1Z0-1085-20 Online Practice Questions and Answers
Which three methods can you use to create or modify Oracle Cloud Infrastructure (OCI) resources?
A. REST APIs
B. OCI desktop client
C. Secure Shell (SSH)
D. OCI Console
E. Command-line Interface
F. Remote Desktop Protocol (RDP)
G. Serial console connection
Which OCI service is the most cost-effective?
A. File Storage
B. Object Storage (standard)
C. Block Volume
D. Archive Storage
You want to migrate mission-critical Oracle E- Business Suite application to Oracle Cloud Infrastructure
(OCI) with full control and access to the underlying infrastructure.
Which option meets this requirement?
A. Replace E-Business Suite with an Oracle SaaS application
B. OCI Exadata DB Systems and OCI compute instances
C. OCI Exadata DB Systems and Oracle Functions
D. Oracle Exadata Cloud at customer, Storage Gateway and API Gateway
You are required to host several files in a location that can be publicly accessible from anywhere in the world. Which Oracle Cloud Infrastructure (OCI) service should you use?
A. OCI Object Storage
B. Oracle Functions
C. OCI Block Volume
D. OCI File Storage
E. OCI Storage Gateway
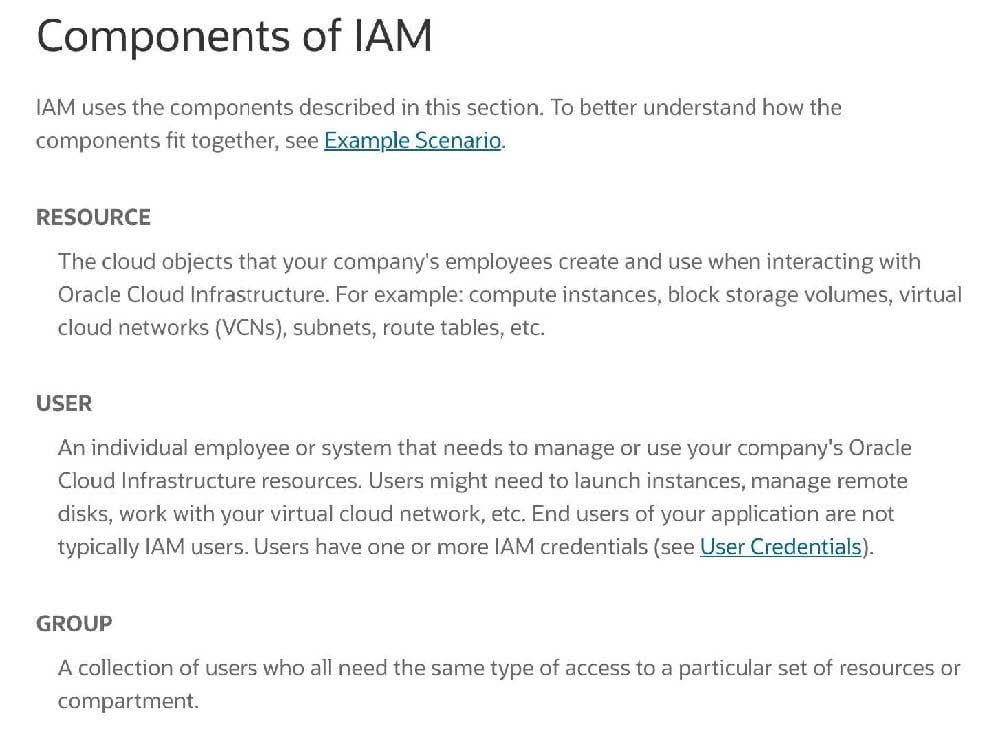
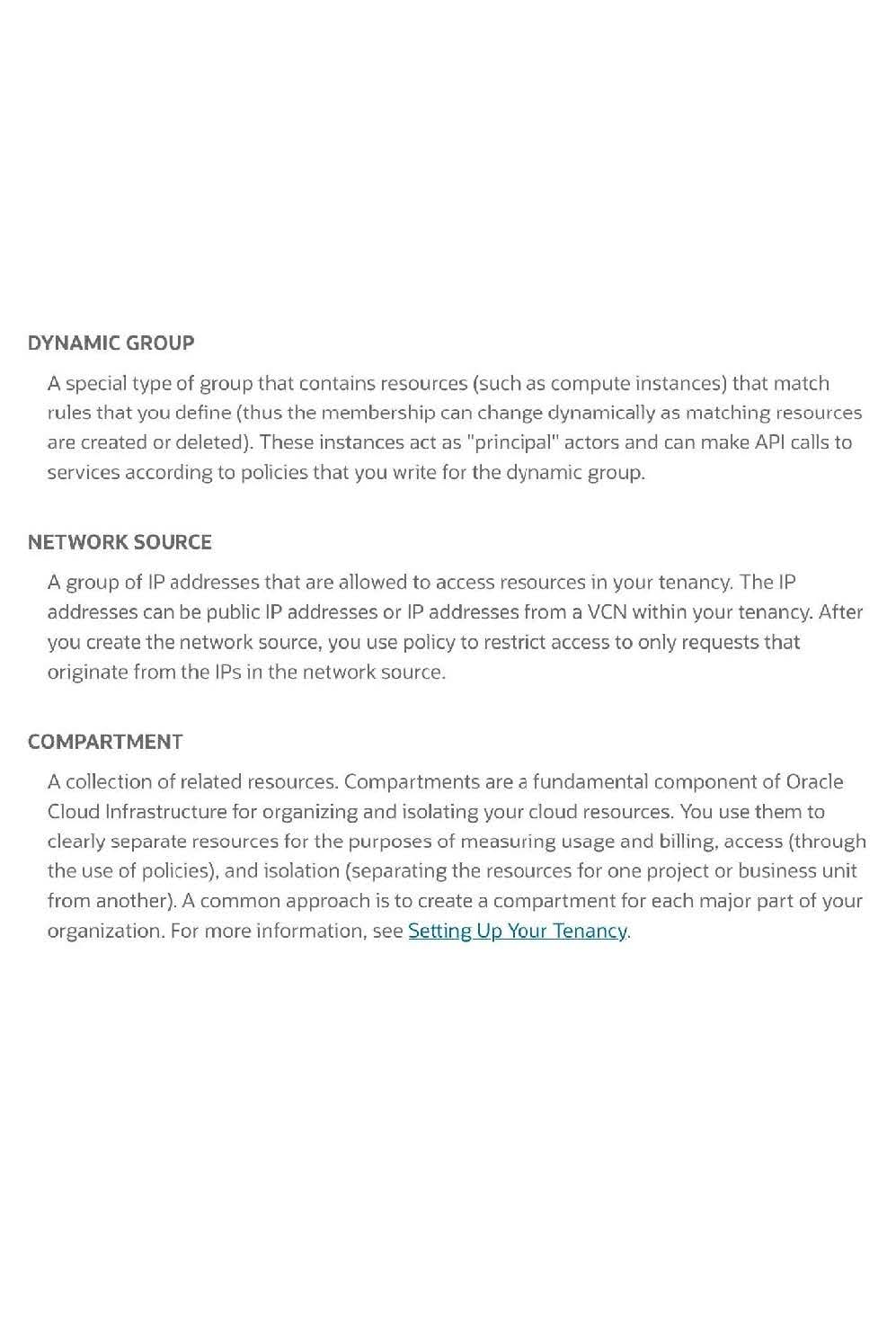
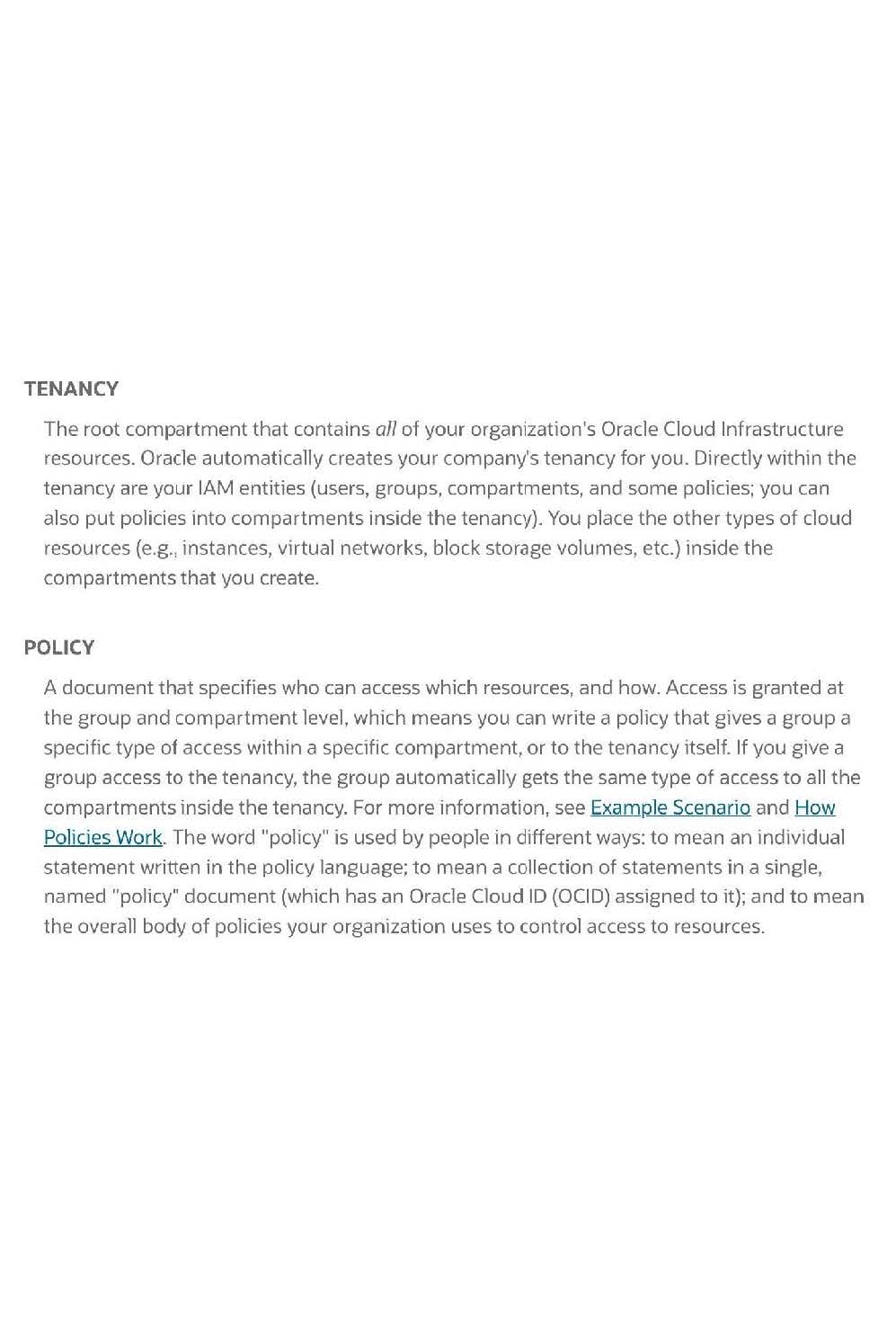
Which feature is not component of Oracle cloud Infrastructure identity and Access management service?
A. federation
B. User Credential
C. Network Security Group
D. Policies
Which statement is true for an oracle cloud Infrastructure (OCI) compute instance?
