1Z0-1070-20 Online Practice Questions and Answers
What does Oracle CASB Cloud Service Access Map within Dashboard Summary show?
A. suspicious activity and threats that have transpired within Oracle CASB and across different geographical regions or the world
B. up to five Application Instances, including API calls showing the geographical regions where the instance was first implemented
C. mobile devices users who are actively using Oracle Identity Cloud Services in a manner that is against Oracle Corporate Usage Policy
D. a geography of login attempts within Oracle Identity Cloud Service and Oracle Enterprise Resource Planning Cloud, specifically the successful logins
Which two services in Oracle Identity SOC solution have machine learning built into it? (Choose two.)
A. Oracle Integration Cloud Service
B. Oracle CASB Cloud Service
C. Oracle Security Monitoring and Analytics Cloud Service
D. Oracle Application Performance Monitoring Cloud Service
Which three represent the different types of Identity SOC architectural models? (Choose three.)
A. Dedicated SOC
B. Privileged SOC
C. Fusion SOC
D. Shared SOC
E. Virtual SOC
In your organization, security operations complains about the shortage of resources to handle the number of alerts generated from the security products deployed. You want to automate the process of handling and remediating the alerts and also want to add contextual awareness to adapt to the threats in real time.
Which would provide the required solution?
A. Oracle Integration Cloud Service
B. Oracle Identity Security Operations Center (SOC)
C. Oracle Configuration and Compliance Cloud Service
D. Oracle Log Analytics Cloud Service
Click to the exhibit.
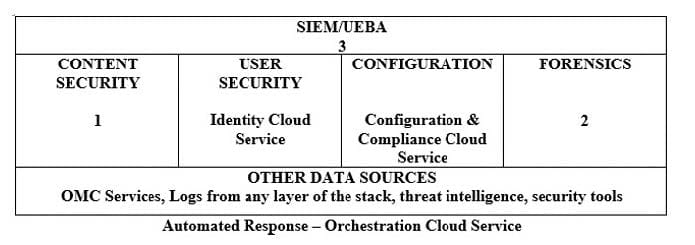
Which three items fit on the high-level architecture diagram?
A. 1 (Log Analytics Cloud Service), 2 (Database Security Vault), 3 (CASB Cloud Service)
B. 1 (CASB Cloud Service), 2 (Security Monitoring and Analytics Cloud Service), 3 (Log Analytics Cloud Service)
C. 1 (CASB Cloud Service), 2 (Log Analytics Cloud Service), 3 (Security Monitoring and Analytics Cloud Service)
D. 1 (Security Monitoring and Analytics Cloud Service), 2 (CASB Cloud Service), 3 (Log Analytics Cloud Service)
From the Oracle Management Cloud dashboard, you noticed a threat or suspicious browsing activity by a user to execute a brute force attack against an application.
Which two remedial actions will happen implicitly to mitigate some risk? (Choose two.)
A. Multi-factor Authentication (MFA) is imposed
B. User added to suspicious data access watchlist
C. Application policy gets created
D. Host AV update enforced
Which two issues can be resolved by using Oracle Configuration and Compliance Cloud Service? (Choose two.)
A. A single timely compliance posture across the enterprise
B. Manual compliance attestation to check rules and benchmarks
C. Assessments across multiple data centers for a timely global compliance posture
D. Extend pre-built benchmarks with custom rules to meet requirements
Which top-level menu option would you go to in order to add an Oracle CASB Cloud Service user?
A. Jobs
B. Configuration, User Exclusion List
C. Users
D. Configuration, Admin Management
Which four are the main pillars of the Oracle Identity Security Operations Center (SOC) solution? (Choose four.)
A. Threat Intelligence
B. Cloud Access Security Broker (CASB)
C. Security information and event management (SIEM)
D. IT Orchestration
E. Application Performance
F. User Entity Behavior and Analytics (UEBA)
Which is a major concern with regards to Line of Business (LOB) buyers when acquiring cloud services?
A. Line of Business (LOB) buyers were buying IT services without notifying their security team.
B. Customers are acquiring services that may not be in compliance with external regulations.
C. Line of Business (LOB) buyers do not have executive approval to acquire such services.
D. End users have no visibility over an organization's cloud strategy.