156-215.77 Online Practice Questions and Answers
The third-shift Administrator was updating Security Management Server access settings in Global Properties. He managed to lock all administrators out of their accounts. How should you unlock these accounts?
A. Delete the file admin.lock in the Security Management Server directory $FWDIR/tmp/.
B. Reinstall the Security Management Server and restore using upgrade_import.
C. Type fwm lock_admin -ua from the Security Management Server command line.
D. Login to SmartDashboard as the special cpconfig_admin user account; right-click on each administrator object and select unlock.
Which of the following are authentication methods that Security Gateway R77 uses to validate connection attempts? Select the response below that includes the MOST complete list of valid authentication methods.
A. Proxied, User, Dynamic, Session
B. Connection, User, Client
C. User, Client, Session
D. User, Proxied, Session
Charles requests a Website while using a computer not in the net_singapore network. What is TRUE about his location restriction?
Exhibit: A. Source setting in Source column always takes precedence.
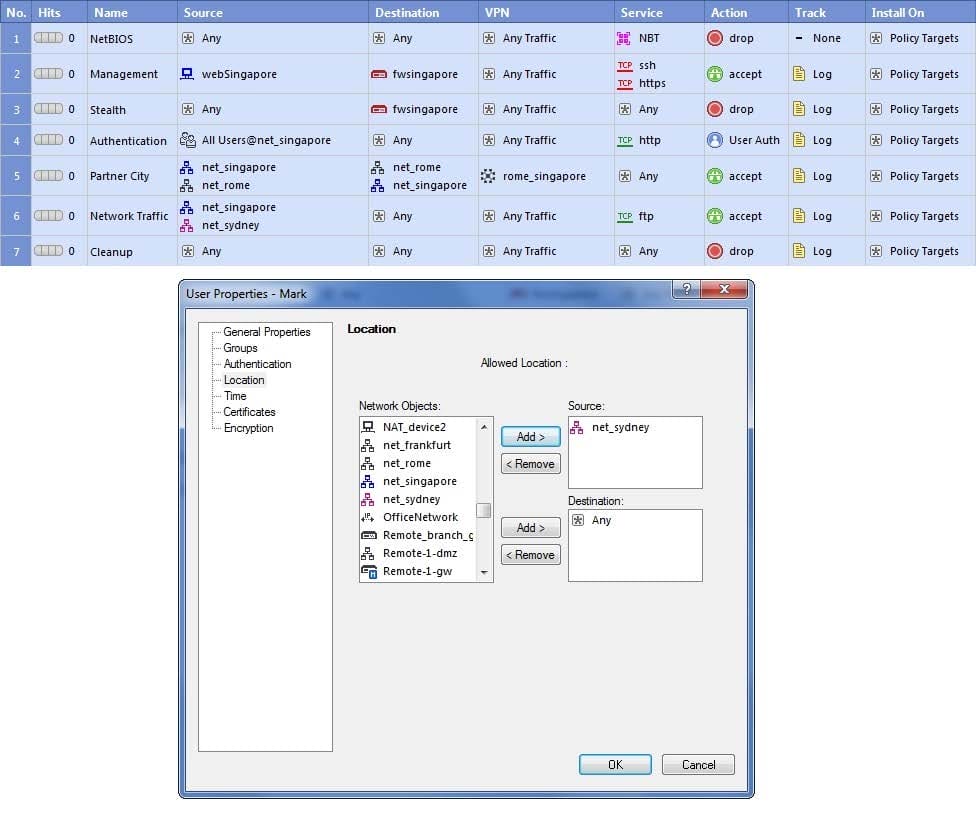
B. Source setting in User Properties always takes precedence.
C. As location restrictions add up, he would be allowed from net_singapore and net_sydney.
D. It depends on how the User Auth object is configured; whether User Properties or Source Restriction takes precedence.
UDP packets are delivered if they are ___________.
A. a stateful ACK to a valid SYN-SYN/ACK on the inverse UDP ports and IP
B. a valid response to an allowed request on the inverse UDP ports and IP
C. bypassing the kernel by the forwarding layer of ClusterXL
D. referenced in the SAM related dynamic tables
Your primary Security Gateway runs on GAiA. What is the easiest way to back up your Security Gateway R77 configuration, including routing and network configuration files?
A. Copying the directories $FWDIR/conf and $FWDIR/lib to another location.
B. Using the native GAiA backup utility from command line or in the Web based user interface.
C. Using the command upgrade_export.
D. Run the pre_upgrade_verifier and save the .tgz file to the directory /temp.
Which of the following statements is TRUE about management plug-ins?
A. A management plug-in interacts with a Security Management Server to provide new features and support for new products.
B. Installing a management plug-in is just like an upgrade process.
C. Using a plug-in offers full central management only if special licensing is applied to specific features of the plug-in.
D. The plug-in is a package installed on the Security Gateway.
You have included the Cleanup Rule in your Rule Base. Where in the Rule Base should the Accept ICMP Requests implied rule have no effect?
A. Last
B. After Stealth Rule
C. First
D. Before Last
Why should the upgrade_export configuration file (.tgz) be deleted after you complete the import process?
A. SmartUpdate will start a new installation process if the machine is rebooted.
B. It will prevent a future successful upgrade_export since the .tgz file cannot be overwritten.
C. It contains your security configuration, which could be exploited.
D. It will conflict with any future upgrades when using SmartUpdate.
Which of the following firewall modes DOES NOT allow for Identity Awareness to be deployed?
A. Bridge
B. Load Sharing
C. High Availability
D. Fail Open
Which rule is responsible for the user authentication failure?
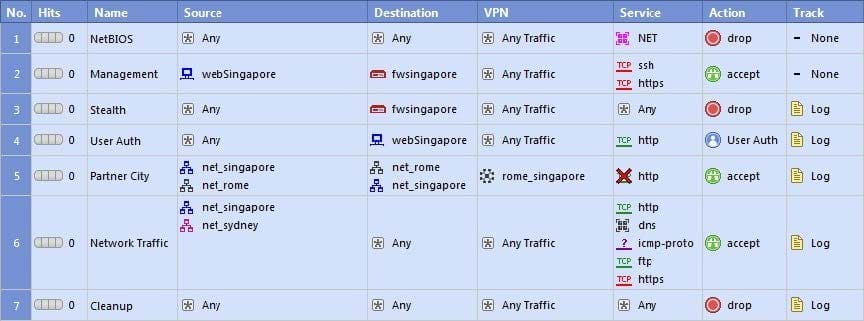
A. Rule 4
B. Rule 6
C. Rule 3
D. Rule 5