A. Compute instance always get a public IP address
B. Compute instance does not use a boot volume
C. Compute instance cannot leverage auto scaling feature
D. Compute instance always get a private IP address
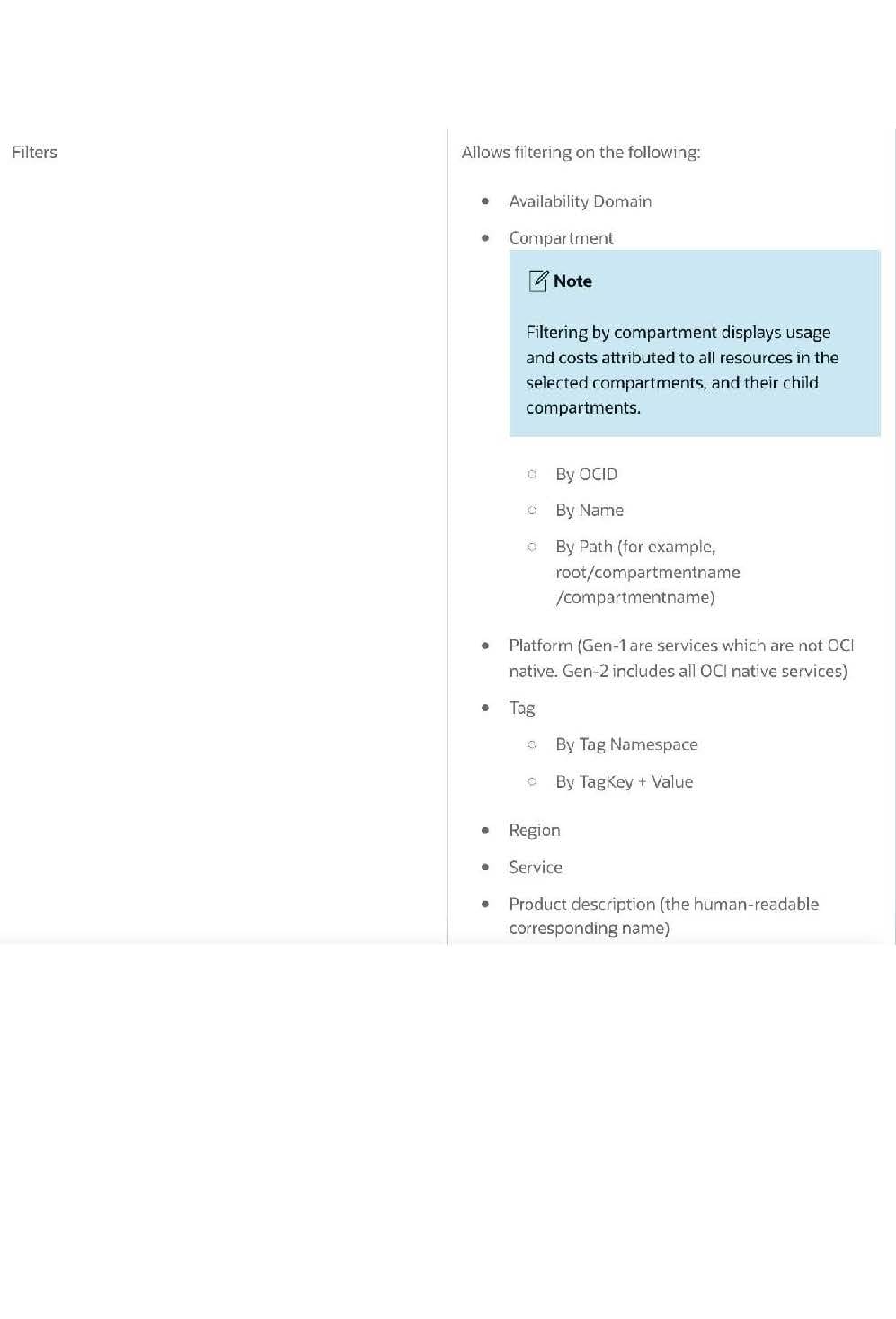
You are analyzing your Oracle Cloud Infrastructure (OCI) usage with Cost Analysis tool in the OCI console. Which of the following is NOT a default feature of the tool?
