C. User account 'b' has not been granted permission to access the data being queried.
D. User account 'a' has not been granted permission to access the data being queried.