1Z0-1058-23 Online Practice Questions and Answers
How do you populate the Control Method field with a new custom value, such as a third-party application'?
A. Enter the new value directly in the Control method field.
B. Use Lookup Meaning of the new lookup value.
C. Use Lookup Code of the new lookup value.
D. Use Lookup Type of the new lookup value.
Which filter can be used to identify expense reports that contain suspicious expense type combinations, such as, a report for a single trip that contains taxi, car rental, and mileage expenses?
A. Inclusive function filter grouped by the "Expense Report Information" object's "Report Number" where the "Expense Type" has an "Equals" condition for values that include taxi, car, mileage.
B. Inclusive function filter grouped by the "Expense Report Information" object's "Report Number" where the "Expense Type" has an "In" condition for values that include taxi, car, mileage.
C. Inclusive function filter grouped by the "Expense Report Information" object's "Person" where the "Expense Type" has an "In" condition for values that include taxi, car, mileage.
D. Inclusive function filter grouped by the "Expense Report Information" object's "Report Number" where the "Expense Amount" has a condition to identify high value anomalies.
You are implementing Advanced Financial Controls and you want to identify suspect transactions where the payment amount is less than $20 USD. However, you only want the results returned to be temporary. What will you build in order to accomplish your objective?
A. Template
B. Control
C. Model
D. Filter
E. Business object
You are configuring security and you do not want the risks to go through the review and approve process each time they are updated. How will you meet this requirement?
A. Add the Risk Reviewer Composite duty role to the person who creates the risks so he or she would be able to review them before saving the record.
B. Use only the Risk Approver Composite duty role in the configurations so the risks will not go through the review process.
C. Ensure that only the upper management is given the Risk Reviewer Composite duty role so they could review the risks that they want to review.
D. Ensure that no user has been assigned a job role that includes the Risk Reviewer Composite or Risk Approver Composite Duty Role.
During implementation, you created a risk object and successfully mapped it to a control object. The client's Risk Owner is able to access the risk but not the control. Why did this happen?
A. The Risk Administrator needs to run the synchronize jobs to populate the mapping.
B. The Risk Owner account is inactive.
C. The Risk Owner role does not have the right privileges.
D. The risk and control objects are inactive and need to be made active.
How do you identify Financial Reporting Compliance Cloud's key stakeholders?
A. Identify users who need to create and submit expense reports easily.
B. Identify users who will create customer invoices, and receive and apply customer payments.
C. Identify executives who need to certify internal controls for SOX or similar mandates.
D. Identify executives who will manage customer balances and recognize revenue.
Which controls can user A access and manage for the following Control Manager role configuration? See details of perspective trees and control-perspective association below.
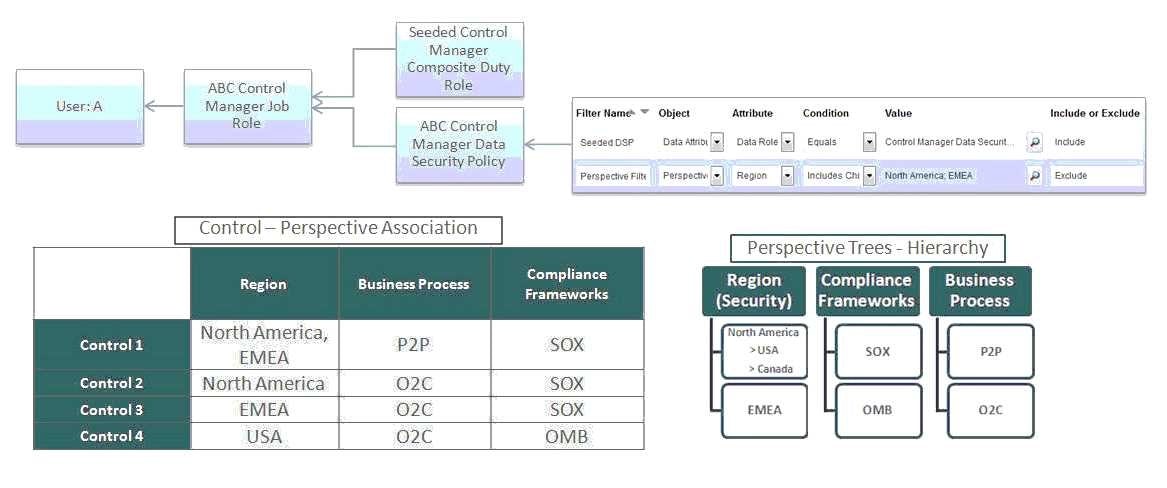
A. None
B. Controls 2 and 3
C. Only Control 1
D. All controls
E. Controls 1, 2, and 3
You have created a risk definition R100 and have created a new control C100 for this risk. No user has been assigned the Risk or Control reviewer and approver roles. What will be the state of R100 and C100 after submitting?
A. Both R100 and C100 will be in the "In Review" state.
B. Both R100 and C100 will be in the "Awaiting Approval" state.
C. Both R100 and C100 will be in the "Approved" state.
D. Both R100 and C100 will be in the "New" state.
You are remediating access incidents in Advanced Access Controls (AAC), and have just completed the remediation of a segregation of duties conflict for users in Fusion Security by removing the conflicting access from the users. What status do you set for the incident in AAC?
A. Resolved
B. Remediation
C. Remedy
D. Authorized
E. Accepted
You are building a transaction model to identify invoices with USD amounts that are greater than the supplier's average invoice amount. The order of the filters is important.
1.
Add an "Average" Function filter grouping by "Supplier ID" where "Invoice Amount" is greater than 0.
2.
Add a standard filter where "Invoice Currency" equals "USD."
3.
Add a standard filter where the delivered "Average Value" attribute is less than "Invoice Amount."
What is the correct order of the filters for this transaction model?
A. 1, 3, 2
B. 1, 2, 3
C. 2, 3, 1
D. 3, 2, 1
E. 2, 1, 3