1D0-610 Online Practice Questions and Answers
Which is the preferred approach to communicate important action items in an e-mail message to a co- worker?
A. Write the action items using all capital letters.
B. List the action items in a numbered or bulleted list for clarity.
C. Include emoticons to ensure the recipient understands your humor.
D. Describe all action items at length in a detailed paragraph in the middle of the message.
Which of the following is a security threat commonly associated with cloud-based services?
A. Malware
B. Phishing
C. Hypervisor vulnerabilities
D. Operating system vulnerabilities
You have volunteered to give a presentation to the parents at your child's school about the dangers of the Internet. Which of the following would you include in your recommendations to parents?
A. Warn children to never provide personal information over the Internet.
B. Direct parents to ask other users in the children's chat rooms to provide identification.
C. Remind the parents that the anonymity of chat rooms provides security.
D. To reduce fear, claim that the threat of predators has been reduced in recent times.
Henry is the network manager at XYY Corporation, a large manufacturing company that competes in the global market. The company's computing environment is extremely complex and includes several proprietary software systems, all of which require custom configuration of network devices to operate correctly. The company's executive management team believes that they can benefit by switching the company over to any cloud-based service. Henry disagrees. What is a disadvantage of cloud-based services that Henry can cite to support his position?
A. Cloud-based services provide no maintenance or support.
B. Cloud-based services are typically more costly than in-house solutions.
C. The company must typically purchase additional servers to support connections to these types of cloud-based service providers.
D. Cloud-based services are typically more limited in offerings and configurations than the company currently supports in-house.
Marsha has been hired by XYZ, Inc., to update the company Web site. Marsha discovers that the existing Web pages were structured using tables. Marsha needs to explain to XYZ why the Web site needs to be recoded in HTML5 with CSS controlling the structure of the document. What is the most important reason for using HTML5 and CSS?
A. The updates will increase user traffic to the site.
B. The updates will improve the overall look and feel of the Web site.
C. The Web site can be interpreted by any HTML5-compliant browser, including mobile devices.
D. The Web site will rank higher in many search engines results, as long as the search engine bot recognizes the code.
Which code is best for embedding video into an HTML5 page?
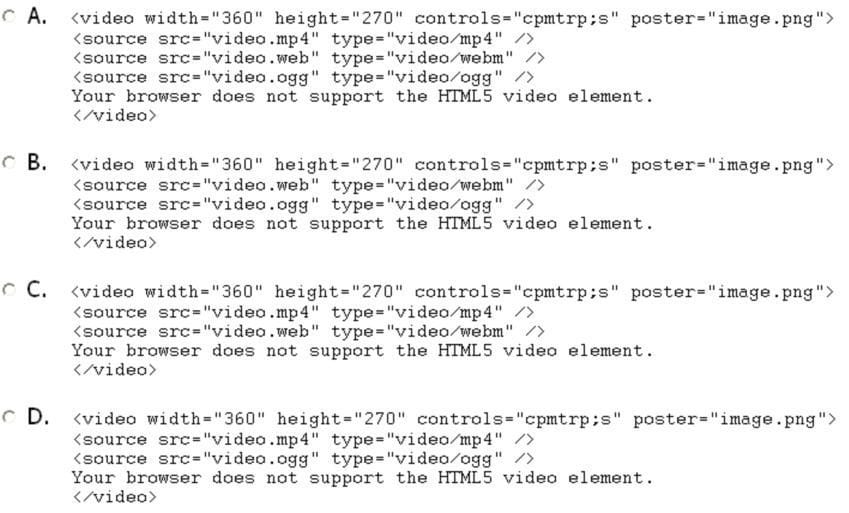
A. Option A
B. Option B
C. Option C
D. Option D
SuperBank is considering a cloud service from Local Data Center, Inc., to support the bank's expanding needs. SuperBank's managers are concerned about security. What can SuperBank request to protect its data from security threats?
A. For Local Data Center to run multiple hypervisors
B. For Local Data Center to install a DDoS mitigation system
C. For SuperBank staff to manage the servers at Local Data Center, Inc.
D. For SuperBank to perform background checks on the staff at Local Data Center, Inc.
Web developers typically include comments in their code for which reason?
A. To insert server-side programs, such as JavaScript
B. To communicate performance issues to site visitors
C. To explain the purpose of code sections to other developers
D. To declare which version of HTML each part of the code is using
What is the distinguishing difference between a LAN and WAN?
A. A LAN is a group of networked computers within a confined geographic area.
B. A WAN is a group of networked computers within a confined geographic area.
C. A LAN typically provides slower network connection speeds than a WAN.
D. A WAN is commonly used for intra-office communication.
Virtualization software transforms the hardware resources of a physical computer to create a fully functional virtual computer that can run its own operating systems and applications. In addition to the CPU and RAM, which hardware resources are used by virtualization software?
A. Hard disk and USB devices
B. Hard disk and network devices
C. Virtual hard disk and network devices
D. Network devices and secondary storage devices