1Z0-574 Online Practice Questions and Answers
The three common goals of Information security are known as the CIA triad. CIA stands for:
A. Confidentiality, Integrity and Auditing
B. Confidentiality, Integrity and Availability
C. Confidentiality, Integrity and Access Control
D. Confidentiality, Integrity and Authentication
E. Confidentiality,Integrity and Authorization
Identify the true statements in the following list.
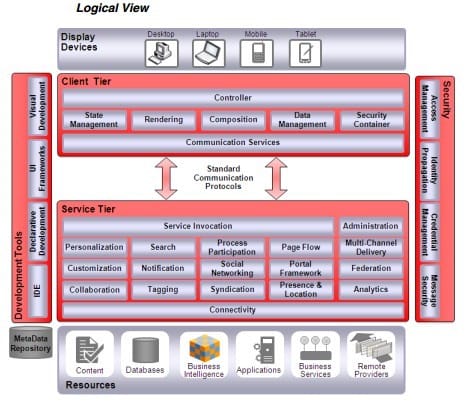
A. The core components of the ORA UI Logical view are grouped into the client tier and the server tier.
B. The components of the ORA UI Logical view are model, view, and controller.
C. The core components of the ORA UI Logical view are grouped into thedisplaytier and theresourcestier.
D. In addition to the core components, the Logical view also includes security, communication protocols, and development tools.
Oracle Web Services Manager uses an agent-based approach to providing Web Services security. Where are these agents deployed?
A. In any IPv4 of Later network firewall
B. In the Oracle WebLogic Server Web Service request Interceptors
C. In the Oracle Service Bus proxy pipeline
D. In the Oracle Access Manager web gate
E. In the Oracle WebLogic Server access gate
Which three primary components form IT Strategies from Oracle (ITSO)?
A. Enterprise Technology Strategies
B. Maximum Availability Architecture
C. Enterprise Solution Designs
D. Oracle Reference Architecture
E. Oracle Enterprise Architecture Framework
F. Oracle Unified Method
Which of the following are true statements about the benefits of standardizing on a common security framework?
A. Security requirements no longer need to be specified for eachindividual application; the framework will automatically determine what security needs to be applied.
B. A common set of security services and information can be used across the organization, promoting Infrastructure reuseand minimizing inconsistencies.
C. Secure application integrationis made easier via standardization on a preferred subset of technologies and options.
D. Administration and auditing are improved due to rationalization and standardization of identities, attributes, roles, policies, and so on.
E. Interoperability amid federation are easier to achieve via the adoption of common security and technology standards.
Audit logging is a form of what type of access control mechanism?
A. detective control
B. preventive control
C. deterrent control
D. corrective control
E. compensating control
F. recovery control
Which statement best describes the use of point-to-point integrations within a Service-Oriented Integration (SOI) architecture?
A. point-to-point integrations using web services are an Integral part of SOI and should be used extensively.
B. Only web service-based point-to-point integrations are allowed (but discouraged).
C. Point-to-point integrations should be avoided but are allowed as exceptions when requirements can be met only by point-to-point integration.
D. Point-to-point integrations are brittle and expensive to maintain and therefore should never be used.
Which of the following does Policy Management Compliance refer to?
A. a desired behavior, andis associated with one or more Infrastructure components
B. the demonstration and enforcement of regulatory standards,industry standards, internal best practices
C. a set of processes through which management identifies, analyzes and, where necessary, responds appropriately to risks
D. a management approach to direct and control the entire organization by using a combination of management information and hierarchical management control structures
Which of the following are primary parts of a SOA Service as defined by the Oracle Reference Architecture?
A. Service Contract
B. Usage Agreement
C. Service Infrastructure
D. Service Implementation
E. Service Interface
F. Web Services Description Language (WSDL)
Which statement best describes how Service-Oriented Integration (SOI) differs from traditional Enterprise Application Integration (EAI)?
A. SOI is Just like EAI except that a service bus is used Instead of a hub or message bus.
B. SOI is different than hub-based EAI, but is the some as EAI using a message bus.
C. SOI uses a point to-point integration approach based on the Web Services Industry standards.
D. SOI uses SOA Services that are separate and distinct from the applications being integrated
E. EAI integrates applications whereas SOA integrates SOA Services.