1Z0-1104-22 Online Practice Questions and Answers
which two responsibilities will be oracle when you move your it infrastructure to oracle cloud infrastructure?
A. Strong IAM Framework
B. PROVIDING STRONG SECURITY LIST
C. Strong Isolation
D. MAINTAINING CUSTOMER DATA
E. ACCOUNT ACCESS MANAGEMENT
What does the following identity policy do?
Allow group my-group to use fn-invocation in compartment ABC where target.function.id = `
A. Enables users in a group to create, update, and delete ALL applications and functions in a compartment
B. Enables users to invoke all the functions in a specific application
C. Enables users to invoke just one specific function
D. Enables users to invoke all the functions in a compartment except for one specific function
Select the component that encompasses the overall configuration of your WAF service on OCI.
A. Protection rules
B. Bot Management
C. Web Application Firewall policy
D. Origin
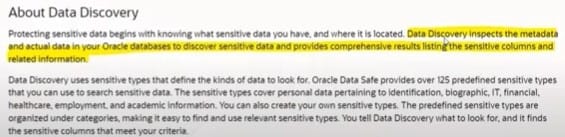
As a Security Admin you want to inspect the metadata and actual data in your Oracle databases to discover sensitive data and provide comprehensive results listing the sensitive columns and related information. Which Data Safe feature will help you to achieve the above requirement ?
A. Data Masking
B. Data Discovery
C. Security Assessment
D. User Assessment
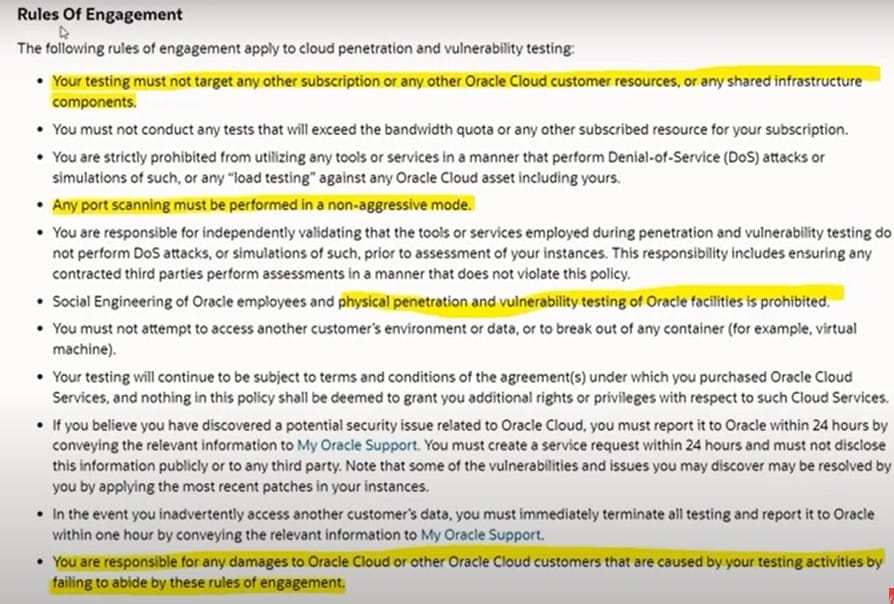
With regard to vulnerability and cloud penetration testing, which rules of engagement apply? Select TWO correct answers.
A. Any port scanning must be performed in an aggressive mode
B. Physical penetration and vulnerability testing of Oraclefacilities is prohibited
C. Testing should target any other subscription or any other Oracle Cloud customer resources
D. You are responsible for any damages to Oracle Cloud customers that are caused by your testing activities
Which VCNconfiguration is CORRECT with regard to VCN peering within a same region ?
A. 12.0.0.0/16 and 194.168.0.0/16
B. 12.0.0.0/16 and 12.0.0.0/16
C. 194.168.0.0/24 and 194.168.0.0/24
D. 194.168.0.0/24 and 194.168.0.0/16
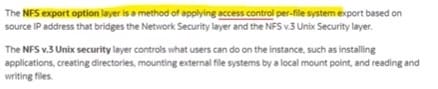
A company has OCI tenancy which has mount target associated with two File Systems, CG_1 and CG_2. These FileSystems are accessed by IP-based clients AB_1 and AB_2 respectively. As a security administrator, how can you provide access to both clients such that CGI has Read only access on AB1 and CG_2 has Read/Write access on AB_2?
A. NFS Export Option
B. Access Control Lists
C. NFS v3 Unix Security
D. Vault
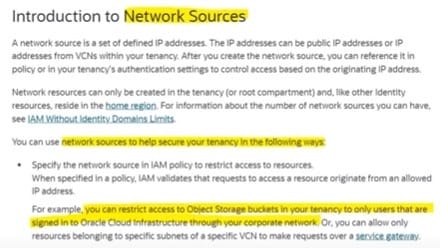
As a security administrator, you found out that there are users outside your co network who are accessing OCI Object Storage Bucket. How can you prevent these users from accessing OCI resources in corporate network?
A. Create an 1AM policy and create WAF rules
B. Create an 1AM policy and add a network source
C. Make OCI resources private instead of public
D. Create PAR to restrict access the access
Which of these protects customer data at rest and in transit in a way that allows customers to meet their security and compliance requirements forcryptographic algorithms and key management?
A. Security controls
B. Customer isolation
C. Data encryption
D. Identity Federation
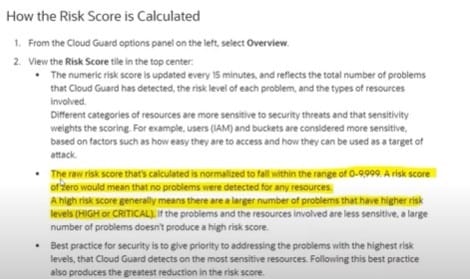
Cloud Guard detected a risk score of zeroin the dashboard, what does this mean ?
A. Risk score doesn't say anything. These are just numbers
B. LOW or MINOR issues
C. Larger number of problems that have high risk levels ( HIGH or CRITICAL )
D. No problem detected for any resource