A. Filter costs by applications
B. Filter costs by tags
C. Filter costs by compartments
D. Filter costs by date
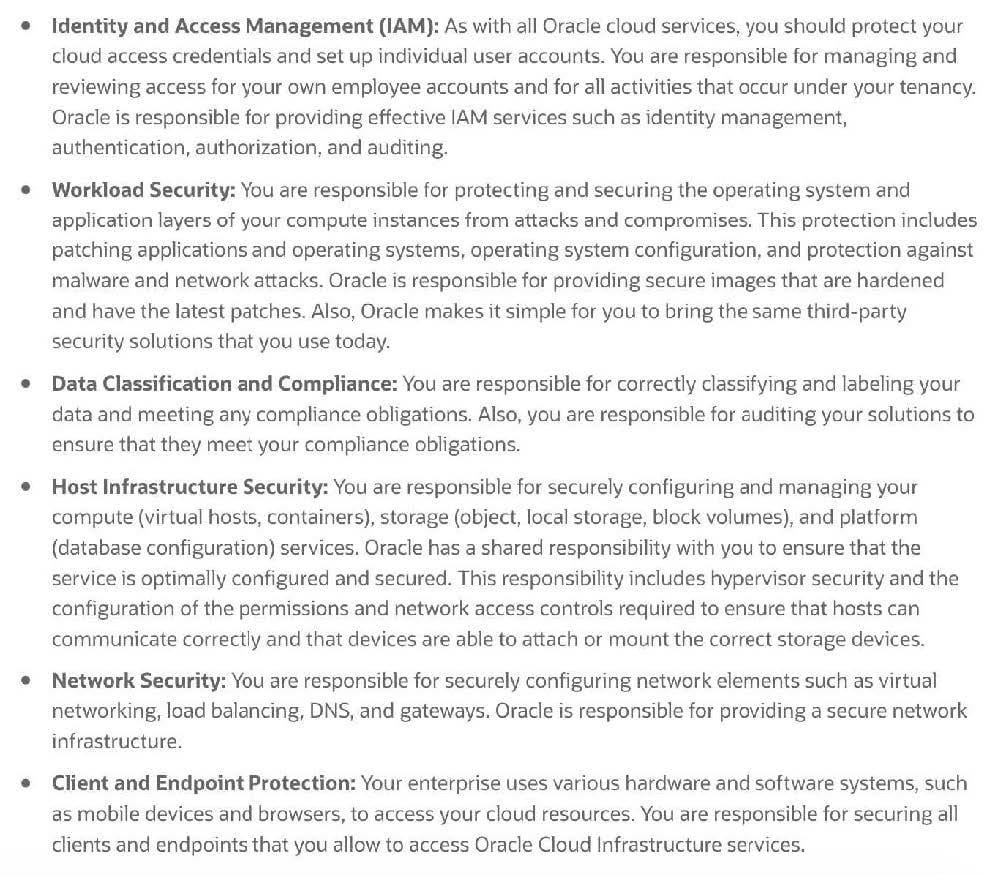
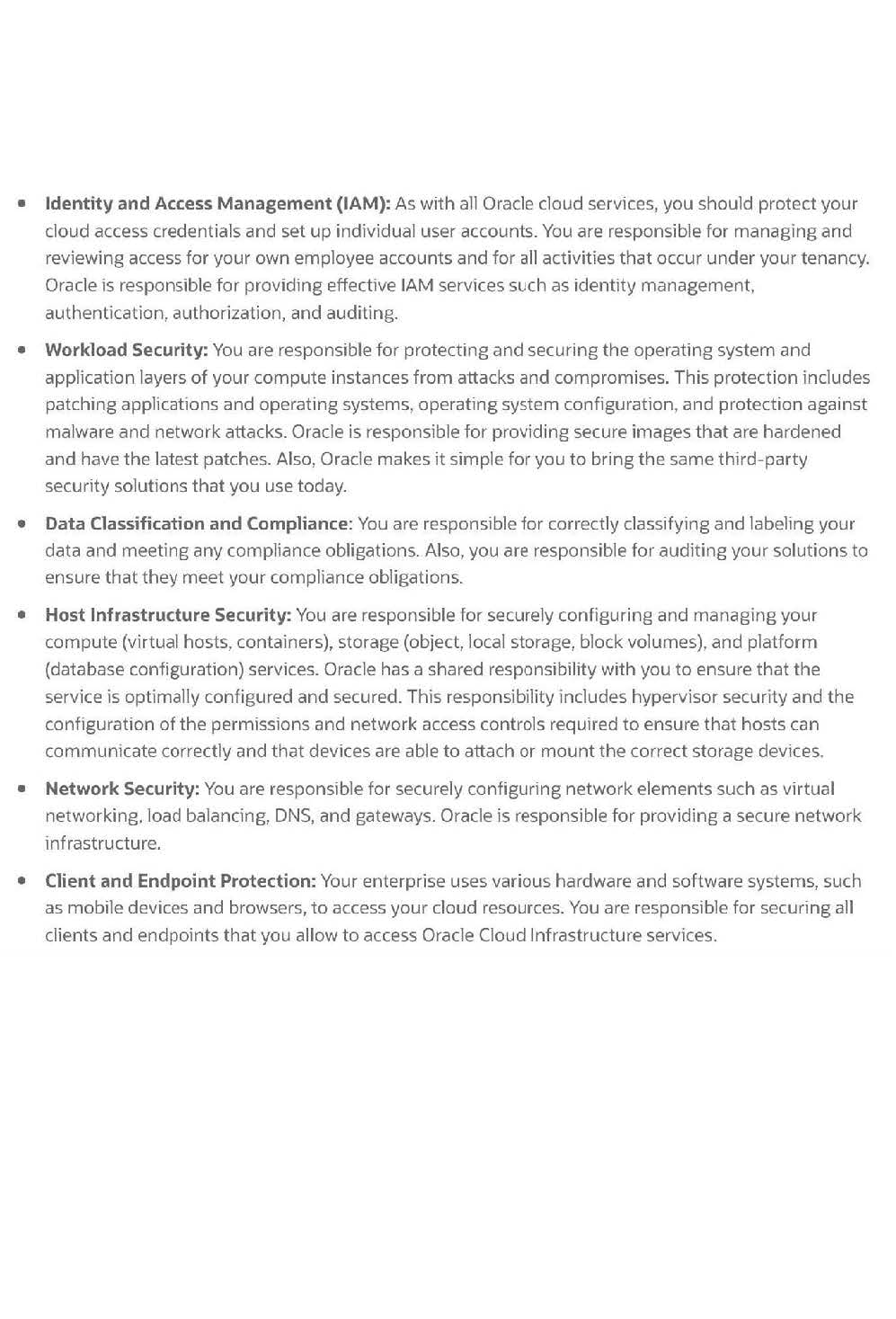
Which statement about the Oracle Cloud Infrastructure (OCI) shared-security model is true?
A. You are responsible for securing all data that you place in OCI
B. You are not responsible for any aspect of security in OCI
C. You are responsible for securing the hypervisor within OCI compute service
D. You are responsible for managing security controls within the physical OCI network
Which of the following services can you control access to via IAM?
A. Networking components
B. Compute Instances
C. All services including IAM
D. DB systems
What is Oracle's responsibility according to the Oracle Cloud Infrastructure (OCI) shared-security model?
A. Configuring OCI services securely
B. Data classification and compliance
C. Securing application workloads
D. Security of data center facilities