1V0-81.20 Online Practice Questions and Answers
Refer to the exhibit.
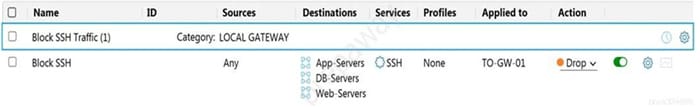
Which statement is true about the firewall rule?
A. It is a gateway firewall applied to a Tier-0 gateway that drops traffic on port 22
B. It is a distributed firewall applied to App-Services, DB-Servers and Web-Servers that rejects traffic on port 22
C. It is a distributed firewall applied to App-Services, DB-Servers and Web-Servers that drops traffic on port 22
D. It is a gateway firewall applied to a Tier-0 gateway that rejects traffic on port 22
Which four alert filters are available in the VMware Carbon Black Cloud Investigate page? (Choose four.)
A. Watchlist
B. Target Value
C. Policy
D. Security Alert List
E. Effective Reputation
F. Alert Severity
What are three core characteristics of VMware's Intrinsic Security solution? (Choose three.)
A. integrated
B. extensible
C. unified
D. content-centric
E. centrally managed
F. built-in
When using VMware Carbon Black Live Response, what command will show all active processes?
A. dir
B. list
C. ls
D. ps
What types of hosts are supported for hosting both NSX-T Data Center managers and host transport nodes?
A. vSphere ESXi 6.7U1 or higher, KVM on CentOS Linux
B. vSphere ESXi 6.7U1 or higher, KVM on RHEL 7.6, Ubuntu 18.04.2 LTS
C. vSphere ESXi 6.5, KVM on RHEL 7.6, Ubuntu 18.04.2 LTS
D. vSphere ESXi 6.7U1 or higher, CentOS KVM 7.6, RHEL KVM
In VMware Carbon Black Cloud Endpoint Standard, which items are available in the Event view?
A. Hashes, Reputations
B. Emails, Policies, OS, Locations
C. Connection, IP/Port
D. IDs, Indicators/TTPs
In Workspace ONE Intelligence, which of the following is a role that can be assigned to an administrator account?
A. Super User
B. Helpdesk
C. Read-only
D. Automater
Least Privilege is a common method for minimizing the risk of what kind of threat?
A. Insider Threats
B. Spear Phishing
C. Distributed Denial of Service
D. Man in the Middle
In a Workspace ONE deployment, Per App Tunnel uses the Native Platform API for which platforms?
A. iOS and Android only
B. iOS, Android, MacOS and Windows
C. iOS and MacOS only
D. Android and Windows only
In VMware Carbon Black Cloud, what is the search field you would use when searching for a command line?
A. command_line:
B. full_cmdline:
C. process_cmdline:
D. process_commandline: